Are you a Linux user on the hunt for a VPN? If so, you'll probably already know exactly why you need a VPN – and that there are generally two types of VPN client available to Linux users; command line and GUI. Unfortunately, not every VPN service out there is compatible with Linux, so we've put together a list of the best providers for the job.
All of our suggestions have been thoroughly tested, work with Linux's most popular distros, and can be counted on to keep your digital life private – so let's jump right in.
The best VPNs for Linux at a glance
If you're in a rush to check out our top VPN picks for Linux, check out the table below:
- Surfshark - The best overall Linux VPN. Strong on privacy, with an intuitive Linux app, unlimited simultaneous connections, and lots of features.
- Private Internet Access - The best cheap VPN for Linux. It offers dedicated clients for Ubuntu, Mint, Arch, and Debian, and a 30-day money-back guarantee.
- Proton VPN - The best secure VPN for Linux. Offers IPv6 and DNS leak protection alongside a kill-switch and sleek apps.
- AirVPN - The best advanced VPN for Linux. Includes a Linux GUI client with all the features, as well as Tor compatibility.
- Mullvad - The best anonymous VPN for Linux. With a full toolset of features, Linux GUI, and strong encryption.
Searching for a reliable VPN is a daunting task at the best of times – and Linux users have the additional obstacle of finding a service that's actually compatible with Linux systems. Most VPN providers simply don't offer support for Linux, and this has a knock-on effect on the availability of VPN features that users on other platforms take for granted.
So, that's why we've focused on the best Linux VPN apps currently available. These apps install quickly, come with a complete security toolset, and include a full GUI wherever possible.
All of our Linux VPN recommendations offer the following key features:
- A Linux GUI
- Robust encryption
- Versatile privacy measures
- A global server network
- Consistent, and impressive, speeds
10 Best Linux VPN clients: In-depth analysis
If you want to secure your Linux device, as well as your online browsing sessions, then we'd recommend checking out any of the VPNs on the list below.
Surfshark is the best overall VPN for Linux. Slick GUI, unlimited simultaneous connections, and a 30-day money-back guarantee. Surfshark Demo If you're familiar with VPNs, you've probably heard of Surfshark - a relatively young service that constantly receives rave reviews from customers. I like that Surfshark is compatible with most platforms, including Linux, and is incredibly easy to use. You won't need to be a tech expert in order to make the most of this VPN. Surfshark recently introduced a brand new Linux VPN app - complete with a stylish GUI! This is a fantastic step up from the previous command-line-only app, and far more intuitive for users. In addition to a sleek-feeling interface (ideal for Linux newbies who aren't as comfortable punching commands), the GUI update comes with a number of features that were already available to users on different operating systems. Now, Linux loyalists will be able to enjoy tools like MultiHop, CleanWeb ad-blocking, the speedy WireGuard protocol, and extended leak protection. It's a hefty update that brings Surfshark's Linux offering into 2024 - and there's even more to come, as the provider has promised support for auto-connect and kill-switch tools in the near future. Currently, the new Surfshark Linux app is available for Ubuntu 20.04 LTS, Debian 11, Mint 20, though other distros are expected to be supported soon. Surfshark is also a zero-logs provider that allows its users to enjoy unlimited simultaneous connections! This means you can use it on your Linux computer, and your mobile devices, work computers, and anything else you might own. Surfshark has servers in over 100 countries
and it permits torrenting throughout its network. It is also one of the few services that can unblock various Netflix libraries (including Netflix US), BBC iPlayer, Amazon Prime Video, Disney+, and other popular streaming services from around the globe. We are always impressed by the level of service you get with Surfshark's 24/7 live chat support. There is no doubt that you're getting incredible value for your money when you sign up with Surfshark. Well worth comparing to our other recommendations using its 30-day money-back guarantee. Private Internet Access is a budget-friendly VPN for Linux with dedicated clients for Ubuntu, Mint, Arch, and Debian. Packed with features and with a 30-day money-back guarantee. PIA Demo Private Internet Access (PIA) is a secure and reliable