Back in 2013, Edward Snowden revealed that privacy was something the US government considers a privilege, not a right. The National Security Agency (NSA) collected and stored the data of anyone they could – regardless of whether they were US citizens. So, while the documents Snowden released forced Congress to scale back the NSA's reach and offer some transparency, it's down to us to protect our basic human right to privacy in a world of overzealous surveillance.
Sadly, these invasive practices arent exclusive to the US. Governments across the world employ everything from ISP logging to phone malware if it allows them to spy on their citizens. To this day, most of them continue to pursue legislation that allow for backdoors to monitor your calls, messages, and general internet activity.
Fortunately, there are steps we can take in order to avoid the eye-in-the-sky that bears increasing similarity to George Orwell's Big Brother. Using encryption to protect your data is a good start. Encryption can make life difficult for surveillance organizations that are tasked to decrypt it, and though encrypted information will be kept indefinitely until it's cracked, cracking it is an incredibly lengthy process. As a result, if encrypted data becomes our new standard, it'll be singled out less by agencies that don't wish to waste their time.
How secure is encryption?
The revelations regarding the scale of the NSA's deliberate assault on global encryption standards have dented their reputation. Lets examine the current state of play.
Encryption key length
 Key length is the crudest way of determining how long a cipher will take to break – it's the raw number of ones and zeros used in a cipher. Ciphers can be targeted by brute force attacks (or exhaustive key searches). These attacks are just as crude, with the attacker attempting every possible combination to find the correct one.
Key length is the crudest way of determining how long a cipher will take to break – it's the raw number of ones and zeros used in a cipher. Ciphers can be targeted by brute force attacks (or exhaustive key searches). These attacks are just as crude, with the attacker attempting every possible combination to find the correct one.
Breaking modern encryption ciphers is a huge undertaking – of course, if anyone is capable of doing so, it's probably the NSA. Let's examine what would happen if the NSA attempted a brute force attack against various ciphers.
128-bit key
A 128-bit key cipher has 3.4 x10(38) possible keys. Going through each of them would take thousands of operations (or more) to break.
In 2016, the most powerful supercomputer in the world was the NUDT Tianhe-2 in Guangzhou, China. Almost 3 times as fast as the Fujitsu K, at 33.86 petaflops, it would "only" take it around a third of a billion years to crack just one 128-bit AES key!
256-bit key
A 256-bit key would require 2(128) times more computational power to break than a 128-bit one.
The number of years required to brute force a 256-bit cipher is 3.31 x 10(56) – which is about 20000...0000 (total 46 zeros) times the age of the universe (13.5 billion or 1.35 x 10(10) years)!

128-bit encryption
Until the Edward Snowden revelations, we assumed that 128-bit encryption was, in practice, uncrackable through brute force. People even thought this would be the case for another 100 years (taking Moore's Law into account).
Moore's Law states that processor speeds, or overall processing power for computers, will double every two years.
And this still holds true in theory. However, we're currently advancing at a slower pace than Moore's Law would predict. This is due to hardware designers brushing up against the hard limits set by the laws of physics: transistors can only be built so small, for example, and can only be placed so close together. The sheer quantity of resources that the NSA seems willing to throw at cracking encryption has also shaken experts' faith in these predictions. Consequently, system administrators the world over are scrambling to upgrade cipher key lengths.
If and when quantum computing becomes widely available, all bets will be off. Encryption will have to be developed from scratch. Quantum computers will be exponentially more powerful than any existing computer and will make all current encryption ciphers and suites redundant overnight.
In theory, the development of quantum encryption will counter this problem. Access to quantum computers will, however, initially be the sole preserve of the most powerful and wealthy governments and corporations. Plus, it's not in the interests of these organizations to democratize encryption.
It should be noted that the US government uses 256-bit encryption to protect 'sensitive' data, and 128-bit encryption for 'routine' needs. However, it also uses the AES cipher, which isn't without its own issues.
