At the beginning of 2015 both the Chrome and Firefox browsers introduced a new "feature” called WebRTC. Rather alarmingly, however, it permits websites to detect your real IP address, even when using a VPN!
What is WebRTC?
Web Real-Time Communication (WebRTC) is a potentially useful standard that allows browsers to incorporate features such as voice calling, video chat, and P2P file sharing directly into the browser.
A good example of this is the new Firefox Hello video and chat client that lets you talk securely to anyone else using an up-to-date Firefox, Chrome, or Opera browser, without the need to download any add-on, or configure any new settings.
So what’s the problem?
Unfortunately for VPN users, WebRTC allows a website (or other WebRTC services) to directly detect your host machine’s true IP address, regardless of whether you are using a proxy server or VPN.
As the makers of https://diafygi.github.io/webrtc-ips/, a tool that detects whether your browser is vulnerable to a WebRTC leak, explain,
"Firefox and Chrome have implemented WebRTC that allow requests to STUN servers be made that will return the local and public IP addresses for the user. These request results are available to javascript, so you can now obtain a user's local and public IP addresses in javascript. This demo is an example implementation of that.
Additionally, these STUN requests are made outside of the normal XMLHttpRequest procedure, so they are not visible in the developer console or able to be blocked by plugins such as AdBlockPlus or Ghostery. This makes these types of requests available for online tracking if an advertiser sets up a STUN server with a wildcard domain.”
The Opera browser, which uses the same WebKit code that powers Chrome is also affected by the issue, but Internet Explorer and Safari, which do not support WebRTC, are not. Update: newer versions of the stock Android browser appear to implement WebRTC, and so should be avoided.
Am I affected?
You can check for WebRTC leaks by using our very own VPN leak testing tool!

Here we can clearly see that I have a WebRTC leak. The website can see my VPN server’s IP, but can also see real local (UK) IP address. Bad!
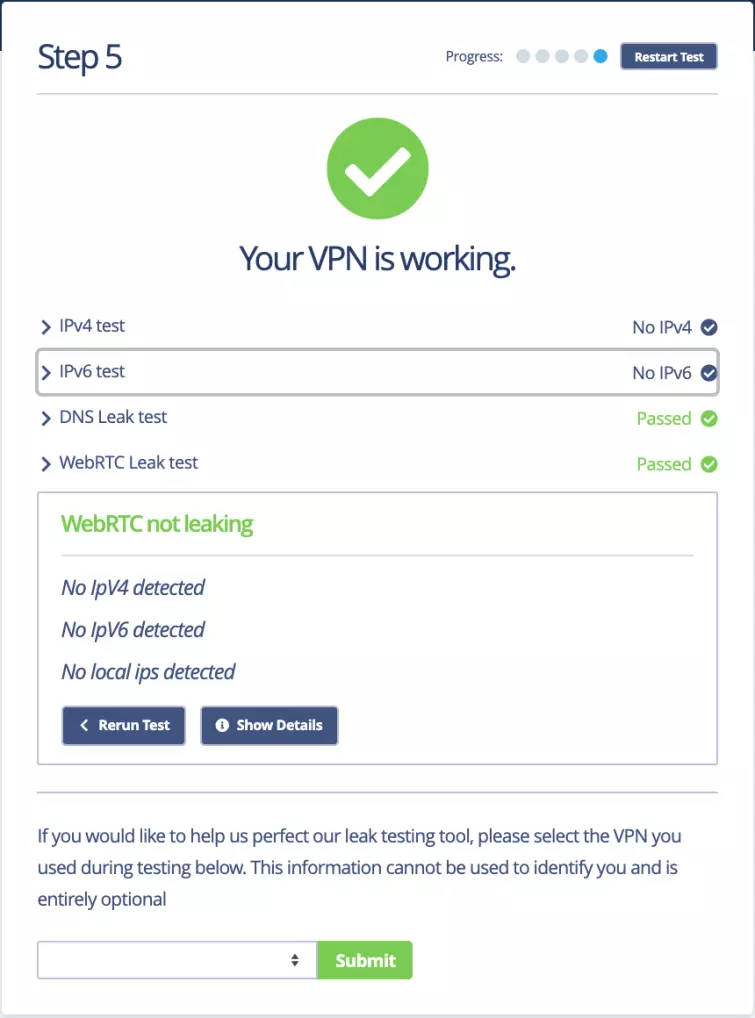
If you have disabled WebRTC in your browser (or are using a browser that does not ”feature” WebRTC, you will see this message. Good!
If you have tested your VPN without disabling WebRTC and you are not getting any leaks, this means that your VPN service has fixed the problem and is routing WebRTC STUN requests through its servers. Bravo!
Although it is great that some VPN providers (such as AirVPN) have taken steps to fix the WebRTC "bug”, it should be stressed that, fundamentally, the problem lies with the WebRTC API, together with the fact that it is enabled by default within affected browsers.
