Improving your online security and privacy is not easy. Governments everywhere are keen to track your every online move, allegedly for "security purposes,” while private companies want to know as much about you as they can in order to target you with ever more personalized ads.
This guide to online privacy cannot hope to protect you from all online threats, and following the advice here should not be allowed to foster in you a false sense of security. Vigilance is always required. But it provides concrete steps that everyone can use to prove their online security and privacy - even novices!
Understanding online security
Knowledge is power, and the more you know about how what things can affect your online security, the more you can do to protect yourself online. We cover some topics you should know about below.
The importance of Open Source Software
Open source software is software that allows anyone to access it's source code. This is important as it can be audited to ensure the software is secure and private.
Most software is written and developed by commercial companies. Understandably, these companies are keen not to have others steal their hard work or trade secrets, so they hide the code away from prying eyes using encryption.
As we say, this is all quite understandable, but it presents a major problem regarding security. If no-one can "see” the details of what a program does, how can we know that it is doing what it's supposed to do? Basically, we can’t, so we simply have to trust the company involved, which is something us paranoid security types are loath to do (with good reason).
The best answer to this problem lies in open-source software - community-developed software, where the code is freely available for other programmers to look at, modify, or use for their own purposes.
In an ideal world, all open source software would be fully audited to ensure it contains no major weaknesses and is not doing anything untoward. But given the complex nature of most programs and the lack of experts with the time to audit the software (usually for free), this is something of a pipe dream.
Even the fact that open source can be audited by anyone who cares to do so, though, gives us a higher degree of confidence in its integrity than is possible for any closed source product.
So while open source is not a perfect solution to a very knotty problem, it is the only solution there is.
End-to-end encryption
Encryption is complex math used to ensure that data cannot be accessed by anyone who is not intended to access it. This is great, but is only part of the story. Just as important is what exactly is encrypted, and where.
A great example of the problem is Google’s Gmail email service. When you send an email using Gmail, it is secured in transit using HTTPS - the main kind of encryption used to secure data as it is transferred over the web.
Emails don’t just get delivered, though. They are stored on Google’s servers so you can access them in the future. Google encrypts this data while it is sitting on its servers ("at rest”) to ensure that hackers and unauthorized people can’t access it.
This is great, but it is Google who encrypts this data, so Google can decrypt it - and does. Although it no longer scans your emails in order to target ads at you, Google routinely scans your emails to detect spam, offer canned response suggestions, add travel times to your Google Calendar, and suchlike. And if Google can read your data, then it can also hand that data over to your government.
The solution to this problem is end-to-end encryption (e2ee). With e2ee you encrypt your data on your own device before sending it anywhere, and it can only be decrypted by yourself or an intended recipient.
In other words, there is no need to trust a third party to encrypt and decrypt your data for you.
Smartphones
Smartphones may be the defining technology of our era, but they are a privacy nightmare. This subject really needs an entire guide of its own (which we may publish at some point), but some key points to bear in mind include:
- Phones can track your movements with scary accuracy, even when GPS is turned off. If you want to keep your movements private, then the safest thing is to leave your phone at home.
- Google and Apple collect a great deal of metadata information about you from apps downloaded from their Stores. Google is definitely the worst offender in this regard, but this is balanced somewhat by the fact that you can sideload APK files or download apps from third party stores such as F-Droid.
- Apps tend to send a lot of data back to their developers. You can improve your privacy by interacting with online services via their web pages instead of their apps, although it's becoming increasingly common for services to force the use of apps.
- Android apps can ask for more invasive permissions than iOS apps, but more recent versions of Android allow you to disable many of these at a granular level once the app is stalled. Whichever platform you use, it's a good idea to check app permissions to ensure you are happy with them.
- Most Android and all iPhones are e2e encrypted these days, but data backed up to iCloud, Google Drive, or your phone manufacturer’s default cloud service of choice, is not. Disable any such auto-backup functions on your phone and use NextCloud (discussed later) instead.
Private/Incognito mode
Almost all modern browsers offer a "private” or ‘‘incognito” mode. Often referred to as "porn mode,” the purpose and scope of this feature is often dangerously misunderstood.
It prevents your browser from caching web pages you have visited and from adding what you do to your browser's History feature. It is, therefore, great for hiding what you get up to online from others who have physical access to your computer, such as family members or work colleagues.
What it doesn’t do is hide what you get up to on the internet from outside observers such as your ISP. For that, you need a VPN or Tor. We discuss these later in this guide, so read on or follow the links to skip to those sections.
