A VPN and Tor are very different beasts, but they are both privacy technologies with a great deal of overlap in function. This means that it is possible to use a VPN and Tor together. In this guide, we make recommend the best VPNs for Tor and give you information and some helpful tips on using a VPN over onion.
The Best VPN for Tor
We have listed the best VPNs for Tor below. These services have been chosen as they all offer a high level of security, have great no-logs policies, and have fast servers located around the world. If you want more information about the providers listed below, scroll on for a closer look at our recommended VPNs for Tor.
- PrivateVPN - The best VPN for Tor. Its superb speeds and server selection allow users to stream, download, or unblock content in a blink. Try today with a 30-day money-back guarantee!
- NordVPN - The most feature-packed VPN for Tor. The apps only take a moment to download, are easy to setup, and have a fresh, uncluttered design that appeals to VPN newcomers.
- Proton VPN - A fast and secure VPN for Tor. A Swiss-based provider that abides by a strict zero-logs policy, and one that has even invited independent auditors to examine its infrastructure.
- AirVPN - The best secure VPN for Tor. It gives users the ability to cloak their online activity as well as plenty of advanced encryption options, and all protocols are supported.
- Mullvad - A great all-round Tor VPN. A service with a variety of features to suit newbies and veterans, like a built-in kill-switch and ad-blocker, and easy setup!
5 best Tor VPN services | In-depth analysis
We have gone into more detail about each Tor VPN service below by calling out what makes each service a great option for Tor users. If you would like even more detailed information about any particular service you see here, click through to the provider's website, or take a look at our in-depth VPN reviews.
PrivateVPN is the best cheap VPN for Tor. Its superb encryption, and ever-growing network of reliable servers, give you free rein across the web. Try today with a 30-day money-back guarantee! PrivateVPN Demo PrivateVPN is a Swedish-based no-logs VPN. It offers robust encryption, unlimited bandwidth and speed, helpful and friendly 24/7 live chat support, and permits up to six simultaneous connections. Thanks to its tactic of issuing new dedicated IP addresses as required, PrivateVPN has an excellent reputation for unblocking almost every streaming service on the internet - including Netflix US (and a large choice of international Netflix catalogs). And because it has a kill-switch, you get peace of mind, knowing that your internet will disconnect if your VPN connection fails. And, PrivateVPN supports OpenVPN through Tor – though this does require you manually edit your OpenVPN configuration file yourself (which is a bit of a fiddle) and to connect using a third party client (available from the OpenVPN website). The good news is that full instructions are available on its website. We think this is an excellent VPN for Tor that provides incredible value for money. And it has servers worldwide that permit torrenting. Well worth testing using its 30-day money-back guarantee. NordVPN is the best user-friendly VPN for Tor. It's loaded with features and boasts incredible speeds, so you can stream and browse without interruptions. Nord Demo NordVPN is a no-logs provider that uses robust AES-256 encryption, and accepts anonymous payments via Bitcoin. Users can connect up to six devices at once and can choose from over 5,200 servers in over 60 countries! On top of this, Nord has “Onion over VPN,” which is Tor through VPN using special OpenVPN configuration files that can be easily selected in its GUI client. This makes it one of the best VPNs for Tor right out of the box. We like NordVPN because it offers a variety of privacy and security tools, including XOR obfuscation and “CyberSec,” a feature that blocks DNS requests based on a real-time blocklist of harmful websites that are suspected to host malware. A solid service that you can try risk-free using its 30-day money-back guarantee. ProtonVPN is a speedy and secure VPN for Tor. Open-source and security-oriented, its robust encryption will keep third party snoops from monitoring your browsing sessions. Proton Demo ProtonVPN is a Swiss-based VPN service that lives up to the good name enjoyed by its elder sister-service, ProtonMail. Depending on which plan you buy, ProtonVPN allows up to 10 simultaneous connections and runs servers in over 51 countries around the world. ProtonVPN supports Tor through VPN natively in it's app (paying customers only), which makes it one of the best VPNs for Tor. It has an excellent free plan which