It is therefore is not really the fault of VPN providers, although we would love to see more of them rise to the challenge of helping their customers (who will be largely unaware of the problem) from having their privacy compromised by this issue.
How to fix a WebRTC leak?
The fix for WebRTC leaks differs slightly depending on the browser that you are using. We have listed the steps that you need to take to fix this issue in Firefox, Google Chrome, and Opera browser below.
How to Fix WebRTC leaks in Firefox
-
The simplest solution to the problem is to just disable WebRTC. In Firefox can be easily done manually in the advanced settings:
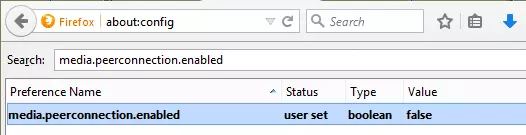
a) Type ‘about:config’ into the URL bar (and click through ‘I’ll be careful I promise!’)
b) Search for ‘media.peerconnection.enabled’
c) Double-click on the entry to change the Value to ‘false’This method also works in mobile versions of Firefox (Android/iOS)
![WebRTC firefox fix]()
-
Install the Disable WebRTC add-on. The uBlock Origin browser extension also prevents WebRTC from leaking your local IP address on the desktop (all of these add-ons also on mobile versions of Firefox.)
![webRTC6]()
In uBlock Origin go to Menu -> Add-ons -> uBlock Origin -> Options -> Show Dashboard to disable WebRTC
-
A more nuclear option is to use the NoScript Add-on. This is an extremely powerful tool, and is the best way to keep your browser safe from a whole host of threats (including WebTRC), but many websites will not play game with NoScript, and it requires a fair bit of technical knowledge to configure and tweak it to work the way you want it to.
It is easy to add exceptions to a whitelist, but even this requires some understanding of the risks that might be involved. Not for the casual user then, but for web savvy power-users, NoScript is difficult to beat (in fact, even with all with most of its features turned off, NoScript provides some useful protections anyway.) NoScript works on desktop versions of Firefox only.
-
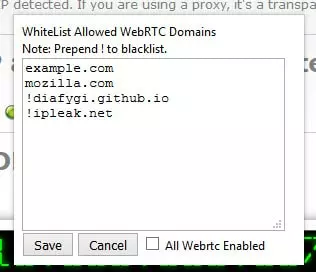
As I have noted, WebRTC can actually be useful, so for a more nuanced approach you can install the Statutory add-on. This allows you to decide, on a site-by-site basis, whether to allow a WebRTC connection. Desktop only.
The Statutory add-on blocks WebRTC by default, but allows you to white-list sites by adding them to this list
![WebRTC 3]()
Note that the Tor Browser (which is based on Firefox) disables WebRTC by default.
How to Fix WebRTC leaks in Google Chrome
-
The uBlock Origin browser extension is also available for Chrome (and work for Opera.)
-
2. The WebRTC Network Limiter browser extension will prevent IP leaks without fully disabling WebRTC functionality (this is an official Google extension.)
-
3. In Android you can manually disable WebRTC in Chrome using the following method:
Type chrome://flags into the search bar and scroll down until you scroll down until you see "WebRTC STUN origin header". Disable this. There are also some WebRTC video decoding options, but you should not need to disable these to prevent WebRTC IP leaks (although if it makes you feel better, go right ahead!).
How to fix a WebRTC leak in Opera
In theory, Opera can use regular Chrome extensions, but these mostly fail to block WebRTC IP leaks. The one method I know of that does work is using the WebRTC Leak Prevent extension, but only if you:
- Go to Menu -> Extensions -> Manage Extensions WebRTC Leak Prevent -> Options
- Set "IP handling policy" to: Disable non-proxied UDP (force proxy), and tick both options under "Legacy".
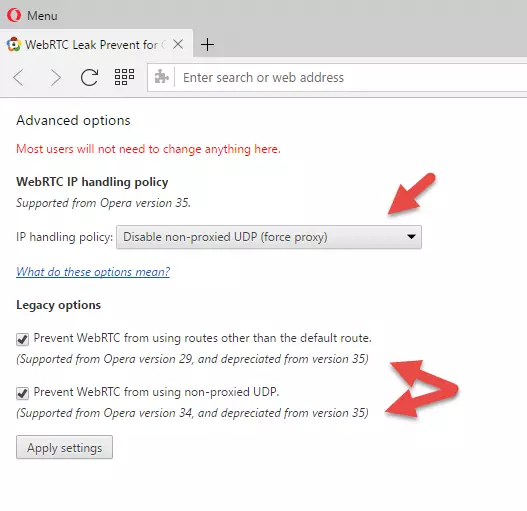
3. Hit "Apply settings".
Conclusion
The WebRTC "bug” is dangerous for VPN users, as it can reveal your true IP address (thereby negating the whole point of using a VPN!)
Although not really their fault, it would be great, however, if more providers could address the problem in order to protect their users, most of whom are completely unaware of this threat.
In the meantime, at least once you are aware of the problem, it can be easily fixed.