Ciphers
Encryption key length refers to the amount of raw numbers involved. Ciphers are the mathematics used to perform the encryption. It is weaknesses in these algorithms, rather than in the key length, that often leads to encryption breaking.
By far the most common ciphers that you'll encounter are those used by OpenVPN: Blowfish and AES. In addition, RSA is used to encrypt and decrypt a ciphers keys, and SHA-1 or SHA-2 are used as hash functions to authenticate the data.
The most secure VPNs use an AES cipher. Its adoption by the US government has increased its perceived reliability, and consequently its popularity. However, there is reason to believe this trust may be misplaced. If you'd like to learn more, check out our complete guide to VPN encryption where we take a look at the types of encryption employed by VPNs.
NIST
The United States National Institute of Standards and Technology (NIST) developed and/or certified AES, RSA, SHA-1, and SHA-2. NIST also works closely with the NSA in the development of its ciphers.
Given the NSAs systematic efforts to weaken or build backdoors into international encryption standards, there is every reason to question the integrity of NIST algorithms.
NIST has been quick to deny any wrongdoing ("NIST would not deliberately weaken a cryptographic standard"). It has also has invited public participation in several upcoming proposed encryption-related standards in a move designed to bolster confidence.
The New York Times, however, has accused the NSA of introducing undetectable backdoors, or subverting the public development process to weaken the algorithms, thus circumventing NIST-approved encryption standards.
News that a NIST-certified cryptographic standard – the Dual Elliptic Curve algorithm (Dual_EC_DRGB) – had been deliberately weakened not just once, but twice, by the NSA further eroded any existing trust.

A potential backdoor in Dual_EC_DRGB had already been noticed, however. Researchers at the Eindhoven University of Technology in the Netherlands noted, in 2006, that it was easy enough to launch an attack via an "ordinary" PC. Microsoft engineers also flagged a suspected backdoor in the algorithm.
Despite these concerns, Microsoft, Cisco, Symantec, and RSA all include the algorithm in their products' cryptographic libraries. This is because compliance with NIST standards is a prerequisite to obtaining US government contracts.
NIST-certified cryptographic standards are pretty much ubiquitous throughout all areas of industry and business that rely on privacy (including the VPN industry). And it's all rather chilling. Worse still, because these standards are used everywhere, cryptography experts may be unwilling to face the growing list of problems.
To learn more about the privacy issues facing US citizens, as well as how folks in the US can better protect themselves online, check out our Best VPNs for the USA guide.
Perfect forward secrecy
One of the most prevalent revaltions in Edward Snowden's information asserted that: "another program, code-named Cheesy Name, was aimed at singling out SSL/TLS encryption keys known as certificates", and that these certificates might be "vulnerable to being cracked by GCHQ supercomputers".
That these certificates can be "singled out" strongly suggests that 1024-bit RSA encryption (commonly used to protect certificate keys) is weaker than previously thought. The NSA and GCHQ could, therefore, decrypt it much more quickly than expected.
In addition to this, the SHA-1 algorithm widely used to authenticate SSL/TLS connections is fundamentally broken. In both cases, the industry is scrambling fix the weaknesses as fast as it can. It is doing this by moving onto RSA-2048+, Diffie-Hellman, or Elliptic Curve Diffie-Hellman (ECDH) key exchanges and SHA-2+ hash authentication.
What these issues (and the 2014 Heartbleed Bug fiasco) highlight is the importance of using perfect forward secrecy (PFS) for all SSL/TLS connections.
This is a system whereby a new and unique private encryption key (with no additional keys derived from it) is generated for each session. For this reason, it's also known as an ephemeral key exchange.
When using PFS, one SSL key being compromised doesn't matter that much, as new keys are generated for each connection. Keys are also often refreshed during connections – and to meaningly access communications would require these new keys to be compromised. This makes the task so arduous as to be effectively impossible.
