 This is the ultimate guide to Bitcoin Privacy. Learn how to buy bitcoins anonymously and securely! How to spend it without worrying, and more! Of course, we'll show you how to buy a VPN anonymously, however, the same process can be used to purchase pretty much any product that accepts Bitcoins anonymously. Do note, however, that physical products need to be delivered to a physical address and/or be collected in person. This is an updated version of a guide I originally published on this website back in 2013. Since then, many things have changed. The value of Bitcoin has shot through the roof, well-known trading websites such as Mt. Gox have closed down, and much more. In some places, you can now even buy Bitcoins from ATM machines!
This is the ultimate guide to Bitcoin Privacy. Learn how to buy bitcoins anonymously and securely! How to spend it without worrying, and more! Of course, we'll show you how to buy a VPN anonymously, however, the same process can be used to purchase pretty much any product that accepts Bitcoins anonymously. Do note, however, that physical products need to be delivered to a physical address and/or be collected in person. This is an updated version of a guide I originally published on this website back in 2013. Since then, many things have changed. The value of Bitcoin has shot through the roof, well-known trading websites such as Mt. Gox have closed down, and much more. In some places, you can now even buy Bitcoins from ATM machines!
What Is Bitcoin?
Bitcoin is the original cryptocurrency. It is a decentralized and open-source virtual currency that operates using peer-to-peer (P2P) technology (much as BitTorrent and Skype do). Like traditional money, you can trade Bitcoin for goods or services (such as a VPN subscription) and exchange it for other currencies. Unlike traditional currencies, however, there is no "middleman,” such as a state-controlled bank.
What is Bitcoin? (v2)

Bitcoins are instead generated using a free computer program, at a predictable rate determined by the amount of processing power dedicated to their generation. This process is known as Bitcoin mining. In theory, anyone can do it. A Bitcoin is not a physical thing; it is a cryptographic algorithm consisting of a public key and private key. Some vendors do sell physical notes and coins denominated in Bitcoin, but what they are really selling is a private key (usually protected by a seal which you must break) together with a public key that you can use to verify the balance.
Bitcoin Mining
In practice, Bitcoin mining requires a large amount of processing power - so much so that mining is impractical for most individuals. However, it is possible to join a Bitcoin mining pool (or similar organization) to help spread the costs (and rewards). The prohibitive cost of Bitcoin mining is in part responsible for the current craze for mining alternative cryptocurrencies such as Ethereum, which has a much lower entry point than mining for Bitcoins. Bitcoin mining is not the focus of this article, but if you are interested in the subject then there is an excellent article here. You may also be interested in our Ethereum Mining Guide.
Other Cryptocurrencies
 Since the release of Bitcoin in 2009, numerous other virtual cryptocurrencies have been developed. Many of these have features that offer distinct advantages over Bitcoin (including being more anonymous). None of these alternatives, however, have achieved anything near the popularity of Bitcoin. This limits their real-world usefulness when you want to buy things.
Since the release of Bitcoin in 2009, numerous other virtual cryptocurrencies have been developed. Many of these have features that offer distinct advantages over Bitcoin (including being more anonymous). None of these alternatives, however, have achieved anything near the popularity of Bitcoin. This limits their real-world usefulness when you want to buy things.
Bitcoin And Anonymity
There are two sides to the Bitcoin when it comes to anonymity. The first thing to stress is that Bitcoin is not inherently anonymous. However, it can be made so (at least to a high degree). Please always bear in mind that 100% anonymity can never be guaranteed. Central to the concept of Bitcoin is the blockchain. This is basically a public ledger that records Bitcoin transactions. Transactions in the form payer X sends Y bitcoins to payee Z are broadcast to the Bitcoin network for all the world to see. Thus, from this perspective, Bitcoin is much less anonymous than, say, good old cash. As Sergio Lerner, CEO of Argentinian company Certimix, notes, "Privacy is not enforced by the Bitcoin protocol design. If you re-use the same address over and over to receive money from other users, then every one of them will detect that the others have sent you money." It is possible to purchase Bitcoins and hold a Bitcoin address without revealing your true identity. This only provides a form of pseudonymity, though. Interested parties can use advanced data analysis techniques to look for patterns to de-anonymize users. Such wide-scale and sophisticated data analysis is Google and Facebook’s entire business model. However… You can use Bitcoin mixing techniques to further confuse who did what with Bitcoins. By randomly switching the ownership of Bitcoins, such techniques make de-anonymization via data analysis very hard to achieve. If you purchase and hold them without revealing your identity, and then properly mix them, Bitcoins can afford a high level of anonymity when performing transactions. I discuss ways to mix Bitcoins later in this guide. To more fully understand how Bitcoin and the blockchain works, The ultimate, 3500-word, plain English guide to blockchain by Mohit Mamoria is a fantastic introduction, as is our own Blockchain Explained guide.
