What is DNS?
DNS stands for 'Domain Name System', something which is called into action every time you make a request for some sort of information online. DNS servers are sometimes referred to as the phonebooks of the internet because they're basically a large collection of web addresses designed for computers.
Every device which connects to the internet is assigned a unique identifying number known as an Internet Protocol address. This is often referred to as its IP address, or just "IP.” Computers identify websites by their IP addresses.
To address this problem, World Wide Web inventor Tim Berners-Lee also invented the Uniform Resource Locator (URL). This is the easy-to-use "web address” that we are all familiar with.
The Domain Name System (DNS) simply maps URL web addresses to the IP addresses which computers really use to identify the website. So DNS is really just a fancy address book, albeit one that needs to be continually updated and coordinated across the internet.
Every computing device and webpage has an IP address – a unique collection of numbers that pinpoint a specific point in cyberspace such as a device or website.
You can probably see the problem; a long sequence of random digits isn't very memorable. This is not how we remember building addresses, for example – most people can just about remember a small collection of two or three-digit house numbers belonging to their closest friends.
This is where a DNS comes in. A DNS essentially assigns this string of numbers to a web address that is recognizable, memorable, and comprehensible to any human using a computer. The URL – such as www.bbc.com – can be understood by humans, whereas the IP address the DNS links it to works for the machines. When the IP address of some URLs or devices change – not all all devices and websites have static, fixed IP addresses – systems are updated via DDNS (Dynamic DNS) services.
DNS servers try to answer queries themselves, but if they cannot, they contact another in a long hierarchy of DNS servers, one of which will complete the request.
DNS servers
The job of matching URLs to IP addresses (more technically referred to as resolving DNS queries) is performed by DNS servers. These servers also communicate with other DNS servers to ensure that all URL to DNS mappings remain up-to-date.
The software for setting up a DNS server is freely available, allowing anyone with the technical knowledge to create one for themselves. By default, however, your devices will send DNS queries to DNS servers run by your internet provider (ISP).
IPv4 and IPv6
IP addresses come in two versions: The older Internet Protocol version 4 (IPv4), and IPv6. The problem with IPv4 is that the standard only supports a maximum 32-bit internet address, which translates to 2^32 IP addresses available for assignment (about 4.29 billion total). And they are running out.
Although workarounds have been found that extend the shelf-life of IPv4, this will only postpone the inevitable, and IPv4 addresses will run out.
The new IPv6 standard solves this problem simply by allowing a much longer internet address. It utilizes 128-bit web addresses, expanding the maximum available number of web addresses to 2^128. This should keep us supplied with IP addresses for the foreseeable future.
Unfortunately, the adoption of IPv6 by websites has been slow. This is mainly due to upgrade costs, backward capability concerns, and sheer laziness. Consequently, although all modern Operating Systems support IPv6, the vast majority of websites do not yet bother to.
Uptake of IPv6 by ISPs has also been slow, resulting in only around 25 percent of internet users globally having access to IPv6 connections (over 50 percent in the United States).
This has led websites that support IPv6 to adopt a dual-tiered approach. When connected to an address that only supports IPv4, they will serve up an IPv4 address, but when connected from an address that supports IPv6, they will serve up an IPv6 address.
All the DNS services listed below can be connected to using IPv4 and IPv6 addresses and can resolve URLs to both IPv4 and IPv6 addresses.
Why might you want to change DNS server?
For Privacy
The DNS server translates the URL of every website you visit into an IP address. This means that whoever runs the DNS server can always know which websites you have visited. Which usually means your ISP.
In the normal course of events, this is not an issue, since it is your ISP which connects you to these websites anyway.
DNS and VPNs
If you use a VPN to hide your internet activity from your ISP any benefit is undone if DNS requests continue to be handled by your ISP.
Fortunately, this is a fairly rare occurrence these days, as VPN software almost always routes DNS queries through the encrypted VPN tunnel. They can then be privately handled by DNS servers operated by the VPN service.
This means that if you are using a VPN, then you don’t need to change DNS servers manually. In fact, doing so (which we sometimes wrongly see advised) compromises your privacy by sending the DNS request outside the encrypted VPN tunnel and by giving your browsing history to a third party.
Some VPN services don’t run their own DNS servers, but instead, pass the DNS query onto a third-party DNS server run by a DNS service such as Google DNS. Although arguably not as private as resolving the DNS query themselves, this is not a big problem.