Unless otherwise stated, all software and services recommended in this article are free, open source, and available for all major platforms (Windows, macOS, Linux, Android, and iOS). If you are using a Chromebook, we have section for Chromebook users at the end of this guide.
Tools that will improve your online security
There are several practical changes you can make to improve your online security and privacy. We suggest the best tools for doing so below.
Use Firefox browser
Although Brave is an up-and-coming contender, we think Mozilla Firefox is the best private browser around. It is open source and includes a wealth of anti-tracking features. Particularly impressive is Firefox’s Containers feature, which can isolate websites inside their own browser tab so they can’t track what you do in other tabs.
In all other respects, Firefox is a fully featured browser that can go head-to-head with commercial closed-source rivals such as Chrome and Safari. It had a reputation for being slower than its rivals, but following a major rewrite of its code in 2019 (dubbed "Quantum”), this is no longer an issue.
One of the best things about Firefox is that it supports a huge range of add-ons, including many that can improve your privacy further. We recommend using at least Privacy Badger and uBlock Origin (together).
For more information, plus some other things you can do to "tighten up” Firefox’s privacy settings further, please see our Firefox privacy and security guide.
Thanks to Apple’s strict developer guidelines, Firefox for iOS is not as fully featured as it is on other platforms. We still recommend it for day-to-day use, but suggest switching to Firefox Focus for your more sensitive browsing needs.
Use Bitwarden password manager
You need a password manager in your life. Simply put, improving the strength of your passwords is the single most important thing that you can do to improve your online security.
Truly secure passwords are long, use a mix of numbers, mixed capitalized letters, and weird symbols like ^%$#@!. Remembering just one password like this is all but impossible for us poor meatsacks, let alone a unique one for each and every online service that you use!
Luckily, our computers can do the heavy lifting for us in the form of password managers. All you need do is remember a single password (or better yet, a passphrase comprised of a number of words), and they will generate secure passwords, remember them, and autofill them into web forms and the like for you.
Using pretty much any password manager will greatly improve your online security, but we like open source end-to-end encrypted Bitwarden. It's a free password manager that is fully featured and ridiculously easy to use - even for total beginners. If you want some alternatives, check out our best password managers page.
Use DuckDuckGo search engine
Google exists by knowing as much as it can about you and then using that information to target you with highly personalized ads.
What you search for tells Google an awful lot about you, including your political beliefs and allegiances, religious leanings (or lack of them), social circles, hobbies, sexual preferences, and much more.
DuckDuckGo, on the other hand, is a private search engine that vows to not track you. Some people complain that it’s anonymised Yahoo-based search results are not as good as those from Google, but we have always found them to be excellent.
It's easy to set DuckDuckGo as your default search engine, it looks good, and it's ease of use make it a fantastic alternative to Google search.
Use secure email services
Despite its continued popularity, email is a desperately outdated communications system that was never designed to be secure.
This already dire situation was made worse when, spearheaded by Google's Gmail service, large commercial tech firms started to offer "free” at the point of use email services which they monetized by invading your privacy (and which subsequently betrayed their users to the NSA).
When it comes to privacy, email should be regarded as fundamentally broken. Given its day-to-day prevalence , however, dumping it altogether is not a practical option.
Fortunately, several secure, secure email services that are as easy to use as the likes of Gmail, Outlook, and Apple Mail, have appeared over the past few years. ProtonMail and Tutanota are arguably most prominent of these, but other good options exist.
What these services have in common is that they offer end-to-end encryption, so that the services have no ability to read emails stored on their servers. This is great, but when you send an email to someone else, then their email service will be able to read it and will store it on their own servers.
This is not a problem, of course, if ProtonMail and Tutanota users send emails to other users of the same service. Both services have also developed ways to send non-users emails that are fully e2e encrypted, no matter which email service the recipient uses.
ProtonMail uses the fiddly-but-widely-supported PGP protocol to achieve this, while Tutanota uses its own much easier system. Both services offer good free plans, which are supported by premium plans.
Use Signal messenger
Services such as ProtonMail and Tutanota make email as secure and private as it's possible to get, but email will never be as secure as a system that was built from the ground up to be secure by one of the world’s most renown cryptographers.
And traditional SMS messaging on your phone is arguably even worse! SMS messages are completely unencrypted and can be readily scanned by your mobile provider.
Desktop versions now exist, but Signal is mainly an end-to-end messenger app (now with audio and video chat support) that replaces the stock messenger app that comes with your phone.
You can send and receive regular insecure SMS messages from non-users, but messages sent between Signal users are secured using the strongest encryption system yet devised for human communications.