Easy access
It's common practice for companies to use just a single private encryption key, unfortunately. Whilst it's a lot easier for these companies to do so, it also puts them in jeopardy, seeing as if this key is compromised, the attacker will be able to access all communications encrypted with it.
OpenVPN and PFS
The most widely used VPN protocol is OpenVPN. It's considered very secure, primarily because it allows the use of ephemeral keys.
Sadly, very few VPN providers implement these keys. And without perfect forward secrecy, OpenVPN connections cannot be considered secure.
It is also worth mentioning here that the HMAC SHA-1 hashes routinely used to authenticate OpenVPN connections are not a weakness. This is because HMAC SHA-1 is much less vulnerable to collision attacks than standard SHA-1 hashes. That said, TLS 1.3 has moved away from SHA-1 for HMAC, amidst a sea of other changes to drop support for insecure protocols. Where possible, you should ensure your OpenVPN implementation uses TLS 1.3.
The takeaway – so, is encryption secure?
To underestimate the NSAs ambition or ability to compromise all encryption is a mistake. However, encryption remains the best defense we have against it (and other threats like it).
To the best of anyones knowledge, strong ciphers such as AES (despite misgivings about its NIST certification) and OpenVPN (with perfect forward secrecy) remain secure. As Bruce Schneier, encryption specialist at Harvards Berkman Center for Internet and Society, and privacy advocate famously stated,
"Trust the math. Encryption is your friend. Use it well, and do your best to ensure that nothing can compromise it. Thats how you can remain secure even in the face of the NSA."
Remember, too, that the NSA is not the only potential adversary out there. However, most criminals (and even governments) have nowhere near the NSA's ability to circumvent encryption.
To ensure your internet is encrypted, you'll want to visit our guide to the best VPNs in 2024.
The importance of end-to-end encryption
End-to-end (e2e) encryption is a method where you encrypt data on your own device. Only you hold the encryption keys, unless you share them, and potential adversaries will find it incredibly difficult to decrypt your data without these keys.

A lot of services and products don't use e2e encryption. Instead, they encrypt your data and hold the keys on your behalf. This is pretty convenient, seeing as it allows for easy recovery of lost passwords and syncing across devices, but it also means that these third parties could be compelled to hand over your encryption keys.
Microsoft is a great case in point. It encrypts all emails and files held in OneDrive (formerly SkyDrive), but also holds the encryption keys. In 2013, it used these keys to unlock the emails and files of its 250 million users to facilitate inspection by the NSA.
We'd strongly suggest avoiding services that encrypt your data on their servers. Always encrypt your own data on your own machine wherever you can, and visit our guide to secure cloud services if this isn't an option for you.
HTTPS
Implementing strong encryption has become somewhat trendy recently, but websites have actually been using end-to-end encryption for the last 20 years. After all, if the web wasn't secure, then we wouldn't be able to shop online or access our banking accounts.
HTTPS is the protocol of choice for most sites, and this stands for HTTP Secure (or HTTP over SSL/TLS). It's used by websites that need to secure user communications, and is known as the backbone of internet security.
Data is transferred unencrypted when you visit a non-secure HTTP website, however. This means that anyone watching can snoop on your activity on the site, including transaction details when making payments! It's even possible to alter the data transferred between you and the web server.
With HTTPS, a cryptographic key exchange occurs when you first connect to the website. All subsequent actions on the website are encrypted, and thus hidden from prying eyes. Anyone watching can see that you've visited a certain site but not the individual pages you read or the data transferred.
For example, the ProPrivacy website is secured with HTTPS. Unless you're using a VPN whilst on our site, your ISP will be able to see that you've visited it, but won't be able to tell that you're reading this particular article. This is because HTTPS uses end-to-end encryption.
It's easy to tell if the website you visit is secured by HTTPS – just look for a locked padlock icon to the left of the main URL/search bar.
There are issues relating to HTTPS but, in general, it's secure. If it wasn't, none of the billions of financial transactions and personal data transfers that happen every day would be possible. The internet itself (and possibly the world's economy) would collapse overnight.