The Bitcoin Cash Hard Fork
 Because nothing is ever easy, on 1 August 2017 Bitcoin split into two derivative currencies: Bitcoin Classic (BTC or XBT) and Bitcoin Cash (BCH or BCC). This split is known as the Bitcoin Cash hard fork and the reasons are highly technical.
Because nothing is ever easy, on 1 August 2017 Bitcoin split into two derivative currencies: Bitcoin Classic (BTC or XBT) and Bitcoin Cash (BCH or BCC). This split is known as the Bitcoin Cash hard fork and the reasons are highly technical.
BTC Vs. BCH
If you had any Bitcoin in your wallet and have possession of the private keys, then you are now also entitled to claim an equal number of Bitcoin Cash coins. Thus, if on 1 August 2017 you had a wallet with one Bitcoin in it, you still have that Bitcoin and can now also claim one Bitcoin Cash coin (BCH). If you are just starting with Bitcoins, then you'll need to decide between purchasing Bitcoin Classic or Bitcoin Cash. Some points to bear in mind are:
- Bitcoin Classic is much better established and far more vendors accept it as a form of payment.
- Most Bitcoin wallets and many exchanges don't accept Bitcoin Cash.
- However, Bitcoin Cash allows for more transactions per second. This translates to faster payments and lower fees.
- 1,500 more blocks were mined on the Bitcoin Cash chain than on the original one.
- The market price for Bitcoin Cash has fluctuated wildly over the last month, but in general, it has seen steady growth.
As already noted, this article was written just one month after the hard fork. It will be interesting to see how the situation develops. For the purpose of this article, I will assume regular Bitcoin (Classic) is used. However, while there may be big differences between the currencies from an investment viewpoint (on which I am not qualified to comment), there is almost no difference in the front-end of how they are used. Indeed, they are based on the same code. As such, you can expect to see more Bitcoin Cash versions of existing Bitcoin software going forward, as tweaking code for the new currency is almost trivially easy.
Your Anonymous Bitcoin Wallet
In order to do anything with Bitcoin, you need a Bitcoin wallet. This is software that stores your Bitcoin and allows you to receive and send (that is, pay for stuff with) Bitcoins. As with most things Bitcoin, there is an almost overwhelming number of options available.
Types Of Bitcoin Wallets
The first thing to do is decide whether you want a mobile, web or desktop wallet. Each sort has its own advantages and disadvantages. The main types are:
- Desktop wallet – the most secure option, giving you complete control over your wallet. It also means that you are solely responsible for backing up and securing your wallet.
- Mobile wallet – very handy, as you can carry it in your pocket and use it to pay for things in stores or exchange funds in person. If you lose your phone, however, say goodbye to your Bitcoin!
- Web wallet – certainly the most convenient type of wallet, as you can access it from just about anywhere. Web wallets are also the least secure kind of wallet, as they are held on a server by a third party. This means that you have to trust the website hosting your wallet not to abscond with your money. In addition, problems with the server, or the company suddenly closing down, may result in loss of money. You should therefore never use pure web wallets to store large amounts of money.
Hardware wallets designed to store your Bitcoins offline, and physical wallets (basically a printout of kind of your private keys), also exist. A recommended tactic is to store large savings as securely as possible (preferably offline), while keeping a small amount of Bitcoin in an anonymous bitcoin wallet for performing transactions.
Wallet Options
Disclaimer!
I and BestVPN.com cannot take any responsibility for the security or honesty of any software, website or service listed in this guide. I've tried to list only popular and reputable options, but I have no way of knowing if an app has malicious code built into it, or if the admins of a website will suddenly decide to abscond with your Bitcoin savings. This is, in fact, pretty much precisely what happened to Mt. Gox, which once handled over 70% of all Bitcoin transactions worldwide. So please be careful.
Choosing A Wallet
Choosing a(n anonymous) Bitcoin Wallet is an important decision and one that you should research thoroughly. There is no such thing as the perfect Bitcoin wallet – they all have their pros and cons. A good place to start is bitcoin.org, which provides a good list of options. Whichever wallet you choose, it is a very good idea to securely encrypt and make regular backups of it.
