One of the main reasons to use a VPN is to hide your true IP address, with the service encrypting your traffic and passing it through its servers before sending it to the internet. This means that third parties and outside observers can only see the IP address of the VPN server.
Unfortunately, there are three ways that prying eyes can discover your real IP address. The first is by convincing your VPN provider to hand it over, which is made difficult by some services offering shared IPs and zero-logs policies. The second is if your VPN is leaking, meaning it is not fully masking your identity. And the third is if you VPN experiences dropouts.
This guide will explain to you how to test for IP leaks, what they are and why you might experience one, and ways to fix them.
How to Test for a DNS Leak or IP leak?
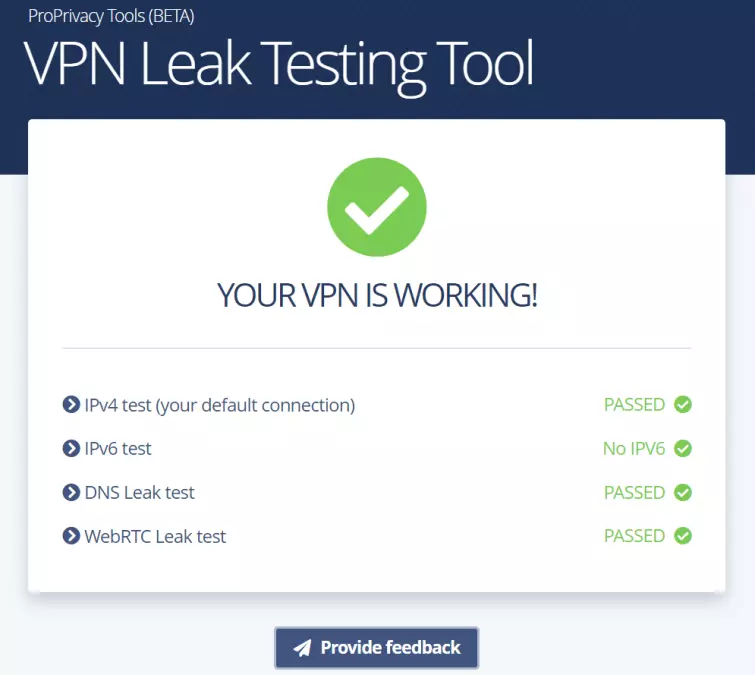
The first step is to check if your VPN is running smoothly. ProPrivacy has streamlined this process with our very own IP leak testing tool.

Our tool tests for IPV4, DNS, and WebRTC leaks, helping you to be sure that your VPN works properly. The tool is completely automated, so you don't have to note down your real IP address before connecting to your VPN, as you would do with other tools. All you have to do is:
- Visit the page, preferably using a private or incognito browser tab.
- Disconnect from your VPN so the tool can determine your actual location.
- Connect to your VPN so we can see if this matches your real IP address. We recommend that you connect to a server outside of the country you are located in, as this will give you a more accurate result.
- The tool will take a few seconds as it checks DNS server requests.
- Our tool will tell you if your VPN service has passed or failed. It's as simple as that!
![leak test showing no leaks]()
You will be prompted with these instructions as you use the tool.
Below, we explain the different kinds of IP leaks and how to fix them. In all cases, though, an often unwritten but advised solution is to change to a service that doesn’t leak, such as the VPNs we recommend.
IP leaks
What is an IPv4 address?
Every internet connection has a unique numerical identifier called an Internet Protocol (IP) address. The IP addresses (or just "IPs”) are assigned by the Internet provider (ISP) that connects the device.
Until recently, the entire internet used the Internet Protocol version 4 (IPv4) standard to define IP addresses. This supports a maximum 32-bit internet address, which translates to 2^32 IP addresses (about 4.29 billion) available for assignment.
Unfortunately, thanks to the unprecedented rise in internet use over the last few years, IPv4 addresses are running out. In fact, technically they have already done so, although workarounds mean that IPv4 is still very far from dead. At present, the vast majority of internet addresses still use the IPv4 standard.