VPN that is ideal for Linux users. It has a full, custom 64-bit (only) client for Linux that is compatible with Ubuntu, Mint, Arch, and Debian. In addition, PIA has told us it is working on support for other distros too, so watch this space! PIA's custom Linux client is downloaded as a .run file which you then install from the install directory using the command: Perhaps surprisingly, the Linux version does everything that PIA’s other desktop apps do, including having a kill-switch, "PIA Mace" (DNS advert and malware blocking), and fine-grained control over the OpenVPN encryption settings. This makes it by far the best GUI Linux client available on the market. And a subscription is extremely cheap, which makes this service an extremely good proposition. What's more, PIA is known for its strong no-logs policy, which it has proven in court on more than one occasion. Plus, this service will be compatible with your other devices (iOS, Android, macOS, etc) and it allows you to use it on up to Unlimited
devices at once – with just a single subscription. You can test it on Linux – and any other devices you own – for 30 days, thanks to its money-back guarantee. ProtonVPN is the best secure VPN for Linux. Offers a full-featured GUI client for Linux users and tough encryption, alongside a 30-day money-back guarantee. Proton Demo ProtonVPN brings both a sleek GUI client and a full suite of features to Linux users. ProtonVPN's Linux client includes IPv6 and DNS leak protection, a kill-switch, support for torrenting and the ability to unblock the libraries of most of the big streaming providers around the world, including Disney+, Amazon, Netflix and more. With servers in 91 countries
, Proton is a fast service with solid encryption and innovative features to keep users secure. While not the cheapest provider around, it offers a 7-day trial of its premium service, a free tier (which restricts which countries you can connect to), and a 30-day money-back guarantee on all of its paid-for subscriptions. AirVPN is the best advanced VPN for Linux. A "techie focused" service with a great "Eddie" GUI client, encryption, and 30-day money-back guarantee. AirVPN Demo AirVPN is great for Linux users thanks to its strong reputation for respecting user privacy and for implementing the technology needed to protect it. Unfortunately, this is something of a double-edged sword, as AirVPN's techie focus can make it difficult for beginners. We doubt this is a problem for Linux users, though, who should rejoice at the fact that AirVPN's excellent open-source "Eddie" VPN client provides the full GUI Linux VPN client experience in Linux. This means the Linux client is fully-featured and includes a kill-switch, full IPv4 and IPv6 leak protection, and is effective at mitigating against WebRTC leaks. Eddie allows Linux users to connect to its VPN servers via the Tor network for true anonymity, and to hide their VPN connections inside an SSH or SSL tunnel (stunnel) in order to defeat VPN censorship. Port forwarding is available via the web interface. Eddie is available pre-compiled for a Debian, OpenSUSE, Fedora, and ArchLinux. A Tarball is also available for re-compiling on any Linux platform. AirVPN keeps no logs at all (they are sent to a dev/null file), allows up to five simultaneous devices, offers a 1-day free trial on request, and allows torrenting on all servers. Mulvad is the best anonymous VPN for Linux. It has a VPN GUI for Linux users with all the features you get on Windows and Mac, and a 30-day money-back guarantee. Mullvad is a no-logs VPN service based in Sweden, which, like AirVPN, has a very strong privacy and technology focus. Hell, it even accepts anonymous payment in cash sent to it by post! It also offers a full open-source GUI Linux VPN client with all the bells and whistles available to users of other platforms. These features include full DNS protection (with proper IPv6 support, which is very rare), a kill-switch, and port forwarding. VPN through Tor is supported through manual configuration. Debian (DEB) and Fedora (RPM) install files are available from the Mullvad website, while the full code with build instructions is available from its GitHub page. Mullvad allows up to 5