Enter Electrum
I have chosen Electrum as my wallet for this guide. It is free, decentralized, and open-source. I like the fact that it gives me full control over my money and fees. It also offers two-factor authentication (2FA) to help prevent theft of my Bitcoin. Although the code for Electrum is open-source, I still need to trust that its developers don’t update the code with something nasty and that it remains an anonymous Bitcoin wallet for me to use. The alternative would be to opt for a wallet such as Armory, which uses full node validation (Bitcoin Core) to validate and relay transactions on the Bitcoin network. Bitcoin Core is very secure but requires 145GB of space on my drive. If I was storing a large amount of Bitcoin, I would use a Bitcoin Core Wallet. However, as I only need a small amount of Bitcoin to buy a VPN service, I consider this to be overkill.

Here is my new Electrum Bitcoin wallet. If you're feeling generous, you can always send some Bitcoin to me using the address shown above! A major downside with Electrum is that it discloses information to a third party. It uses central servers that can associate your payments together and log your IP address. If you're bothered about the central server connecting your payments together (which won't be logged to your real IP anyway), you can mitigate this by creating a new wallet every time you perform a transaction. You can also take advantage of Electrum’s Tor functionality to hide your real IP address from a central server. (I have opted to connect to a single .onion server for maximum privacy.) Electrum is available for Windows, macOS, Linux and Android, but it is not available as a web wallet. Reviews for the Android version of Electrum in the Play Store are disappointing, so I will stick with the Windows version. If this was purely for personal use, I would use the Linux version. However, Windows has a much wider audience in terms of those reading this guide. A good introduction to installing and configuring Electrum on Windows is available here. A good beginners’ guide to using Electrum is available here. When downloading any wallet from the internet, be sure to verify its digital signature.
How to Buy Bitcoins Anonymously
There are many ways to buy Bitcoin anonymously. These vary depending on which country you're in. It is therefore probably best to search online for options available in your area. How to Buy Bitcoins provides an excellent list of resources for almost every country. Ideally, you want to buy Bitcoins as anonymously as possible so it cannot be traced to your real-world identity. Broadly speaking, there are three main approaches you can take. In rough order of anonymity, from lowest to highest:
1. Buy Then Mix
This is not the most anonymous method of buying Bitcoins, but it is the most convenient. It does nevertheless ensure a fairly high degree of anonymity. Using this method, you do not actually buy Bitcoin anonymously at all. You simply purchase it from an automated Bitcoin exchange such as CoinBase. To make the Bitcoin more anonymous, you then launder it using a "mixer” service. A mixer service basically anonymizes your Bitcoin by swapping it for other Bitcoin that has no connection to you. This makes it very difficult to follow the chain back to you. Difficult, but not impossible. Bitcoin laundry services are, of course, not free. Almost all automatic exchanges require you to prove your real-world identity. In this case, it is easy to determine that you've purchased Bitcoin, but not what happens to it after it has been mixed. I will look at mixing Bitcoin later in this guide. You can also mix Bitcoin that has been bought more anonymously in order to further increase its anonymity.
2. Buy Online From A Seller
Websites such LocalBitcoins.com or the #bitcoin-otc IRC chatroom on Freenode (otc = over-the -counter) allow you to meet private Bitcoin sellers online. You can buy Bitcoin anonymously in this way without registering your real name anywhere. As the seller is a private individual, tracing the transaction is much more difficult than if it was done through a big, centralized exchange where everything is recorded.  #bitcoin-otc uses a fairly involved feedback system. It is well worth taking the time to understand this. You'll need to hash out the payment method with the seller. A list of IRC clients is here. Private sellers may accept all sorts of payment methods – up to and including meeting up in person for cash payment.
#bitcoin-otc uses a fairly involved feedback system. It is well worth taking the time to understand this. You'll need to hash out the payment method with the seller. A list of IRC clients is here. Private sellers may accept all sorts of payment methods – up to and including meeting up in person for cash payment.
3. Bitcoin ATM Machines
There are now many places in the world where you can buy Bitcoin by inserting cash into an ATM machine. If you wish to use a Bitcoin ATM as anonymously as possible, be sure to pick one that doesn't require any form of personal validation (this is up to the ATM operator).