IPv4 leaks
Since IPv4 addresses are the primary protocols used, an IPv4 leak means that your VPN is failing to establish a connection. These are the rarest type of leaks we encounter, but if you come across an IPv4 leak, we recommend trying other servers or moving to another, more reliable provider.
What is an IPv6 address?
While various mitigating strategies have been deployed to extend the shelf-life of IPv4, the real solution comes in the form of a new standard - IPv6. This utilizes 128-bit web addresses, thus expanding the maximum available number to 2^128 (around 340 billion billion billion billion!), keeping us supplied with IP addresses for the foreseeable future.
Adoption of IPv6 has been slow because of upgrade costs, backward capability concerns, and sheer laziness. Consequently, although all modern Operating Systems support IPv6, the vast majority of ISPs and websites do not yet bother.
This has led websites that support IPv6 to adopt to a dual-tiered approach. When connected to an address that only supports IPv4, they will serve up an IPv4 address. But when connected from an address that supports IPv6, they will serve up an IPv6 address.
Until IPv4 addresses start to run out, there is no disadvantage to using an IPv4-only connection.
IPv6 leaks
Unfortunately, a great deal of VPN software has not caught up with IPv6. When you connect to an IPv6 enabled website from an IPv6 enabled internet connection, the VPN client will route your IPv4 connection through the VPN interface but is completely unaware of the IPv6 connection also being made.

So the website won’t see your real IPv4 address, but it will see your IPv6 address - which can identify you.
Solutions
1. Use a VPN client with IPv6 leak protection
All good VPN clients these days offer IPv6 leak protection. In most cases, this is done by disabling IPv6 at the system level to ensure IPv6 connections are simply not possible. This is something of a lazy solution, but it works well.
More technically impressive are VPN apps that properly route IPv6 connections through the VPN interface. This is a much more elegant solution and is undoubtedly the future for all VPN apps.
If your VPN provider’s custom software does not prevent regular IPv6 leaks then you can use a third-party app instead. OpenVPN GUI for Windows, Tunnelblick for macOS, OpenVPN for Android, and OpenVPN Connect for iOS (and other platforms) all provide effective IPv6 leak protection.
2. Disable IPv6 manually on your system
The most sure-fire way to prevent any possibility of IP leaks is to disable IPv6 at the system level (where possible). Please check out our guide on How to disable IPv6 on all devices for instructions on how to do this.
DNS leaks
DNS leaks are the most well-known form of IP leak because they used to be the most common. In recent years most VPN services have stepped up to the mark, however, and we are detecting DNS leaks much less often in our tests.
The Dynamic Name System (DNS) is used to translate the easy-to-understand and remember web addresses we are familiar with (URLs), to their "true” numerical IP addresses. For example, translating the domain name www.proprivacy.com to its IPv4 address of 104.20.239.134. At its heart, DNS is just a fancy telephone book that matches URLs to their corresponding IP addresses.
This DNS translation process is usually performed by DNS servers run by your internet provider (ISP). With larger ISPs, it is likely that DNS queries will be resolved geographically close to you (for example somewhere in your city), but this is not always the case.
What is certain is that DNS queries will be resolved in the country your ISP is based (i.e. your own country). DNS queries will never be resolved at your home IP address, but that doesn't mean there aren't threats to your privacy.
Privacy risks
Your ISP can see what you get up to
It is your ISP who resolves your DNS queries, so:
- It knows the IP address they came from.
- It knows which websites you visit because it’s one translating the URLs you type into IP addresses. Most ISPs the world over keep logs of this information, which they may or may not share with your government or police forces as a matter of routine, but which they can always be compelled to share.
Now… in the normal course of things this doesn’t actually matter too much because it is your ISP which connects you directly to the IP addresses you visit. So it knows which websites you visit, anyway.
A VPN server proxies your internet connection, though, to prevent your ISP from seeing what you get up to on the internet. Unless it is still resolving your DNS queries, in which case it can still (indirectly) see which website you visit.
You can be traced
Websites can see and log the IP addresses of DNS servers which direct connections to them. They won’t know your unique IP address in this way, but they will know which ISP resolved the DNS query and routinely create a timestamp of when it happened.