All queries appear to come from the VPN server, not the device which actually made them. This is called proxying a DNS request and means that the third party DNS resolver has no idea who makes the initial request.
VPN software should atomically route DNS queries through the VPN tunnel, so no further configuration should be required. If for any reason it doesn’t, then you have a DNS leak.
DNS and proxies
Standard proxy connections, on the other hand, do not affect how DNS requests are handled. So if you want to hide what you get up to on the internet from your ISP when using one, then you will need to manually change the DNS server your device uses.
Even then, although it no longer handles DNS queries itself, your ISP will be able to see DNS requests to a third-party DNS server unless they are encrypted. We will discuss DNS encryption later in this article.
To defeat censorship
A quick and dirty way to censor the internet is DNS spoofing (also called DNS poisoning). All that is required is for a government to instruct domestic ISPs to either not resolve DNS queries or to redirect them to a warning website.
Such censorship can be easily defeated simply by changing by the DNS server your device uses to one located outside the country where content is censored.
This is exactly what happened in Turkey in 2014 when it blocked access to Twitter and Facebook. A number of Turkish newspapers posted details on how to change DNS settings on their websites and Twitter itself tweeted the numbers for the Google DNS servers.

Graffiti in Istanbul, 2014, showing the numbers for Google’s DNS primary and secondary DNS servers
For speed
Some DNS servers are faster than others. This means they can resolve DNS queries more quickly, which in turn improves page load times.
Factors affecting DNS resolution times include the resources available to the server (how powerful it is), how many people are using it any one time, and the distance between you and the server.
In reality, DNS translation is usually so fast, anyway, that you are unlikely to notice any change when switching DNS servers. But it is possible, especially if you can switch to a DNS server which is much closer to you.
The best DNS servers 2024
As already noted, if you use a VPN then you will automaticity use the VPN’s DNS servers (or ones proxied your VPN provider). If using a VPN, then manually changing your DNS settings to those listed below will damage, rather than improve, your privacy.
Although we list primary and secondary DNS server addresses below, most of the DNS services listed actually run hundreds of VPN servers around the world. Connecting to the DNS addresses listed, however, will transparently connect you to a DNS server near to you.
Cloudflare 1.1.1.1
Primary IPV4 DNS server: 1.1.1.1. Secondary IPv4 DNS server: 1.0.0.1
Primary IPv6 DNS server: 2606:4700:4700::1111. Secondary IPv6 DNS server: 2606:4700:4700::1001
Cloudflare is a content delivery network service best known for the DDoS protection service it offers to websites. It now also runs a free public DNS service, and boy is it good! Snappily named 1.1.1.1 after its primary (IPv4) DNS server address, Cloudflare’s DNS service is blindingly fast and is great for privacy.
DNS speed tests consistently places 1.1.1.1 streaks ahead of all other public and ISP-run DNS services (and almost twice as fast as Google DNS).
Unlike many other DNS resolvers, 1.1.1.1 does not provide anti-phishing filters, but it does not log your IP address when you make a query. This means it has no records of your browsing history that can be traced back to you. Which is fantastic, as is the fact that it’s no logs claim is audited on a yearly basis by KPMG.
In addition to this, 1.1.1.1 fully supports the DNS over HTTPS (DoH) and DNS over TLS (DoT) DNS encryption standards. These allow you to encrypt connections using DNSCrypt or Android Pie 9.0+’s new Private DNS mode.
iOS users and owners of older Android phones have nothing to fear, though, as the 1.1.1.1 mobile apps automatically encrypt DNS connections using either DoH or DoT.
OpenNIC
Primary DNS server: varies. Secondary DNS server: varies.
OpenNIC is a non-profit, decentralised, open, uncensored and democratic DNS provider. Designed to take back power from governments and corporations, OpenNIC is run by volunteers and provides a completely unfiltered DNS resolution service, with DNS servers located all across the world.
OpenNIC can resolve all regular ICANN TLDs (Top Level Domains, e.g. .com, .net, .co.uk, .es etc.), and so appears seamless in use.
It has also added a number of its own domains, which can only be accessed if using OpenNIC. These are indy, .geek, .null, .oss, .parody, .bbs, .fur, .free, .ing, .dyn, .gopher, and .micro (plus it cooperatively operates the TLD .glue, which is shared among alternative domain name systems).