Other services, such as Facebook Messenger, WhatsApp, and Skype, now use the Signal protocol to provide users with end-to-end encryption. But unlike these services, the Signal app itself collects almost no metadata and uses fully audited open source code.
An issue that bothers some people is that, in order to seamlessly replace your phone's SMS messenger, Signal identifies users by their phone numbers. It is therefore secure, but not anonymous. As already noted, though, Signal keeps almost no metadata relating to its users, so we do not consider this a major issue.
There are several other alternatives to Signal messenger, check out our Best secure private messengers article for a list of these.
Use Linux

We understand that switching to a new operating system may be a step too far for many "beginner” readers, but it is one that everyone should seriously consider if they are concerned enough about privacy to read this guide.
Linux is a desktop operating system that can replace Windows or macOS on your existing hardware. Unlike those operating systems (especially Windows), it is free, open source, and built from the ground up with security and privacy in mind. All of these things make it the best alternative to Windows or Mac OS.
Enthusiasts insist that Linux is as easy (if not easier) to use than its commercial rivals, but we think most people migrating from Windows or macOS will find the learning curve quite steep. It is worth persevering, however, as it is a great platform, and is the only real option if you want to step up your privacy game.
Linux comes in a bewildering number of flavors (called distros) but we endorse the usual recommendation that Ubuntu LTS (which uses Mac-like desktop) or Mint (which uses a Windows-like desktop) are the best places to start. If you want to learn more about these, take a look at our most secure Linux distros.
If you just want to dip your toe into Linux waters, then LiveDVD/LiveUSB distros allow you to try the OS out without installing them. Another good option is to create a Linux Virtual Machine using Oracle VirtualBox.
It's also easy to dual-boot Linux with your existing OS for easy migration, an option particularly favored by Windows gamers!
Use a no-logs VPN service
A Virtual Private Network (VPN) connects your device to a VPN server run by a commercial VPN service. This connection is securely encrypted. This setup might sound simple, but it means that:
- Your internet provider (ISP) doesn't know what you get up to on the internet. It can't see your data because it's encrypted, and it can’t see which websites you visit the VPN server sits between it and what you get up to on the internet.
- And what your ISP doesn’t know, neither does your government (probably) since all mass surveillance schemes rely on ISPs handing their data over to the government.
- Websites can’t see your real, unique internet (IP) address. All they see is the VPN address of the VPN server.
VPNs are also useful for stuff like torrenting safely, changing Netflix region so you can watch more content, evading censorship, and more, but we won’t go into that here.
An important thing to be aware of is that the encrypted VPN tunnel only extends from your device to the VPN server. This means that your ISP can’t see what you get up to on the internet, but the VPN service can.
Unlike ISPs, most good VPN services these days mitigate against the privacy issues this raises by having robust no-log VPN policies regarding the data they (don’t) collect. This is great, but it should always be remembered that VPN providers can be forced to start logging at any time if enough pressure is applied.
Most VPN software is not open source, but as a VPN provider can see what you get up to on the internet, anyway, we consider worrying about this point rather pointless. It also costs a lot of money to run a VPN service, so most free VPN services shouldn't be trusted.
Read our best VPNs in 2020 page for a list of services that will keep you secure online, while also enabling you to unblock content unavailable in your location.
Use Tor (if you really need to)
A VPN will hugely improve your online privacy with minimal impact to your day-to-day internet experience. But at the end of the day, it requires a level of trust in your VPN service.
If you need true anonymity on the internet, then use the Tor Network instead. This routes your internet connection through at least three volunteer-run Tor "nodes,” encrypting your data each time. The entry node can see who you are, but not what you do on the internet, while the exit node can see what you do on the internet, but not who you are.
Anonymity on the internet is impossible to 100% guarantee, but Tor is as close as it gets. So if you are a whistleblower or political dissident whose life or liberty depends on maintaining your anonymity, then use Tor.
Tor, though, is very slow. It breaks many websites and is generally a pain in the butt to use. So if you are not a whistleblower or a political dissident, then use a VPN instead. The usual way to access Tor is via Tor Browser.
Use Nextcloud cloud storage
None of the big-name cloud storage services - Google Drive, Dropbox, Apple iCloud, Microsoft OneDrive, etc., employ end-to-end encryption. This means they can access your data (and by this point we shouldn’t need to point out that almost all of them have cooperated with the NSA to betray their customers in the past).
Nextcloud is an incredibly fully featured open source cloud storage platform that you can self-host for maximum privacy and security. Beginners will be pleased to know, however, that there are easier ways to use Nextcloud! A multitude of smaller cloud hosting services leverage the Nextcloud platform, making it ridiculously easy to set up and use.