If they (or the police, for example) want to identify a visitor they simply have to ask the ISP "who made a DNS request to this address at this time?”
Again, in the normal course of things, this is irrelevant, since websites can see your unique IP address, anyway. But when you are hiding your IP address with a VPN, it becomes an important means of "de-anonymizing” VPN users.
How DNS leaks happen?
In theory, all DNS requests should be sent through the VPN, where they can be handled in-house by your VPN provider or proxied out to a third party who will only see that the request came from the VPN server.
Unfortunately, operating systems sometimes fail to route DNS queries through the VPN interface and instead send them to the default DNS server specified in the system settings (which will be your ISP’s DNS server unless you have manually changed your DNS settings).
Solutions
1. Use a VPN client with DNS leak protection
Many VPN clients address this problem with a "DNS leak protection” feature. This uses firewall rules to ensure no DNS requests can be sent outside the VPN tunnel. Unfortunately, these measures are not always effective.
We don't understand why "DNS leak protection” is often a user-selectable feature that is not enabled by default.
Again, OpenVPN GUI for Windows, Tunnelblick for macOS, OpenVPN for Android, and OpenVPN Connect for iOS (and other platforms) all offer good DNS leak protection.
2. Disable IPv6
Note that this is only a partial solution, as it does not prevent IPv4 DNS leaks. But one of the main reasons that DNS leak protection fails to block leaks is because they only firewall DNS requests to IPv4 DNS servers.
Since most DNS servers remain IPv4-only, they can often get away with this. But ISPs that offer IPv6 connections also usually offer IPv6 DNS servers. So if a client only blocks IPv4 DNS requests outside the VPN interface then IPv6 ones can get through.
3. Change your DNS settings
Any wayward DNS queries which don’t route through the VPN interface (as they should) will instead be sent to the default DNS servers specified in your system’s settings.
Unless you have changed these already, then the DNS server addresses (IPv4 and IPv6 if available) will be obtained automatically from your ISP. Check out our guide on how to change you DNS settings for more information about this.

Changing your DNS settings is not really "fixing” the DNS leak issue. It’s just that you are leaking DNS requests to a third party resolver instead of your ISP.
Fortunately, there are now some very good privacy-focused DNS services that keep no logs. They also protect DNS requests with DNS over HTTPS (DoH) or DNS over TLS (DoT) DNS encryption, without which your ISP can see the DNS requests, anyway, even if it is not handling them.
A note for Linux users
Manual VPN setup in Linux, whether using NetworkManager, the CLI OpenVPN client, strongSwan, or whatever, provides no DNS leak protection. Fortunately, there are steps you can take to fix this issue, although they complicate the VPN setup process.
You can modify resolvconf to push DNS to your VPN’s DNS servers, or you can manually configure the iptables firewall to ensure all traffic (including DNS requests) cannot leave your Linux machine outside the VPN tunnel. Please see our notes on building your own firewall later in this article for more on this.
WebRTC leaks
WebRTC leaks are now the most common form of IP leak we see in our tests. Strictly speaking, WebRTC leaks are a browser issue, not a VPN issue, which has led many VPN providers to distance themselves from a problem which is not easy to fix.
In our view, this is not good enough. We also don't think publishing a "How to Disable WebRTC” guide hidden deep inside a provider’s help section is good enough, either.
What is WebRTC?
WebRTC is an HTML5 platform that allows seamless voice and video communication inside users’ browser windows. Almost all modern browsers on almost all major platforms now support WebRTC, including Chrome, Firefox, Opera, Edge, Safari, and Brave.
An exception is in iOS, where only Safari supports WebRTC (at least without additional plugins).
To achieve seamless browser-to-browser communication through obstacles such as firewalls, WebRTC-enabled browsers broadcast your real IP address(es) to STUN servers, which keep a list of both users’ public IP addresses and their real IP addresses.
Anyone wishing to initiate a WebRTC conversation with you (or just any nosey website) can request your real IP address, and the STUN server will simply hand it over.