Metadata
A more concerning limitation of encryption is that it does not necessarily protect users from the collection of metadata.
Even if the actual contents of an email, voice conversation, or browsing session cannot easily be monitored, knowing when, where, from whom, to whom, and how regularly such communication takes place can tell an adversary a great deal. It's a powerful tool in the wrong hands.
Take a securely encrypted messaging service – like WhatsApp. Facebook will still be able to tell who you're messaging when you use the service, as well as how often you message them, how long you usually chat for, and other factors.
Metadata is so powerful that collecting it has become the primary concern of the NSA (besides targeting individual communications.) As NSA General Counsel Stewart Baker openly acknowledged:
"Metadata absolutely tells you everything about somebodys life. If you have enough metadata, you dont really need content."
Technologies like VPNs and Tor browser can make collecting metadata more difficult, however. An ISP simply can't scoop up metadata relating to the browsing history of VPN customers using the service to hide their activity, after all.
Note, though, that some VPN providers log some metadata themselves. This is something to take into consideration when picking out a provider to protect your privacy.
It's also worth noting that mobile apps typically bypass any VPN running on your device and connect directly to their publishers' servers. Using a VPN, for example, won't prevent WhatsApp sending metadata to Facebook.
For more information about the VPNs we recommend for mobile devices, head on over to our best VPN for iPhone guide or best VPN for Android equivalent, where we go into more detail.
Identify your threat model
When considering how to protect your privacy and stay secure on the internet, carefully consider who or what worries you most. Defending yourself against everything is almost impossible. And any attempt to do so will likely seriously degrade the usability (and your enjoyment) of the internet.
Use FOSS software
 The terrifying scale of the NSAs attack on public cryptography, and its deliberate weakening of common international encryption standards, has demonstrated that no proprietary software can be trusted. This even includes software specifically designed with security in mind.
The terrifying scale of the NSAs attack on public cryptography, and its deliberate weakening of common international encryption standards, has demonstrated that no proprietary software can be trusted. This even includes software specifically designed with security in mind.
The NSA has co-opted (or coerced) hundreds of technology companies into building backdoors into their programs, or otherwise weakening security to allow them access. Companies in the US and UK are particularly suspect, although reports make it clear that companies around the world have conceded to NSA demands.
The problem with proprietary software is that the NSA has no issue approaching and convincing the sole developers and owners to play ball. In addition, their source code is often kept secret, making it much easier to add to or modify it without anyone else noticing.

A solution to this problem is to stick to free open-source software (FOSS). Often jointly developed by disparate and otherwise unconnected individuals, anyone can examine and peer-review FOSS source code. This minimizes the chance of someone tampering with it.
Ideally, this code should also be compatible with other implementations in order to reduce the possibility of a backdoor being built in.
It is, of course, possible that NSA agents have infiltrated open-source development groups and introduced malicious code without anyones knowledge. In addition, the sheer amount of code involved in these projects can be difficult to peer-review in its entirety.
Despite these potential pitfalls, FOSS remains the most reliable and tamper-proof software available. If you're serious about privacy, you should do your best to use it exclusively (and try out FOSS operating systems like Linux).
And if you're already a Linux user, you'll want to check out our best VPNs for Linux guide for additional tips on how to stay secure.
Steps you can take to improve your privacy
With the proviso that nothing is perfect, and that if "they" really want to get you "they" probably can, there are still steps you can take to improve your privacy.
Pay for stuff anonymously
You can vastly improve your digital privacy by paying for goods anonymously. Obviously, when it comes to physical goods delivered to an actual address, this isn't going to happen – but it's a different story with online services.
More and more services are accepting Bitcoin payments, too. A few VPNs, such as VPN service Mullvad, will even accept cash sent anonymously by post. If you're interested in learning more, check out our guide to the best VPNs for Bitcoin where we look at some of the providers that support crypto payments.