Buy Bitcoin by Bitcoinnect 比特通購買比特幣
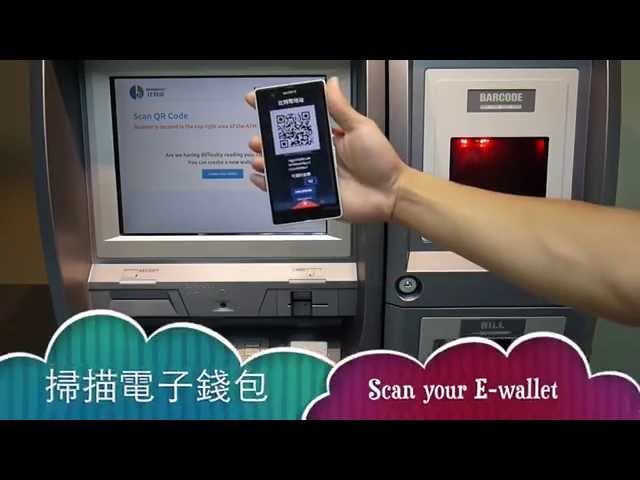
Most Bitcoin ATMs are located in shops and similar places. Remember that most of these have timestamped CCTV security systems. Interested parties could, in theory, use these to de-anonymize you.
My Experience
I used LocalBitcoins.com to buy my Bitcoin. It is an international online marketplace for in-person Bitcoin trading. For maximum anonymity, you can search for someone who lives nearby and arrange a face-to-face meeting with them to buy Bitcoins anonymously with cash. Alternatively, you can buy online and pay with a bank transfer or other agreed method. Options for this include cash bank deposit, cash sent by post, and paying with gift cards. Please be aware that cash, gift cards and similar payments are not covered by LocalBitcoins.com ’s escrow system by default. Buyer trust scores can help mitigate this problem. However, cash and gift card payments are still among the riskiest ways to buy Bitcoin in terms of the potential to lose your money. I therefore strongly recommend only making small Bitcoin purchases in this way.
The Process
How To: Buy Bitcoins on LocalBitcoins.com

-
Register An Account On LocalBitcoins.com. You need a valid email address for verification, but there is nothing to prevent you from using a disposable email account for this. Note that if you use a disposable email address, you won't receive messages and notifications. However, you can access these directly through the website.
-
Next, search to find a seller who matches your criteria.
![local bitcoins Local Bitcoins]() For comparison, here are prices in USD. On 25 October 2017, CoinBase listed the price of a Bitcoin at $5,482.36. As you can see, prices listed by individual LocalBitcoins.com sellers are significantly higher than this. Such is the price of privacy.
For comparison, here are prices in USD. On 25 October 2017, CoinBase listed the price of a Bitcoin at $5,482.36. As you can see, prices listed by individual LocalBitcoins.com sellers are significantly higher than this. Such is the price of privacy.![Local Bitcoins Local Bitcoins]() It is increasingly common for sellers to require that buyers prove their identity. While I am sure there are many perfectly good reasons for this (such as combating fraud), this runs counter to the idea of buying Bitcoin anonymously. I, therefore, filtered results with the 'SMS not required' and 'ID not required' filters. Note that even with these filters selected, many sellers did, in fact, ask for ID in their small print. Others would not sell to VPN or Tor users.
It is increasingly common for sellers to require that buyers prove their identity. While I am sure there are many perfectly good reasons for this (such as combating fraud), this runs counter to the idea of buying Bitcoin anonymously. I, therefore, filtered results with the 'SMS not required' and 'ID not required' filters. Note that even with these filters selected, many sellers did, in fact, ask for ID in their small print. Others would not sell to VPN or Tor users. - Check Out The Profile Of Your Prospect
![Bitcoin Trade Bitcoin Trade]() This seller is not the cheapest available, but has 500+ trades with a 98% feedback score and requires no ID check. He also permits purchases when using a VPN or Tor, although the use of Tor is not recommended For the purposes of this guide, I’m going to pay via bank transfer. It's easy, but still affords a fair degree of privacy as I'm dealing with an individual private seller. Plus, I plan to launder the Bitcoin afterward! I found plenty of sellers who accept various forms of cash and/or store card payment from anonymous buyers. It's worth noting that, in general, the more anonymous the payment a seller accepts, the higher the cost per Bitcoin - and the higher the risk of losing your money. The price for paying with Amazon Card Codes was over twice the going exchange rate for Bitcoin.