devices to connect at once and offers servers located all around the world. It also offers consistently good speeds, which will make engaging in data-intensive tasks a breeze. ExpressVPN is the best premium VPN for Linux. Can be used via command line client or browser extension, and offers users a 30-day money-back guarantee. ExpressVPN Demo ExpressVPN is an excellent no-logs VPN service, based in the British Virgin Islands. It's a top-shelf VPN provider that continues to set standards in the industry, and was a significant driving force behind many other VPN providers adopting a 24/7 approach to customer support. Express offers super-fast servers that operate in RAM only! On top of this, ExpressVPN also published its own proprietary VPN protocol, Lightway, that offers faster and more secure VPN encryption for its users. Despite being a command-line-only VPN for Linux, it's a solid VPN with great functionality. It is available for Ubuntu, Debian, CentOS, Fedora, Arch, and Raspbian, although its source is not available to compile yourself. Give it a try with a 30-day money-back guarantee to fall back on. TorGuard is the best torrenting VPN for Linux. With a great GUI Linux app and kill-switch, and a 7-day money-back guarantee. TorGuard is a no-logs VPN provider based in the US. It offers a global network of fast and secure bare-metal servers that are great for torrenting as well as for unblocking geo-restricted content from around the world. With its fully-featured GUI for Linux, you get great customization with the VPN. Defaulting to OpenVPN in UDP mode, you can switch to TCP mode, and even Cisco OpenConnect (/AnyConnect). With OpenVPN, you can also choose from a selection of ports to use (for example, OpenVPN TCP port 443 for obfuscation), or you can use stunnel to hide the VPN connections inside a TLS/SSL tunnel. The GUI also has an advanced kill-switch function that lets you disconnect from the internet and even terminate specific programs if the VPN fails. Try TorGuard today with a 7-day free trial and support for Ubuntu, Debian, RedHat, Fedora, CentOS, and Arch. NordVPN is the best all-rounder VPN for Linux. Controlled via a CLI, with excellent encryption and easy setup, and a 30-day money-back guarantee. Nord Demo NordVPN is a large no-logs VPN service is based in privacy-friendly Panama. It has a strong consumer-facing focus and is known for its 24/7 live chat support, 30-day money-back guarantee, and its ability to unblock popular streaming services such as US Netflix and BBC iPlayer. A free full Smart DNS is included in the startling-low entry price. NordVPN offers a simple command-line OpenVPN tool that comes pre-configured for NordVPN's server locations, including NordVPN's obfuscated XOR servers. It allows you to switch easily between UDP and TCP connections, which can be useful for evading VPN censorship measures. Its autofill feature also makes life easier. The app is available to download as a DEB or RPM package, although the CLI setup instructions assume Debian. NordVPN allows you to connect up to six devices at once, offers 24/7 live chat support, and will refund your money up to 30-days after payment. VPNArea is the best easy-to-use VPN for Linux. With a clean and clear GUI and advanced features, as well as a 30-day money-back guarantee. VPNArea Demo VPNArea is a provider from Bulgaria that has apps for all platforms, this includes a Linux GUI that will work on various distros. The VPN has servers in over 55 countries
, and that entire Tier-1 network is more than capable of providing fast enough connection speeds for streaming and gaming online without the hassle of buffering or lag. With VPNArea, you can unblock many of the most sought-after streaming services from around the world, like Netflix US, BBC iPlayer, Hulu, Prime Video, and much more. And if you have any problems, you can always contact its friendly 24/7 live chat support agents. Where privacy is concerned, this VPN is outstanding thanks to its no-logs policy and strong OpenVPN encryption. It also has a kill-switch, DNS leak protection, and obfuscation. This makes it great for doing sensitive tasks like torrenting that require complete privacy. We are always impressed by this VPN, and because of its relatively low cost, we consider this a superb option for anybody who needs a VPN for Linux. Well worth testing using its money-back guarantee. CyberGhost is the best value VPN for Linux. Available via a CLI and a solid option for the security-conscious, with a 45-day money-back guarantee. CyberGhost Demo CyberGhost is a well-known name in the VPN sphere – and it is a service that does everything right. Its latest software (CyberGhost 8) is super to use and offers a wealth of awesome features for gaining privacy both at home and on public Wi-Fi. In this CyberGhost VPN review, we have taken an in-depth look at the security features, speed and performance, and the apps for each platform. We found it to be a versatile service that is able to unblock highly desirable streaming services like Netflix US and BBC iPlayer. Overall, we consider CyberGhost to be a superb service that offers outstanding value-for-money. Read on to find out why we think it is worth splashing out on this amazing-value VPN. 1. Surfshark