By relying on a third party to host and manage your Nextcloud account, you relinquish some control over your data, but this can be heavily mitigated against by enabling end-to-end encryption (that is, you encrypt your files on your device before uploading them to the cloud)..
E2ee is not offered by all Nextcloud hosts - so check before signing up to a particular Nextcloud provider. Most Nextcloud providers offer a free plan, but e2e encryption is invariably only available to Premium users.
See our best cloud storage article for a list of several alternatives to Nextcloud.
Use HTTPS websites
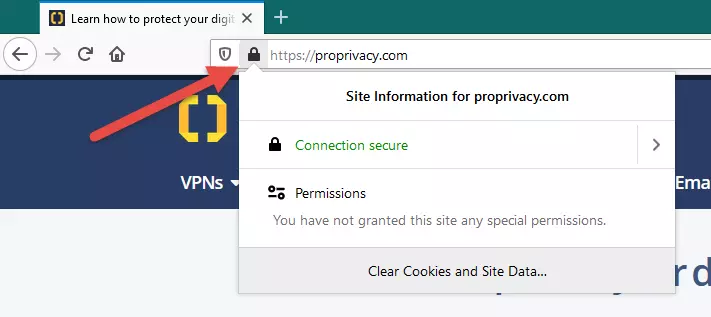
HTTPS is the encryption protocol that secures the internet. When you visit an HTTPS-protected website no-one except the website owner can see what you do on that website.
Your ISP can see that you have visited a particular website (or your VPN provider if you are using a VPN), but they can’t see which pages you visit on that site, or any details (like payment details) that you enter web forms. Without HTTPS, internet commerce would be impossible.
You don't need to do anything to use HTTPS - the magic happens automatically when you visit HTTPS websites. But what you can do is ensure that websites you visit use HTTPS by looking for a closed padlock icon in your browser’s URL bar. Assuming it's there, you can find out additional details by clicking on the icon.
If you see an open padlock, then the site is not secure and you might want to consider leaving. If you see an open padlock on a page that is asking you to enter sensitive information (such as payment details) then run away very fast!
Use Norton or AVG antivirus software
We don’t think it necessary to spill a lot of digital ink explaining that malware exists, is bad, and you don't want it on our devices.
Macs, iPhones, and iPads, are traditionally much less vulnerable to malware than Windows and Android devices, but to a large extent this is simply down to the fact that the overwhelming numbers of Windows and Android devices in use make them the most bountiful target for criminals.
The simple existence of malware for macOS, however, means that we strongly recommend Mac users install anti-malware software. We also feel that Apple’s insistence on banning anti-malware apps from the App Store, despite the existence of malware for iOS, shows a worrying disregard for its users’ security.
On all other platforms we feel that Norton 360’s comprehensive suite of security features offers fantastic value for money, while AVG AntiVirus Free does a good job at covering your basic antivirus needs.
Unfortunately, no antivirus product that we can recommend is open source. This is because the resources and expertize needed to assess the continually evolving threats faced by all computer users requires the kind of resources that are only available to commercial companies.
And at the end of the day, the threat posed by using closed source anti-malware software is considerably less than the threat posed by insufficient protections against malware. For some alternatives to Norton 360, check out our best antivirus software page.
Final thoughts
Whew! We did say at the beginning that maintaining privacy and security on the internet was not easy!
However, if you have read through this guide, then you should have a good idea of the scale of the challenge we face and the need to meet that challenge head on. This is not just for our own sake, but as part of a united effort to make the internet the free, open, and democratic hub of innovation it has the potential to be.
We cannot guarantee our privacy or security on the internet, but by following the advice in the guide, thinking about the issues raised, and then acting appropriately, we can greatly improve it and make the lives of those who threaten these basic human and civil rights much more difficult.
Notes for Chromebook users
Most recommendations in this guide can be used by Chromebook owners without additional comment. The following points are worth noting, though:
- As a Chromebook user, you have pretty tied your flag to the Google mast. That said, Firefox for Android works fine in Chrome OS, although there are some limitations based on it being mainly designed for small touch screens. Firefox for Linux also works brilliantly on machines that support Linux and have the processing hefty to handle full desktop apps.
- Besides an Android app, a Bitwarden extension is available through the Chrome Web Store.
- The easiest way to use a VPN on a Chromebook is via an Android app. Please see How to Install a VPN on Chromebook for a detailed look at this subject.
- Tor browser is available for Android and Linux.
- If you install the NextCloud Android app, then your Nextcloud server will be mounted in Files.
- Antivirus software is not required for regular Chrome OS, although you should probably install an Android antivirus app if you use Android apps a lot.