This seller is not the cheapest available, but has 500+ trades with a 98% feedback score and requires no ID check. He also permits purchases when using a VPN or Tor, although the use of Tor is not recommended For the purposes of this guide, I’m going to pay via bank transfer. It's easy, but still affords a fair degree of privacy as I'm dealing with an individual private seller. Plus, I plan to launder the Bitcoin afterward! I found plenty of sellers who accept various forms of cash and/or store card payment from anonymous buyers. It's worth noting that, in general, the more anonymous the payment a seller accepts, the higher the cost per Bitcoin - and the higher the risk of losing your money. The price for paying with Amazon Card Codes was over twice the going exchange rate for Bitcoin. -
Buy The Bitcoin
![]() The requested coins are held in escrow (that is, temporarily by LocalBitcoins.com) until the seller receives payment. You must make the payment before the payment window finishes, or LocalBitcoins.com will cancel the trade. This escrow system is designed to protect both buyers and sellers. If either side in a transaction reports a problem, LocalBitcoins.com will hold on to the Bitcoin until both sides are happy. If required, it will provide arbitration. Paying by bank transfer is not very anonymous, as the seller will receive a bank transaction number. However, I plan to further anonymize the purchase by transferring the funds to another wallet and then laundering them. Once you've paid the seller, there is usually a short wait for the transfer process to complete and the payment to be confirmed. Once the seller has confirmed the payment, the Bitcoin is released from escrow and credited to your LocalBitcoins.com wallet. LocalBitcoins.com creates this when you set up a new account.
The requested coins are held in escrow (that is, temporarily by LocalBitcoins.com) until the seller receives payment. You must make the payment before the payment window finishes, or LocalBitcoins.com will cancel the trade. This escrow system is designed to protect both buyers and sellers. If either side in a transaction reports a problem, LocalBitcoins.com will hold on to the Bitcoin until both sides are happy. If required, it will provide arbitration. Paying by bank transfer is not very anonymous, as the seller will receive a bank transaction number. However, I plan to further anonymize the purchase by transferring the funds to another wallet and then laundering them. Once you've paid the seller, there is usually a short wait for the transfer process to complete and the payment to be confirmed. Once the seller has confirmed the payment, the Bitcoin is released from escrow and credited to your LocalBitcoins.com wallet. LocalBitcoins.com creates this when you set up a new account. ![Local Bitcoins Local Bitcoins]() You can check out transactions in your LocalBitcoins.com wallet. Like eBay, LocalBitcoins.com relies on a reputation system. You are therefore expected to leave feedback on the seller once a trade is complete.
You can check out transactions in your LocalBitcoins.com wallet. Like eBay, LocalBitcoins.com relies on a reputation system. You are therefore expected to leave feedback on the seller once a trade is complete. -
Move The Bitcoin To A Private Wallet
Although not strictly necessary if you just want to spend your Bitcoin openly, this improves both privacy and security (assuming you keep your private wallet somewhere secure). For maximum privacy you should create a new wallet address each time you transfer funds. This helps prevent an adversary from linking different Bitcoin transactions you make together.![Send Bitcoins Send Bitcoins]()
-
Sending Bitcoin to your wallet (or anywhere else, for that matter) is easy. Just enter your wallet’s address and the amount you wish to send. Note that transfers are subject to a Bitcoin network transaction fee.
![Sending Bitcoins Sending Bitcoins]()
- After a few minutes, the Bitcoin should appear in your personal wallet (wallet #1). Yay! If you are concerned that interested parties might actively trace your Bitcoin transactions, you should now create a second new wallet (wallet #2) and transfer your funds into that.
It isn't hard for an adversary to trace transfers from wherever you bought the coins to wallet #1. For example, LocalBitcoins.com knows the address of wallet #1. By sending the coin from wallet #1 to wallet #2, you can reasonably claim zero knowledge of, or responsibility for, what happens to funds in wallet #2. All you need is a plausible excuse for why you transferred the money to another person. If you plan to mix your Bitcoin, wallet #2 should be created on the Tor Hidden Services dark web. Electrum is good for this as it supports Tor. Another good option is to create a wallet on Blockchain.info’s .onion website. Depending on your threat model and how anonymous your initial purchase was, you can now start spending your Bitcoin. Alternatively, you can further improve anonymity by mixing the Bitcoin before spending it.
Mixing Bitcoin
The idea behind mixing Bitcoin is to confuse the trail of transactions. This is important if you value privacy, since the Bitcoin blockchain is a public ledger that records all transactions. The mixing process divides your funds into smaller parts and mixes them with random small parts of other people's Bitcoin funds. You end up with completely new coins. This helps to break any link between you and the coins you purchased. Mixing Bitcoin is particularly useful if you've openly purchased your Bitcoin, meaning that someone could easily trace your transactions back to your real identity. If you've already taken steps to purchase the Bitcoin privately, mixing might be overkill. It will, however, help further anonymize your Bitcoin payments. It is worth noting that properly mixing Bitcoin will help protect you not just now, but also if future tools and techniques can trace historic Bitcoin transactions.