Pricing
Pros
Cons
Linux client (GUI)
Built-in kill switch
Server locations
Website

Pricing
Pros
Cons
Linux client (GUI)
Built-in kill switch
Server locations
Website

sh pia-linux-2.2.1-05193.run
Pricing
Pros
Cons
Linux client (GUI)
Built-in kill switch
Server locations
Pricing
Pros
Cons
Linux client (GUI)
Built-in kill switch
Server locations
Website

5. Mullvad

Pricing
Pros
Cons
Linux client (GUI)
Built-in kill switch
Server locations

Pricing
Pros
Cons
Linux client (GUI)
Built-in kill switch
Server locations
Website

Pricing
Pros
Cons
Linux client (GUI)
Built-in kill switch
Server locations

Pricing
Pros
Cons
Linux client (GUI)
Built-in kill switch
Server locations
Website

9. VPNArea
 www.vpnarea.com
www.vpnarea.com
Pricing
Pros
Cons
Linux client (GUI)
Built-in kill switch
Server locations

Pricing
Pros
Cons
Server locations
Website

How to install a VPN on Linux
We've put together a guide on how to install a VPN on a Linux device. It's easy to follow, regardless of whether you're a Linux newbie or just need a refresher, and primarily focuses on the Debian/Ubuntu distros. However, we hope to expand it to include other Linux branches in the near future.
The advantages of using a VPN on Linux?
Most Linux users are already well aware of the privacy issues associated with using the internet. Linux itself is typically known to be much more secure than other, more mainstream operating systems, and certain distros are already being geared towards protecting user privacy. Using a VPN, then, is the next logical step for Linux users who want to keep their online privacy watertight.
A VPN ensures that all the traffic leaving your Linux machine is fully encrypted before it passes over the local network and through your ISP's gateway servers. This will effectively prevent anyone from tracking what you are doing online and keep your data safely out of the reach of any potential eavesdroppers.
To find out more about what a VPN is, follow the link. Below, we have included a list that outlines what VPNs can do thanks to the encrypted connection they furnish:
- A VPN prevents your ISP from tracking what you do online by acting as your personal proxy. When connected to a VPN, all your ISP will be able to see is that you have connected to the VPN's IP address- not what you're actually doing on the internet.
- Your ISP also won't be able to see the contents of your data because it is encrypted between your PC and the VPN server.
- Given that every government mass surveillance project in the world relies on ISPs logging your data to know what you get up to online, what your ISP doesn't know, neither will your government (unless it is actively investigating you as an individual, of course).
- The proxy works both ways, so websites you visit can't see your real IP address. They only see the IP address of the VPN server you are connecting through. Note that websites also use other sneaky ways to follow you online, so a VPN should always be supplemented with anti-tracking browser add-ons.
- Like websites, P2P torrent peers also won't be able to see your real IP address, allowing you to torrent with peace of mind.
- VPNs are great for defeating censorship, be it on political, "moral", or copyright grounds. Simply connect to a VPN server located in a region that doesn't censor the internet!
- Because VPN servers can be located all over the world, they're great for unblocking geo-restricted content. VPNs are particularly useful for unblocking BBC iPlayer and US Netflix (which has a much bigger catalog than what is generally available to paying customers in other parts of the world). Check out VPN for Netflix guide for more information about unblocking this service.
- Using a VPN protects against Wi-Fi hackers and unreliable Wi-Fi hosts when using public Wi-Fi hotspots, since all data between your PC and the VPN server is securely encrypted.
So if you use Linux, then we think you should also use a VPN!
What is a custom Linux VPN client?
Linux is Linux, so any Linux VPN app can be re-compiled from its source code (usually in Tarball form) to work on any Linux platform.
Most VPN providers, however, also make their apps available as executable DEB files for Debian (Ubuntu/Mint/etc.) users and RPM files for Red Hat (Fedora, RHEL, CentOS/etc.) users. Some may even offer install packages in Snaps or Flatpack format.
However, it's fair to say that installing and using a VPN client (whether GUI or CLI) works pretty much exactly the same as any other Linux app on your system.