Membership in OpenNIC is open to all internet users, and decisions are made either by democratically elected administers or direct vote, with all decisions appealable by a vote of the general membership.
Unlike the other corporate DNS revolvers listed here, each OpenNIC DNS server has its own IP address which must be configured individually. The logging policy, whether a server supports DNSCrypt (many do), and whether a server performs any form of DNS blocking (e.g. spam and phishing protection) is also up to the volunteers who run it.
The OpenNIC website does a good job at clearly showing which servers do what, and at recommending a nearby server for you.
The main downside of OpenNIC is that server performance can vary wildly, with servers regularly going offline. Another issue is trust. That anybody can set up an OpenNIC server is in many ways great, but it does mean that you have no way of knowing if the volunteer running any given server can be trusted.
DNS.Watch
Primary IPv4 DNS server: 84.200.69.80. Secondary IPv4 DNS server: 84.200.70.40
Primary IPv6 DNS server: 2001:1608:10:25::1c04:b12f. Secondary IPv6 DNS server: 2001:1608:10:25::9249:d69b
Like 1.1.1.1, DNS. Watch is a 100% free and uncensored DNS service. Much like OpenNIC, it is run not-for-profit by a group of enthusiasts.
As far as we can tell, the server addresses are for the actual DNS servers, making DNS.Watch a very small operation. The result is that performance is much more consistent than with OpenNIC, but just two servers will never be able to compete in terms of speed with the big boys who operate hundreds of DNS servers located all over the world.
All DNS queries handled by DNS.Watch are protected by DNSSEC. This helps to verify the authenticity of a DNS translation by allowing a domain owner to attach a cryptographic signature to their domain which is verified by DNSSEC. It does not encrypt the translation, however, and so does not provide privacy.
It should be noted that while DNS.Watch makes a big deal of its support for DNSSEC, this feature is fairly standard for DNS services and is usually only worth mentioning when it is absent.
OpenDNS
Primary IPv4 DNS server: 208.67.222.123. Secondary IPv4 DNS server: 208.67.220.220
Primary IPv6 DNS server: 2620:119:35::35. Secondary IPv6 DNS server: 2620:119:53::53
OpenDNS is a commercial DNS service. It offers free services (including basic DNS resolution), but also offers premium home and small business plans. OpenVPN is open about the fact that it keeps logs, and so it is not a service for the seriously privacy-conscious.
What it does do is provide content filtering aimed at improving your online security and/or preventing children from accessing adult material.
OpenDNS Family Shield is a free service which is pre-configured to block adult content. Just set up and forget. OpenDNS Home, also free, allows you to filter web content at levels High to Low, or to customize which categories of content you would like filtered.
If you want to whitelist individual websites within a category, then you will need to upgrade to the premium OpenDNS Home VIP plan for $19.95 per year, which also provides detailed usage stats.
OpenDNS also provides a very fast service, beaten only by 1.1.1.1 on speed as a public DNS resolver.
Quad9 DNS
Primary IPv4 DNS server: 9.9.9.9. Secondary IPv4 DNS server: 149.112.112.112
Primary IPv6 DNS server: 2620:fe::fe, 2620:fe::9. Secondary IPv6 DNS server: 2620:fe::9.
Quad9 is a not-for-profit DNS service which collects no personally identifiable information about its users. Crucially, the IP addresses of users are not stored when making a query. Funding comes from a number of sources, including IBM, Packet Clearing House, The Global Cyber Alliance (GCA), and the City of London Police.
Unlike 1.1.1.1 and DNS.Watch, Quad9 filters malicious websites based on blacklists provided to it by nineteen security intelligence companies, including IBM’s X-Force. In return, it provides these companies with high-level anonymized telemetry and aggregate statistics from its service.
Only websites considered be a security threat are filtered, with no additional censorship performed. Quad9 is a global operation, running DNS servers in 135 locations in over 77 countries. Performance is decent but does not match that of the industry leaders. All servers fully support DNS-over-TLS (DoT) and DNS over HTTPS (DoH).
Are DNS servers secure?
DNS hijacking and DNSSEC
Any computer system which is connected to the internet is potentially vulnerable to hacking, and hijacking DNS servers is a relatively common occurrence. How secure a DNS server is from hackers depends entirely on the barriers put into place by the DNS provider.
When a hacker has gained control of a DNS server, they can simply rewrite the DNS "address book” in order to redirect URLs to malicious domains (such as has fake bank login pages).