Bitcoin Blender
The best beginner's guide to the complex issue of Bitcoin mixing that I know of is published by Bitcoin Blender (but is not specific to that service). Key points about Bitcoin mixing are summarized below. However, I strongly recommend you read through the Bitcoin Blender document, as it goes into much more detail on this highly specialized subject than what is within the scope of this general guide.
Bitcoin Mixers
In order to mix Bitcoin, you need a Bitcoin mixer service (also known as a Bitcoin tumbler). DIY methods of mixing Bitcoins do exist using websites such as LocalBitcoins.com. This is not recommended, however, as it does not really remove the taint and it may require trusting websites that are subject to legal warrants for information. Using CoinJoin can help improve anonymity when DIY mixing, but should only be considered if you really know what you are doing when it comes to Bitcoin and blockchain analysis. Bitcoin mixers are centralized services that keep large reserves of clean Bitcoin. For a service fee, they allow you to swap your Bitcoin for clean Bitcoin. Bitcoin mixers come in two basic flavors – Tor mixers and clearweb (regular internet) mixers.
Tor Mixers
Tor mixers exist only on Tor Hidden Services (aka the dark web), and are therefore the best option for maximum anonymity. On the downside, the operators of these services are themselves anonymous. This means that there is nothing to prevent them disappearing with your coins! In addition to this, Tor mixers are particularly vulnerable to phishing scams (see below). Established Tor mixers with a strong reputation within the Bitcoin community include:
- Bitcoin Blender (http://bitblendervrfkzr.onion)
- Grams Helix
When using a Tor mixer you should always disable JavaScript in the Tor Browser. 
Clearweb Mixers
Clearweb mixers exist on the normal internet. Most of them are legally registered companies. This means that they can be subpoenaed for transaction information. However, many such services promise to keep no logs or personal information. Many clearweb mixers use CloudFlare. This is great for protecting their websites from Distributed Denial of Service (DDoS) attacks, but carries potential privacy risks. One such risk is often the requirement to enable JavaScript in order compete Captchas. The main advantage of clearweb mixers is that they are much less likely to just abscond with your money (although nothing can be 100% guaranteed). Their use of regular HTTPS certificates also makes it much less likely that you will become the victim of a phishing scam. You can, of course, connect to clearweb mixers using the Tor Browser or a VPN to hide your IP address from the mixer. This is will improve your privacy, but is not as anonymous using a Tor mixer. The advice issued by LocalBitcoins.com about the dangers of transferring Bitcoin funds over Tor also holds true here.
Beware Phishing
The internet is flooded with fake links to Bitcoin mixer sites. Even popular, high profile websites can carry fake phishing links. Most clearweb mixer sites use HTTPS. If the domain names look legit and the website has a valid HTTPS certificate (look for a closed padlock in the URL bar), then the site is almost certainly genuine. The same cannot be said for Tor mixer sites, which don't have clearly recognizable domain names or use HTTPS certificates. Indeed, some phishing websites look very convincing, so that even users familiar with the genuine website might be fooled. To the best of my knowledge, the links provided in this article are genuine, but I take no responsibility for them. The same is also true of the trustworthiness of services, even when they’re genuine. Please do your own research before trusting any website with your Bitcoin.
Bitcoin Mixer Aunonymization Features
Even when mixing Bitcoin, a determined adversary may be able to use blockchain analysis techniques (similar in principle to traffic correlation) to trace the Bitcoin trail. In order to counter this threat, mixers often offer some or all of the following obfuscation features:
- Randomized Service Fee – because a fixed service fee on the blockchain may provide a clue as to which mixer service was used.
- Randomized Delay – this makes it difficult to tie together transactions entering and exiting your wallet.
- Multiple Withdrawals – this allows you to receive the mixed coins using multiple transactions and multiple wallets in order to hide the transaction.
For maximum anonymity, you should take advantage of all such available features.
Taint Analysis
When mixing Bitcoin, "taint” is the connection between your old coins and the new ones. 0% taint = no connection at all. In the past, Blockchain.info offered a free "taint analysis” tool that allowed you to manually check for taint. It has shut this tool down, however, and at the time of writing, no real alternative exists.
My Experience
I opted to use popular Tor mixer Helix by Grams, which offers the following features:
- Standard service fee (2.5%)
- Customizable delay (optional, up to 24 hours)
- Multiple address withdrawals (optional)
- Optional 2FA (two-factor authentication)
The service fee is not random, but I can live with that. More important for the purpose of this guide, is that trades require a fairly low minimum of 0.01 BTC (as it was, I had to top the funds in my wallet up a little for this step). You can register for an account, but I opted for the Helix Light (quick mix) option.