Features offered by custom Linux VPN clients
Using a VPN on Linux can be difficult, and that's because few VPN providers offer full Graphic User Interface (GUI) apps. Instead, they'll focus on developing apps for more mainstream platforms like Windows and macOS.
The good news is that there are a few VPNs available on the market that have guides for setting up their VPN using CLI. On top of that, a growing number of VPN providers are also now providing a GUI client as well.
The VPNs we recommend in this article all have Linux compatibility, whether that be via manual setup or using a full client. All of our recommendations have full, user-friendly guides for setting up the VPN, which means that you can easily get the VPN going on your Linux machine, regardless of which provider you choose.
Please bear in mind, however, that if you do opt for a VPN without a GUI client, you may not have access to certain key VPN features when setting up the VPN connection manually. Below, we've listed a few features that will typically only be available with a full GUI client:
-
DNS leak protection
In theory, any VPN client will route all DNS requests through the VPN tunnel to be resolved either by the VPN provider itself or be proxied by the VPN provider to a public DNS service in order to hide their originator.
But for a variety of reasons, Linux can sometimes route DNS requests directly to the OS-default DNS services (usually your ISP), thus bypassing the VPN's DNS resolution. VPN clients with DNS leak protection guard against this by using firewall rules to ensure no connections are possible outside the VPN tunnel (IPv6 connections are usually just disabled).
Manual VPN setup in Linux, whether using NetworkManager, the CLI OpenVPN client, StrongSwan, or a similar alternative, provides no DNS leak protection. Fortunately, there are steps you can take to fix this issue, although they complicate the VPN setup process.
You can modify resolvconf to push DNS to your VPN's DNS servers, or you can manually configure the iptables firewall to ensure all traffic (including DNS requests) cannot leave your Linux machine outside the VPN tunnel. An excellent guide to doing this is available from IVPN.
-
WebRTC mitigation
Most modern browsers support WebRTC, a communication protocol that allows seamless VoIP and video chat between users inside the browser window.
A feature of WebRTC is that it allows communication through firewalls – but this is a problem for VPN users, seeing as it allows any website to request your real IP address and WebRTC STUN servers will just give it to them! This completely bypasses one of the main privacy protections offered by a VPN.
Many custom VPN clients help mitigate against WebRTC leaks by tightening up VPN settings and using firewall rules, although this is never as secure as preventing WebRTC leaks at the browser level. Fortunately for manual Linux VPN users, disabling WebRTC in the browser is easy.
-
Kill-switch
A kill-switch ensures that your true IP address is not exposed in the event of a VPN dropout, during network switches, and suchlike. Nowadays, most custom VPN clients use firewall rules to ensure no connection is possible when the VPN tunnel is inactive for any reason.
You won't get this protection with a manual VPN setup method, however. As mentioned above, configuring iptables will also work as a kill-switch.
For more information on DNS leaks, WebRTC leaks, and kill-switches, please see A Complete Guide to IP Leak Protection.
Get Linux VPN to start on boot?
We may cover this subject ourselves in the future, but, for the time being, excellent guides for doing this with OpenVPN are available on the smarthome beginner and IVPN websites.
Different ways to use a VPN on Linux
Now that we've covered what you can expect from your Linux VPN, and some of our top recommendations, let's take a look at some different ways to use a VPN on a Linux device.
Use a custom Linux CLI clients
An increasing number of VPN services now offer custom Linux command-line interface (CLI) clients. These are invariably wrappers to the open-source OpenVPN CLI client. As such, they don't usually offer any advanced features, although ExpressVPN's client does feature DNS leak protection.
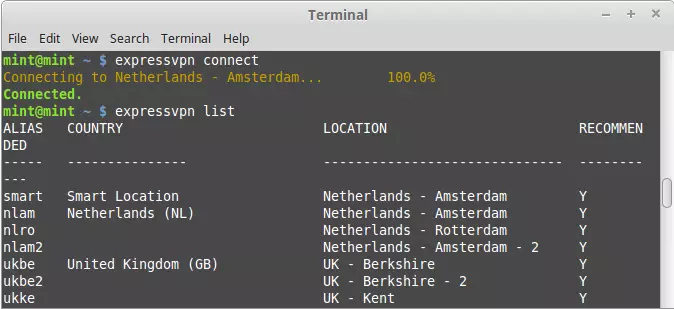
They do, however, make life easier, as they come pre-configured to use that services' VPN servers.