Usually referred to as a WebRTC leak, this problem is sometimes called the "WebRTC bug.” Which is something of a misnomer since it is an intentional and very useful feature of WebRTC. But it is a real pain for VPN users who are trying to hide their real IP address!
Solutions
1. Disable WebRTC in your browser
This is the only 100% effective way to prevent a WebRTC leak when using a VPN. We recommend doing it even if your VPN client is effective at mitigating against VPN leaks.
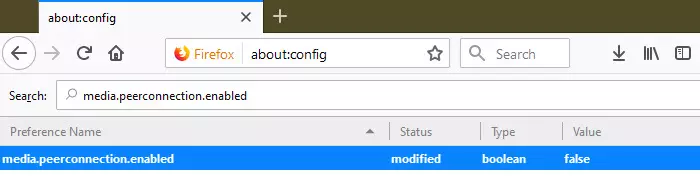
In Firefox it is easy to disable WebRTC. Type "about:config” into the URL bar to enter Firefox’s advanced settings, search for "media.peerconnection.enabled,” and double-click on the entry to change its value to false.
Alternatively (and in other browsers), there are various browser plugins can disable WebRTC, including Disable WebRTC, uBlock, uBlock Origin and NoScript. Some VPN providers include a Disable WebRTC feature in their custom browser add-ons.
A more complete discussion on this subject can be found at What is the WebRTC VPN "Bug” and How to Fix It?
2. Use a VPN service which mitigates against WebRTC leaks
WebRTC leaks are a browser issue, so the only truly effective way to prevent this is by disabling WebRTC in the browser.
That said, VPN providers can use firewall rules and tighten up settings at both the client and VPN level to greatly reduce the chance of WebRTC leaks occurring. No VPN provider will guarantee that these measures work because it is always possible for websites to implement clever JavaScript code designed to increase the likelihood of leaks.
We have, however, found that some VPN services are consistently effective at preventing VPN leaks. We still recommend disabling WebRTC at the browser level even with these, though. Just to be on the safe side.
VPN dropouts
Although not technically an "IP leak,” as the problem occurs exactly because you don’t have a VPN connection, the effect is the same – you think you are protected by VPN, when in fact the whole world can see your IP address. However, there are features that VPNs have to protect you when your VPN connection fails, we review them below.
What is a VPN dropout?
Sometimes VPN connections fail, often for reasons completely outside the control of even the best VPN services. If your computer remains connected to the internet after this happens, then your real IP will be exposed.
This is particularly a problem for if you plan on using a VPN for torrenting. Many downloaders who leave BitTorrent clients running while they are away from their computers (often for long periods of time). If the VPN connection drops, their true IP is exposed to anyone tracking the torrent they are downloading.
It is also a problem for mobile users, as switching between WiFi and mobile networks, and switching mobile networks, can cause VPN dropouts.
Solutions
1. Use a kill switch
A kill switch prevents your device connecting to the internet when the VPN is not working. Almost all modern kill switches are actually firewalls or system-level firewall rules which block all internet connections outside the VPN interface.
So if the VPN software fails or needs to reconnect, then all access to the internet is blocked. Indeed, the same firewall rules provide effective DNS leak protection and can help mitigate against WebRTC leaks. Check out our what is a killswitch guide for more information about this.
Kill switches are now a very common feature in desktop VPN clients, although rarer in mobile apps. Android 7+, however, includes a built-in kill switch that works with any installed VPN app.
VPN apps may use their own firewall to create a kill switch (and other leak protection) or may modify your system’s built-in firewall. We prefer the latter solution as the kill switch will survive, even if the app completely crashes. But any kill switch is much better than none.
Build your own kill switch and DNS leak protection using firewall rules
As we have seen, many VPN apps use their own firewall rules or modify your system firewall rules to create a kill switch and prevent DNS leaks. It is entirely possible for you to build your own kill switch.
Details differ by OS and firewall program, but the basic principles are:
We have a detailed guide for doing this using Comodo Firewall for Windows. Mac users can do the same using Little Snitch, while Linux users and those running a VPN client on a DD-WRT router can use iptables.