- Create a new Bitcoin wallet, to which the newly mixed, untainted Bitcoin will be sent. Let’s call this mixer wallet #3. I will be mixing funds stashed in wallet #2 that I created earlier.
- Grams Helix is a Tor mixer, and is therefore only available via the Tor Hidden Services network. Thus I fire up the Tor Browser and visit (http://grams7enufi7jmdl.onion/helix).
- In the Helix Light tab, just enter the Bitcoin Wallet addresses that you would like the coins sent to (mixer wallet #3, in my case). You can have the coins sent up to five addresses to help obfuscate the transaction.
![Helix Helix]()
- You are then provided a Bitcoin wallet address to send your "dirty” coins to. I sent these from wallet #2.
![Helix Light Helix Light]() Helix also provides a PGP key that verifies the receiving wallet it created for this transaction. Save this key in case there are any problems and you need to prove the transaction occurred. I simply pasted the PGP key text into a text file on my computer. Once the transaction is successfully completed, this can be safely deleted.
Helix also provides a PGP key that verifies the receiving wallet it created for this transaction. Save this key in case there are any problems and you need to prove the transaction occurred. I simply pasted the PGP key text into a text file on my computer. Once the transaction is successfully completed, this can be safely deleted. - Refresh the webpage to see confirmation that the payment has been received (you may need to wait a few minutes for this). You can then increase anonymity by adding a random delay (1-6 hours) and/or send to multiple wallets. Both of these options are recommended.
 Refresh or bookmark and revisit this web page for final confirmation when the transaction is completed. You should now see the mixed Bitcoin in your wallet (mixer wallet #3 for me). Once you have verified that the Bitcoin is in your wallet, hit the "Remove Helix” button to erase all records of the deal from the Helix servers. Then transfer the funds away from the wallet into which you received the mixed funds, into yet another wallet. Just to be sure. I would then check the mixed Bitcoin for taint, but there currently appears to be no way of doing this. Regardless, the Bitcoin should be well mixed by now.
Refresh or bookmark and revisit this web page for final confirmation when the transaction is completed. You should now see the mixed Bitcoin in your wallet (mixer wallet #3 for me). Once you have verified that the Bitcoin is in your wallet, hit the "Remove Helix” button to erase all records of the deal from the Helix servers. Then transfer the funds away from the wallet into which you received the mixed funds, into yet another wallet. Just to be sure. I would then check the mixed Bitcoin for taint, but there currently appears to be no way of doing this. Regardless, the Bitcoin should be well mixed by now.
Using Bitcoin To Buy A VPN Anonymously
Now that you have some highly anonymous Bitcoin, it’s time to spend it! You can use it to buy a VPN subscription, but the process is similar whatever you buy. If you're buying a VPN subscription, please remember that although payment may be anonymous, the VPN provider will always know your real IP address. You are therefore never truly anonymous. The one exception to this rule is if you use VPN through Tor combined with an anonymous payment method such as properly mixed Bitcoin. This can allow for true anonymity when using a VPN because the Tor network hides your IP from the VPN provider. AirVPN is the only VPN service I know of to support this feature, however. Note that the process for paying with Bitcoin varies quite considerably from provider to provider. I have chosen to use Mullvad for this example.
- Register for a new account or sign in to an existing one (see our Mullvad review for more details). On the My Account page, select the Bitcoin tab, choose how long you want to pay for, and hit the "Request payment info” button.
![Mullvad Mullvad]()
- Mullvad will generate a one-use wallet. Send the money to the address given.
![Mullvad Mullvad]()
- Once the Bitcoin payment has received at least one confirmation, your account will be credited with the time purchased. Enjoy!
Bitcoin Privacy Recap
Bitcoin is not inherently anonymous. Far from it, in fact. With some effort, however, it can be made highly anonymous (there is no such thing as 100% guaranteed anonymity). In my experience, buying and mixing Bitcoins was a painless process, but it does require some work. Is it worth the effort? Only you can decide that. For info on how to buy a VPN anonymously click here.

 For comparison, here are prices in USD. On 25 October 2017, CoinBase listed the price of a Bitcoin at $5,482.36. As you can see, prices listed by individual LocalBitcoins.com sellers are significantly higher than this. Such is the price of privacy.