Use a custom Linux VPN GUI clients
To get the full VPN functionality that users of custom Windows and macOS clients enjoy, however, requires a full custom GUI Linux client. Only a few of which exist on the market at the time of writing – those from Private Internet Access, AirVPN, Mullvad, Proton VPN and TorGuard.
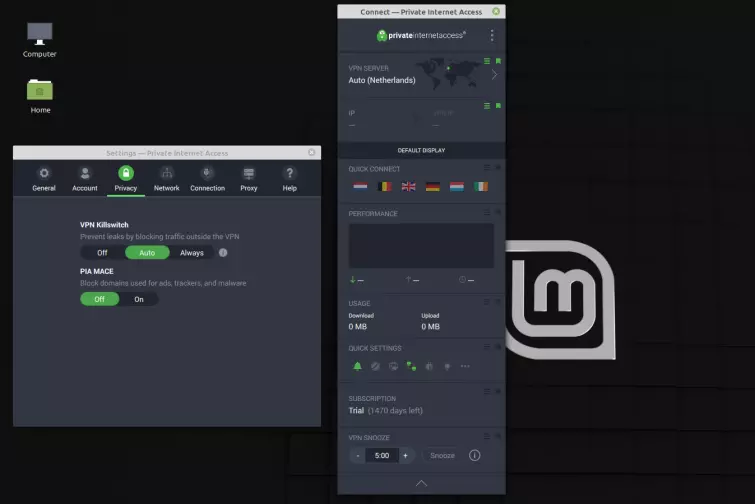
These providers' GUI VPN clients are effectively identical to their Windows and macOS counterparts and offer the same features, including full DNS leak protection, WebRTC mitigation, kill-switches, and other bells and whistles unique to each provider.
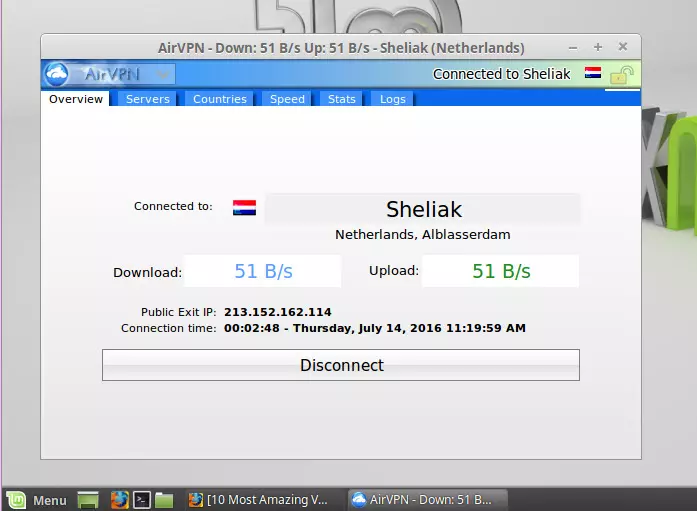
On top of offering additional functionality, most people find that GUI clients are much more user-friendly, thanks in large part to the visual prompts they provide. You do, after all, need to be a seasoned Linux user to not flinch when faced with a blinking command prompt in Terminal!