In order to address this problem, ICANN, the body which oversees the DNS system, implemented DNS Security Extensions (DNSSEC). This standard helps to verify the authenticity of a DNS translation by allowing a domain owner to attach a cryptographic signature to their domain which is verified by DNSSEC.
The problem with DNSSEC is that it must be implemented (and correctly) at all levels of the process in order to be effective at ensuring against DNS hijacking. Which is sadly not always the case.
If implemented correctly, then DNSSEC ensures that a URL will resolve to the correct IP address. It does not encrypt the translation, however, and so does not provide privacy…
DNS Encryption
Although it no longer handles the DNS requests, your ISP usually can still see DNS queries sent to third party resolvers, as by default they are sent over the internet in plaintext. It probably doesn’t bother to keep a record of these, but it can. And it will certainly comply with any valid legal request to start doing so.
If you are using a DNS service in order to improve your privacy, then you should encrypt DNS requests as they are sent to the DNS resolver. There are now three standards for doing this: DNSCrypt, DNS over HTTPS (DoH) and DNS over TLS (DoT).
Having so many standards might seem a little confusing, but implementation is pretty much seamless as far as the end-user is concerned, and they all do the job of encrypting DNS queries well.
DNSCrypt is the oldest and most established standard. It is basically DoH with some additional bells and whistles aimed at improving regular DoH. Usefully, DNSCrypt-proxy (see below) supports both DNSCrypt and DoH connections.
As already noted, Android Pie 9.0+ supports DoT "out of the box” with its Private DNS Mode.
Various mobile apps such as DNS Manager and the ones from 1.1.1.1 also support one or both encryption standards. Desktop users, on the other hand, have DNSCrypt-proxy.
DNSCrypt-proxy
DNSCrypt-proxy is an open source app that encrypts all DNS queries to servers which support the DNSCrypt or DNS over HTTPS (DoH) protocols.

The base app is available for Windows, macOS, Android, Linux and more, but implementations of it are available which are easier to use than the base app (such as Simple DNSCrypt for Windows), or which support additional platforms (such as DNSCloak for iOS).
VPNs and DNS Encryption
When you use a VPN all DNS queries are sent through the encrypted VPN tunnel to be handled by your VPN provider (who runs its own DNS servers or proxies your query to a public DNS service). The DNS requests are therefore protected by the VPN encryption, so no additional encryption measures (such as DNSCrypt) are required.
DDoS Attacks
DNS services have occasionally been victims of Distributed Denial of Service (DDoS) attacks, which attempt to disrupt the service by overwhelming it with DNS quires. Such attacks may temporarily prevent a DNS service from working, but do not pose any privacy threat to its users. Check out our "what is DDoS" article for more information about this topic.
Primary DNS and Secondary DNS servers
Most DNS services publish four DNS server IP addresses: a primary and a secondary IPv4 address, and a primary and a secondary IPv6 address. Most device’s DNS settings also support both a primary and secondary IPv4 address, although many do not yet support IPv6.
The primary address is exactly that: the IP address of the main DNS server. The secondary address is simply that of a fallback server, which your device will default to if there is a problem with the primary server.
In the normal course of events you don’t really need to input the secondary server address, but is always nice to have a fallback option.
If your device and your ISP both support IPv6 connections then you should configure your device’s setting to connect to both IPv4 and IPv6 primary and a secondary DNS server to ensure IPv6 DNS queries are sent to your chosen DNS provider instead of your ISP.
If either your device or ISP does not support IPv6 then you can safely ignore the IPv6 server settings.
How to change DNS
Please check out A Complete Guide to Changing your DNS Settings for a detailed guide on this subject with step-by-step screenshots. What follows here is the quick summary version.
Windows 10
1. Go to Start -> Settings -> Network & Internet -> Status -> Network and Sharing Center -> Change adapter settings.
2. Right-click on your internet connection -> Properties.
3. Click on (highlight) "Internet Protocol Version 4 (TCP/IPv4)”, then select "Properties”.
4. Ensure the "Use the following DNS server addresses” radio button is checked, and input your new primary DNS server address into the "Preferred DNS server” field and secondary DNS server address into the "Alternative DNS server” field. Click "OK”.