will be good enough to serve as a full VPN service for many users. If you sign up for the free plan, you are also offered a 7-day free trial of the premium, paid service. And if you upgrade to the premium, you have up to 30 days to use the provider's money-back guarantee. Take full advantage of its free trial and test it for yourself, risk-free. AirVPN is the best secure Tor VPN. Developed by activists, the service supports P2P activity, implements OpenVPN encryption, and even boasts Perfect Forward secrecy. AirVPN Demo AirVPN is, without a doubt, one of the best VPN services for Tor browser. This Italian provider offers among the best security and anti-censorship technology available on the web, allowing both SSH and SSL tunneling to evade government blocks. Add in a solid no-logs policy, some of the strongest encryption around, and a Windows, macOS, and Linux GUI client with built-in DNS leak protection and a kill switch, and AirVPN is a strong choice for privacy enthusiasts. In keeping with its usual technical excellence, AirVPN is one of the few VPN providers to offer OpenVPN through Tor. Indeed, it is the only service to support this feature through its open-source GUI “Eddie” client. On top of this, it also provides instructions for combining Tor and VPN using the Tor Browser VPN method. The main problem with AirVPN is that its service is definitely aimed at techies, so using it may not be so straightforward for newbies. You can try it for yourself with a 3-day trial for only $2.35 (2€). Mullvad is an excellent all-round VPN for Tor. An inexpensive service boasting obfuscation measures and privacy-enhancing features, as well as blazing speeds ideal for torrenting. Mullvad is a service for tech enthusiasts, and cares strongly about its users’ privacy. In an unprecedented move, it even accepts payment in cash sent by post! It allows up to five simultaneous connections and offers a three-hour free trial. We like the fact that its custom desktop client is one of only two we know of to fully support routing through IPv6. Mullvad supports manual configuration of OpenVPN through Tor by downloading the Tor Bundle and editing the OpenVPN config files (instructions are available in the Help section of their website). You can sign up anonymously for this VPN service and don't need an email address or a username. And you can try it for yourself using its 30-day money-back guarantee (which will let you see why it's a popular choice for techier, privacy purists). However, unlike PrivateVPN, which features higher in this list (and has the same manual OpenVPN through Tor setup using a third party client), it isn't such a good all rounder when it comes to accessing geo-restricted content. However, if you have an IPv6 connection specifically; this is a good option. 1. PrivateVPN
Pricing
Pros
Cons
Logging policy
Accepts cryptocurrency?
Supports Tor-over-VPN?
Has .onion site?
Website

Pricing
Pros
Cons
Logging policy
Accepts cryptocurrency?
Supports Tor-over-VPN?
Has .onion site?
Website

Pricing
Pros
Cons
Logging policy
Accepts cryptocurrency?
Supports Tor-over-VPN?
Has .onion site?
Pricing
Pros
Cons
Logging policy
Accepts cryptocurrency?
Supports Tor-over-VPN?
Has .onion site?
Website

5. Mullvad

Pricing
Pros
Cons
Logging policy
Accepts cryptocurrency?
Supports Tor-over-VPN?
Has .onion site?
Methods for using Tor With a VPN
There are several ways you can use a VPN and Tor together and so we have listed them below, along with the pros and cons of each method.
Tor through VPN (using a transparent proxy)
This is by far the most common Tor VPN method. You connect to a special "Tor VPN server” operated by your VPN provider. This server then transparently routes your internet connection through the Tor network so that the endpoint connected to the internet is a Tor exit node.

Your ISP sees that you have connected to a VPN server. Websites and anyone else on the internet see the IP address of the Tor exit node.
Pros:
- Your entire internet connection is routed through both the VPN and the Tor network.
- Your VPN provider cannot see which websites you visit on the internet
- You can access Tor hidden services (.onion websites) using your regular browser.
- Your ISP cannot see that you are using Tor (although it can know that you are using a VPN)
- To identify your real IP address from the internet would require compromising both the Tor network and your VPN provider.
Cons:
- You lose the true anonymity afforded by Tor because your VPN provider can see your real IP address (and may know payment details, although this can be avoided using properly anonymized cryptocurrencies).
- The VPN provider can see the contents of your data (if not protected by HTTPS).