For comparison, here are prices in USD. On 25 October 2017, CoinBase listed the price of a Bitcoin at $5,482.36. As you can see, prices listed by individual LocalBitcoins.com sellers are significantly higher than this. Such is the price of privacy. It is increasingly common for sellers to require that buyers prove their identity. While I am sure there are many perfectly good reasons for this (such as combating fraud), this runs counter to the idea of buying Bitcoin anonymously. I, therefore, filtered results with the 'SMS not required' and 'ID not required' filters. Note that even with these filters selected, many sellers did, in fact, ask for ID in their small print. Others would not sell to VPN or Tor users.
It is increasingly common for sellers to require that buyers prove their identity. While I am sure there are many perfectly good reasons for this (such as combating fraud), this runs counter to the idea of buying Bitcoin anonymously. I, therefore, filtered results with the 'SMS not required' and 'ID not required' filters. Note that even with these filters selected, many sellers did, in fact, ask for ID in their small print. Others would not sell to VPN or Tor users. This seller is not the cheapest available, but has 500+ trades with a 98% feedback score and requires no ID check. He also permits purchases when using a VPN or Tor, although the use of Tor is not recommended For the purposes of this guide, I’m going to pay via bank transfer. It's easy, but still affords a fair degree of privacy as I'm dealing with an individual private seller. Plus, I plan to launder the Bitcoin afterward! I found plenty of sellers who accept various forms of cash and/or store card payment from anonymous buyers. It's worth noting that, in general, the more anonymous the payment a seller accepts, the higher the cost per Bitcoin - and the higher the risk of losing your money. The price for paying with Amazon Card Codes was over twice the going exchange rate for Bitcoin.
This seller is not the cheapest available, but has 500+ trades with a 98% feedback score and requires no ID check. He also permits purchases when using a VPN or Tor, although the use of Tor is not recommended For the purposes of this guide, I’m going to pay via bank transfer. It's easy, but still affords a fair degree of privacy as I'm dealing with an individual private seller. Plus, I plan to launder the Bitcoin afterward! I found plenty of sellers who accept various forms of cash and/or store card payment from anonymous buyers. It's worth noting that, in general, the more anonymous the payment a seller accepts, the higher the cost per Bitcoin - and the higher the risk of losing your money. The price for paying with Amazon Card Codes was over twice the going exchange rate for Bitcoin. The requested coins are held in escrow (that is, temporarily by LocalBitcoins.com) until the seller receives payment. You must make the payment before the payment window finishes, or LocalBitcoins.com will cancel the trade. This escrow system is designed to protect both buyers and sellers. If either side in a transaction reports a problem, LocalBitcoins.com will hold on to the Bitcoin until both sides are happy. If required, it will provide arbitration. Paying by bank transfer is not very anonymous, as the seller will receive a bank transaction number. However, I plan to further anonymize the purchase by transferring the funds to another wallet and then laundering them. Once you've paid the seller, there is usually a short wait for the transfer process to complete and the payment to be confirmed. Once the seller has confirmed the payment, the Bitcoin is released from escrow and credited to your LocalBitcoins.com wallet. LocalBitcoins.com creates this when you set up a new account.
The requested coins are held in escrow (that is, temporarily by LocalBitcoins.com) until the seller receives payment. You must make the payment before the payment window finishes, or LocalBitcoins.com will cancel the trade. This escrow system is designed to protect both buyers and sellers. If either side in a transaction reports a problem, LocalBitcoins.com will hold on to the Bitcoin until both sides are happy. If required, it will provide arbitration. Paying by bank transfer is not very anonymous, as the seller will receive a bank transaction number. However, I plan to further anonymize the purchase by transferring the funds to another wallet and then laundering them. Once you've paid the seller, there is usually a short wait for the transfer process to complete and the payment to be confirmed. Once the seller has confirmed the payment, the Bitcoin is released from escrow and credited to your LocalBitcoins.com wallet. LocalBitcoins.com creates this when you set up a new account.  You can check out transactions in your LocalBitcoins.com wallet. Like eBay, LocalBitcoins.com relies on a reputation system. You are therefore expected to leave feedback on the seller once a trade is complete.
You can check out transactions in your LocalBitcoins.com wallet. Like eBay, LocalBitcoins.com relies on a reputation system. You are therefore expected to leave feedback on the seller once a trade is complete.


 Helix also provides a PGP key that verifies the receiving wallet it created for this transaction. Save this key in case there are any problems and you need to prove the transaction occurred. I simply pasted the PGP key text into a text file on my computer. Once the transaction is successfully completed, this can be safely deleted.
Helix also provides a PGP key that verifies the receiving wallet it created for this transaction. Save this key in case there are any problems and you need to prove the transaction occurred. I simply pasted the PGP key text into a text file on my computer. Once the transaction is successfully completed, this can be safely deleted.