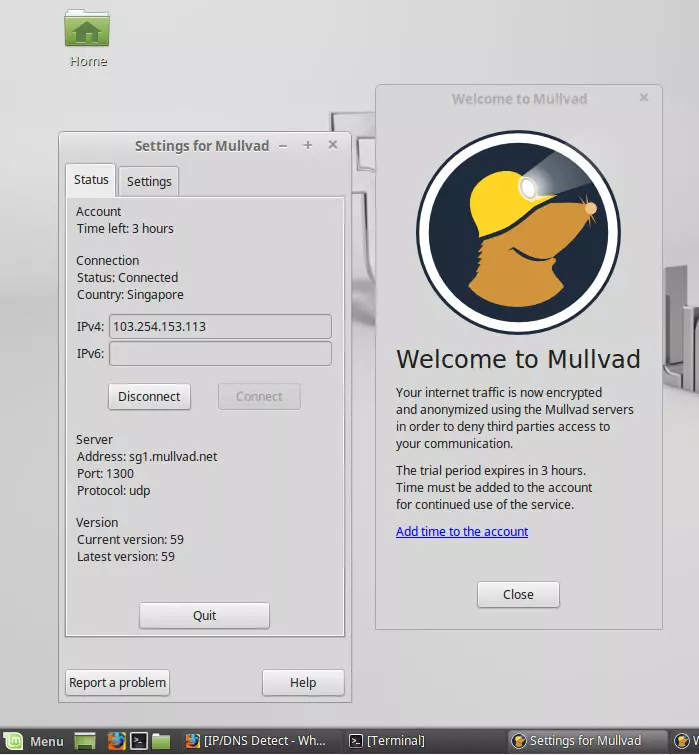
Using NetworkManager as a Linux VPN GUI
Many Linux distros, including most Debian flavors, use NetworkManager as a GUI interface to manage their network connections. Even with distros that don't (such as Raspbian), it is usually possible to manually install NetworkManager.
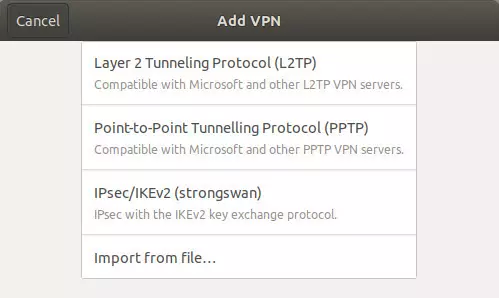
NetworkManager provides an easy-to-use graphical interface for managing your VPN connections. Out-of-the-box, it usually only supports the PPTP VPN protocol, but plugins are available for OpenVPN, L2TP/IPsec, and IKEv2 (using strongSwan). As we've already noted, however, this type of setup does not provide any DNS leak protection or a kill-switch.
It is worth noting that AirVPN recommends against using NetworkManager "due to multiple, critical problems". We have not been able to ascertain what these are, though, and most VPNs are happy to provide setup guides using NetworkManager.
The command-line
With this being Linux, it's only natural that you can set up and run a VPN from the command line! The exact commands will depend on the specific distro you're using, but apps like OpenVPN will work well in any Linux environment.
As we have discussed, you will also need to configure iptables to enjoy a truly secure VPN experience.
Using a VPN for different Linux distros
Ubuntu is by far the most popular desktop version of Linux. It is, therefore, widely regarded by both developers and casual users as the "default" version of Linux. VPN services are no different, and most of the Linux VPN support out there revolves heavily around Ubuntu users.

You're no doubt used to this if you use a different version of Linux. If you're a Debian, Mint, Kali, or any other Debian-based user, most Ubuntu guides (and DEB packages) should be useable on your distro of choice. Unfortunately, you're often on your own if you use an entirely different version of Linux.
Can I get a free VPN for Linux?
Unfortunately, very few VPNs offer a free service compatible with Linux. The good news is that two market-leading services have a limited free plan that is available to Linux users!
Both Proton VPN and Windscribe offer command-line OpenVPN Linux tools.
Proton VPN provides guidance on installing its CLI Linux VPN tool on Ubuntu, Archlinux, Manjaro, Solus, and Fedora, while Windscribe not only supports Ubuntu, Debian, Fedora, and CentOS, but also different versions of its tool optimized for different versions of each distro.
For more information on free VPNs (and why you need to take care when picking one), please head over to our Free VPN guide.
Is WireGuard a good option for Linux users?
The WireGuard VPN protocol has been heaped with praise ever since its inception – and for good reason. Developed by Jason Donenfeld, WireGuard incorporates stealth and typically provides faster tunneling speeds than other protocols, which is a win/win for users.
So, it's encouraging to see more and more VPN providers offer WireGuard connections! You'll be able to use it in place of the OpenVPN or IKEv2 protocols and, if you're particularly untrusting of custom VPN apps, you can also use WireGuard to connect to your VPN's servers, seeing as its connection is made via the third-party WireGuard client.