- The Tor exit node can see the contents of your data (if not protected by HTTPS), and which websites you visit on the internet.
- Public Tor exit nodes are openly published and are therefore easy to block. This is a problem with Tor in general, but regular Tor users can use Tor bridges to bypass such blocks in a way that Tor through VPN users cannot.
- The drop in speeds you experience is that of Tor and the VPN combined.
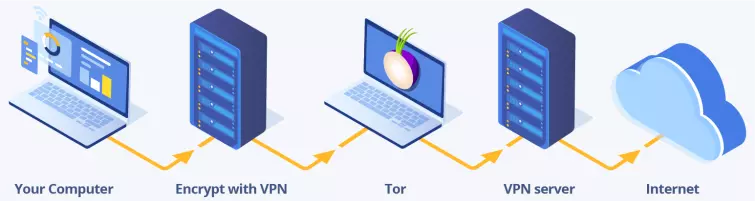
VPN through Tor
This method works in reverse to the previous Tor through VPN one. You connect to the VPN server via the Tor network. The endpoint connection to the internet is the VPN server.
Your ISP sees that you have connected to the Tor network. Websites and anyone else on the internet see the IP address of the VPN server.
Pros:
- Your VPN provider cannot know your real IP address. If combined with an anonymous payment method, then this allows true anonymity when using the VPN.
- The Tor exit node cannot spy on you because your data is secured using the VPN encryption, and what you do on the internet is blocked by the VPN server.
- The endpoint is the VPN server, so blocks on Tor exit nodes are ineffective.
- Al internet traffic is routed through both the Tor and VPN networks.
- You can choose any VPN server location supported by your VPN provider.
- If care is taken to pay anonymously and only connect to the VPN and the VPN website using Tor, then this method allows true anonymity.
- To identify your real IP address from the internet would require compromising both your VPN provider and the Tor network.
Cons:
- The VPN provider can see everything a VPN provider can usually see. This is pretty much everything, but if you have been careful to pay anonymously and only connect via the Tor network, then it will not know who you are.
- Unlike using Tor on its own, the VPN is a fixed point in the chain. It would theoretically be possible for an adversary to exploit this by compromising the VPN service so that over time it could perform an end-to-end timing or other de-anonymization attacks. Any such attack would be very hard to perform, and if the provider keeps logs it cannot be performed retrospectively. But the risk is still there.
- Speed hit is that of Tor and the VPN combined.
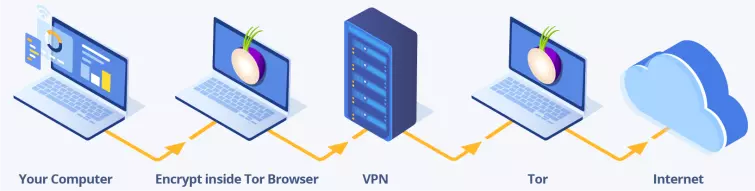
Tor Browser VPN
Technically speaking, this is a version of Tor through VPN. It has some important differences, however, to let your VPN provider transparently route your internet connection from its servers.
In this method, you connect to a VPN server and then access the internet using the Tor Browser. You can connect to the VPN using any VPN software or via a VPN router. Note that this method can be achieved using Whonix instead of the Tor Browser, but for the sake of simplicity, we’ll just refer to the Tor Browser.
Your ISP sees that you have connected to a VPN server. Websites and anyone else on the internet see the IP address of the Tor exit node.
Pros:
- Your VPN provider cannot see which websites you visit on the internet
- It also cannot see the contents of your data because it is encrypted inside the Tor browser
- You can access Tor hidden services (.onion websites), but only using the Tor Browser
- Your ISP cannot see that you are using Tor (although it can know that you are using a VPN)
- To identify your real IP address from the internet would require compromising both the Tor network and your VPN service.
- The Tor Browser is a version of Firefox been "hardened” for improved privacy security. It is also the best defense against browser fingerprinting techniques. For more details on this please see our Tor Review.
Cons:
- You lose the true anonymity afforded by Tor because your VPN provider can see your real IP address (and may know payment details, although this can be avoided using properly anonymized cryptocurrencies).