5. If using IPv6 then repeat steps 3 & 4, except for Internet Protocol Version 6 (TCP/IPv6) Properties.
macOS
1. Go to System Preferences -> Network -> [your internet connection] -> Advanced -> DNS tab.
2. Use the "-" symbol to remove existing servers and the "+” symbol to add new servers. macOS will preference servers from top to bottom of this list, so if you are using IPv6 then order IPv6 server addresses to the top. When you are done, click "OK”.
Linux (Ubuntu)
1. Go to Settings -> Network [your internet connection] -> gear icon -> IPv4 tab.
2. Enter the primary and secondary IPv4 DNS server addresses in the DNS field, separated by a coma. Click Apply.
3. If using IPv6 then click on the IPv6 tab, and repeat except using the supplied IPv6 server addresses.
Android
Android Pie 9.0+ supports DoT encrypted connections via its Private DNS Mode.
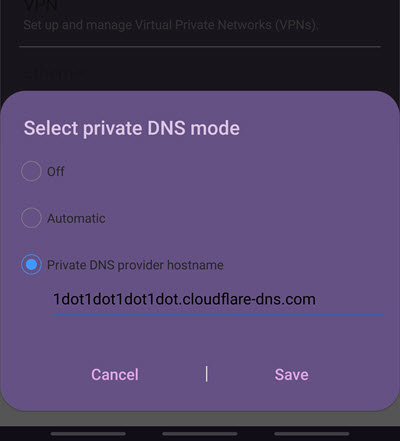
1. Go to Settings -> Connections -> More connections -> Private DNS.
2. Fill in the Private DNS provider hostname supplied by your DNS service. Note that this is not a regular primary or secondary DNS server IP address. The Private DNS hostname for 1.1.1.1, for example, is 1dot1dot1dot1dot.claudflare-dns.com.
Owners of older devices, or who wish to use more conventional DNS server settings (for example because their DNS service does not support DoT encryption), need to use an app. Unfortunately, the open-source DNSCrypt for Android is not easy to install at the moment, so you may be better off using commercial alternatives such as DNS Manager or DNS Switch. Alternatively, the 1.1.1.1 app is free.
iOS
iPhone and iPad users can download the DNSCloak (a implementation of DNSCrypt-proxy) and 1.1.1.1 apps from the App Store.
What is Dynamic DNS (DDNS or DynDNS)?
ISPs usually assign residential IP addresses dynamically via DHCP. That is, they are handed out as needed and can change at random. Business connections are usually assigned a static IP address that never changes (which is, in fact, one of the major advantages of paying extra for a business account).
Much like regular DNS, Dynamic DNS (also known as DDNS or DynDNS) is a way of mapping URLs to their IP address. The difference is that if the target IP address changes, Dynamic DNS will instantly update its address book and send visitors to the correct new IP address.
Dynamic DNS is therefore particularly useful for people who host online resources such as FTP or games servers from their residential home address. It allows them to create and hand out a URL that can be used to reach the resource, no matter if its IP address is changed by their ISP.
In order to use dynamic DNS you must sign-up to a dynamic DNS service, which will manage your domain’s DNS connections for you.
DNS server issues
There are three main concerns when using a DNS service: whether it works, how fast it is, and whether it provides any privacy.
As already discussed, most DNS services (including ISPs) issue a secondary IP address (for both IPv4 and IPv6 if supported) as a fallback in case of problems with the primary address.
With a small service, this might literary be the IP address of a single backup server. With larger services that run hundreds of DNS servers around the world, the situation is undoubtedly much more complex, but the idea remains the same in principle.
The chances of both addresses failing are very low, although DNS services have been deliberately targeted by Denial of Service (DoS) attacks in the past aimed at causing disruption to their service.
Slow DNS lookup times increase page load times, and so are a popular reason to switch to third-party DNS services. At the time of writing this article, Cloudflare’s 1.1.1.1 is streaks ahead of its competition in the speed department.
When it comes to privacy, by default your ISP knows everything you do on the internet. Changing to a more privacy-focused DNS service improves the situation somewhat, but does nothing to stop your ISP from seeing what you get up to on the internet.
For this you need to use a VPN service, which encrypts your data (including DNS requests), performs the DNS translation (like a regular third-party DNS service), and proxies your internet connection so that your ISP can’t see which websites you connect to – only that you have connected to an IP address belonging to a VPN company.
If you are interested in changing your DNS service away from your ISP in order to improve privacy, you therefor much better using a good VPN service instead.
Image credit: @kadikoybaska.