It should be noted, however, that your data will still pass through the VPN's servers – and that you'll need to trust the VPN to handle that data. This is always going to be the case when using a VPN provider. Fortunately, sticking with one of our recommended zero-log VPNs can minimize the risk of interference.
It is also worth noting that WireGuard is still extremely new, and the protocol is not as proven in the wild as something like OpenVPN, which has been audited countless times. That said, the cryptographic primitives that make up the WireGuard protocol are well known and are considered extremely robust.
Why use Linux?
Many people moved over to Linux from other operating systems to take advantage of its added security. The majority of viruses target mainstream operating systems like Windows and macOS, which means that using Linux can keep you much safer from these, and similar, threats. Other users made the switch away from Windows and Mac because of the privacy ramifications associated with the high levels of surveillance capitalism these companies are known to engage in.
Whether you opt for Ubuntu, Fedora, Kali, Mint, OpenSUSE, or another Linux distribution, you'll gain the advantage of having greater control over your device and the data that it controls. This is a considerable benefit to your privacy, as Apple and Microsoft have previously been found to be working alongside NSA to snoop on users.
Even years after Edward Snowden blew the whistle on the NSA, plenty of credible evidence and rumors persist concerning the implementation of NSA backdoors in Windows and macOS/iOS devices.
Although using Linux is generally a positive step towards increasing your digital privacy, it is important to understand that the OS itself will not be able to protect any of the data that leaves your device and travels over the internet. To protect that data, you must encrypt it before it travels over the local network and onto the internet – which is where a VPN comes into play.
Using a VPN to encrypt your web traffic – to prevent it from being harvested by your ISP, local network administrators, and the government – is an absolute must.
It's not just about this serious stuff, either! A Linux VPN will give you the power to bypass geo-restrictions while protecting privacy online. It will let you unblock Netflix or watch BBC iPlayer from anywhere in the world, and with the right VPN you can torrent in safety.
Linux is more secure than Windows do I still need a VPN?
Yes. Although Linux operating systems are far less vulnerable to hacking and malware, they still require a VPN for online privacy purposes. When a Linux machine connects to the internet it behaves the same way as a Windows, Mac, Android, or iOS device.
The data leaving your Linux machine passes over the local network to the router, and then onto the internet - where it passes through the ISP's gateway servers - on its way to the website you selected in your browser.
This process means that the local network administrator and ISP can track which websites you are using. In some countries, this web browsing data must also be retained due to Mandatory Data Retention directives. As a result, your web data can also be accessed by government agencies.
A VPN encrypts your data on your device before it travels over the internet. This encryption prevents anybody on the local network and your ISP from knowing which websites you are using. It also protects your communications metadata from being monitored.
This VPN encryption not only prevents ISPs and government agencies from snooping on you, but also helps to protect you on public wifi by preventing your data from being intercepted by hackers, and by securing you against the threat of Evil Twin Attacks.
The reasons above make it vital to use a VPN on your Linux machine, as this is the only way to protect your online habits from being tracked and used for profiling purposes.
In addition, the tunnel provided by a VPN conceals your home IP address from websites and services, including other users when you torrent.
This massively increases your privacy by preventing websites from knowing where you are. And by concealing your IP address from other internet users who could potentially be hackers looking for ways to probe your network for vulnerabilities.
Conclusion
Although plenty of VPNs offer some level of Linux compatibility, it is rare for a VPN to offer the same level of service as you would enjoy on its Windows or macOS client. If you want to get the most out of your VPN for Linux, then getting one with a custom GUI for your distro is the best place to start. Here's a quick reminder of our top VPNs for Linux:

From $5.50/month
The best anonymous VPN for Linux. With a full toolset of features, Linux GUI, and strong encryption.
- ProPrivacy TrustScore:
- 9.6 out of 10
- Simultaneous connections
- 5
- Server locations
- 36
- Free trial
- No
FAQs
If you still have questions – don't worry! We've put together an FAQ section that covers the most common questions related to Linux VPN services.