- The Tor exit node can see the contents of your data (if not protected by HTTPS), and which websites you visit on the internet.
- Public Tor exit nodes are openly published and are therefore easy to block. Because you are using the Tor browser, however, you can use Tor bridges to mitigate against this problem.
- Speed hit is that of Tor and the VPN combined.
- Only your Tor Browser session is protected by Tor. Everything else is protected by your VPN only.
Analysis
Here are some of our thoughts on the matter.
- Adding an extra "layer” of protection does introduce meaningful benefits, but the jury is out over whether these offset the disadvantages.
- We do not consider Tor through VPN using a transparent proxy to be very secure. Being able to access Tor's hidden services using your regular browser is very convenient, however, so it all depends on what your specific threat model is and what you hope to achieve.
- Tor through VPN using the Tor Browser VPN method achieves a similar end and is much more secure. If you are doing anything that requires real anonymity we recommend doing this over the convenience of Tor through VPN using a transparent proxy.
- In both the above methods, though, you lose the true anonymity afforded by Tor.
- The VPN through Tor method basically allows you to use a VPN anonymously, but this requires great care to do effectively.
- Tor on its own also provides true anonymity without introducing a fixed point of weakness.
- But having a VPN server, rather than a Tor exit node, as the endpoint does offer some real advantages.
End-to-end timing (e2e) attacks
An end-to-end timing attack (e2e) is a technique used to de-anonymize VPN and Tor users by correlating the time they were connected to the timing of otherwise anonymous behavior on the internet.
On a global scale, pulling off a successful e2e attack against a Tor user would be a monumental undertaking. But probably not impossible for the likes of the NSA, who are suspected of running a high percentage of all the world public Tor exit nodes.
If such an attack (or another de-anonymization tactic) is made against you while using Tor, then using a VPN as well will provide an additional layer of security.
Should you use a Tor browser VPN?
The debate as to whether you should use a Tor browser VPN (or even any VPN with Tor) is still ongoing. By considering the effects of such setups, you can develop your understanding of how these systems work, and generate better operational security as a result.
Though they may appear similar, VPNs and Tor can benefit you in very different ways. A VPN will provide you with a high level of day-to-day privacy, with minimal disruption to your internet experience. However, Tor provides true anonymity with a much larger impact on your internet experience – and so isn't really viable for day-to-day use.
We think it's more appropriate to use each privacy tool for what it's best at (rather than trying to have one tool do everything). By using a VPN to secure your day-to-day browsing and switching to Tor to access hidden services or when true anonymity is required, you can get the most out of each without compromising the integrity of either.
There are viable real-world uses for combining Tor and VPN, and running a VPN through Tor configuration definitely seems to have the most potential. But we cannot stress enough that:
Please Remember
Anyone planning to combine a VPN with Tor should consider carefully, and comprehensively, what they hope to achieve by doing so, and what the security implications of such actions may be. To not do so risks compromising your privacy and security, and depending on your intended use of these tools, could land you in serious trouble.
Conclusion
If you want to use a VPN with Tor, then it's important that you get the right configuration, and, more importantly, the right VPN. Using a VPN that's compatible with Tor will help you maximize your online security, privacy, and anonymity. To that end, here's a reminder of our top picks for VPNs for Tor:
- PrivateVPN - The best VPN for Tor. Its superb speeds and server selection allow users to stream, download, or unblock content in a blink. Try today with a 30-day money-back guarantee!
- NordVPN - The most feature-packed VPN for Tor. The apps only take a moment to download, are easy to setup, and have a fresh, uncluttered design that appeals to VPN newcomers.
- Proton VPN - A fast and secure VPN for Tor. A Swiss-based provider that abides by a strict zero-logs policy, and one that has even invited independent auditors to examine its infrastructure.
- AirVPN - The best secure VPN for Tor. It gives users the ability to cloak their online activity as well as plenty of advanced encryption options, and all protocols are supported.
- Mullvad - A great all-round Tor VPN. A service with a variety of features to suit newbies and veterans, like a built-in kill-switch and ad-blocker, and easy setup!