Bitcoin
Bitcoin is a decentralized and open-source virtual currency that operates using peer-to-peer technology (much as BitTorrent and Skype). As a result, the concept doesn't require a middleman to work (like a state-controlled bank).
However, Bitcoin's rise to legitimacy in the last few years has come at a cost to privacy. While major banks and even some small nation states will trade in Bitcoin, most bitcoin vendors and coin exchanges now require the user to pass a "Know Your Customer" process similar to those required by financial institutions. Handing over your photo ID to a third party does somewhat dampen the appeal of Bitcoin as a currency for privacy protection.
There are several ways to bypass this issue. Some users use coin tumblers to mitigate Bitcoin's public blockchain, and others have switched to cryptocurrency projects with a greater focus on privacy. The most mature cryptocurrency in the space is currently Monero, which boasts a privacy and anonymous blockchain for payments.
Tor vs VPN
Tor is a vital tool for internet users who require maximum possible anonymity. VPNs, however, are a much more practical privacy tool for day-to-day internet use.
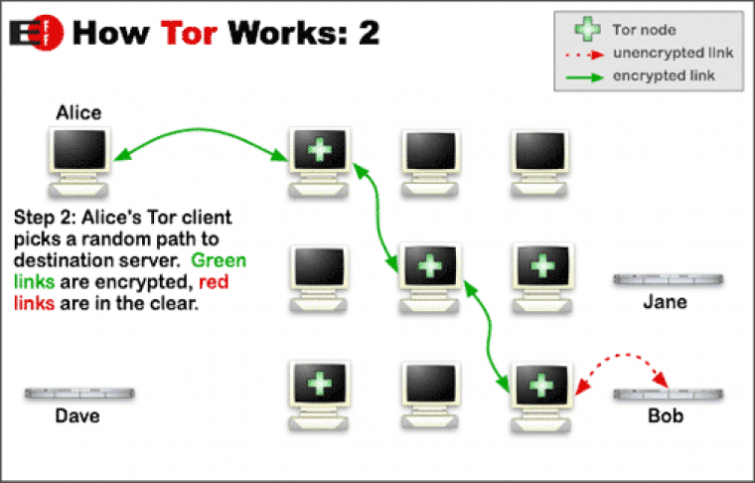
Tor can also be a handy anti-censorship tool. However, many governments go to great lengths to counter this by blocking access to the network (with varied success). Unfortunately, even identifying that someone is using the Tor network is a red flag to a network administrator working for a repressive government.
So, if you want to use Tor for journalism or whistleblowing, it's important to hide your use of the network altogether. In this case, it is possible to use Tor and a VPN together to provide meaningful security benefits.
Other ways to stay private online
VPN and Tor are the most popular ways to maintain anonymity and evade censorship online, but there are other options. Proxy servers, in particular, are quite popular. In my opinion, however, they are inferior to VPN services.
Other services which may be of interest include JonDonym, Lahana, I2P, and Psiphon. You can combine many such services with Tor and/or a VPN for even greater security.
Secure your web browsing
 Its not just the NSA who are out to get you: advertisers are too! They use some sneaky tactics to follow you around the web and build up a profile in order to sell you stuff... or to sell this information to others who want to sell you stuff.
Its not just the NSA who are out to get you: advertisers are too! They use some sneaky tactics to follow you around the web and build up a profile in order to sell you stuff... or to sell this information to others who want to sell you stuff.
Most folks with some security know-how are aware of HTTP cookies and how to clear them. Modern browsers also have a Private Browsing mode that blocks these cookies and prevents the browser from saving your internet history.
Whilst it's a good idea to use a Private Browsing mode, it's not enough to stop organizations from tracking you across the internet – your browser leaves other traces as it goes.
You can use our third party tracking tool to figure out which websites are tracking you.
Clear cached DNS entries
To speed up internet access, your browser caches the IP address it receives from your default DNS server (see the section on changing your DNS server later).
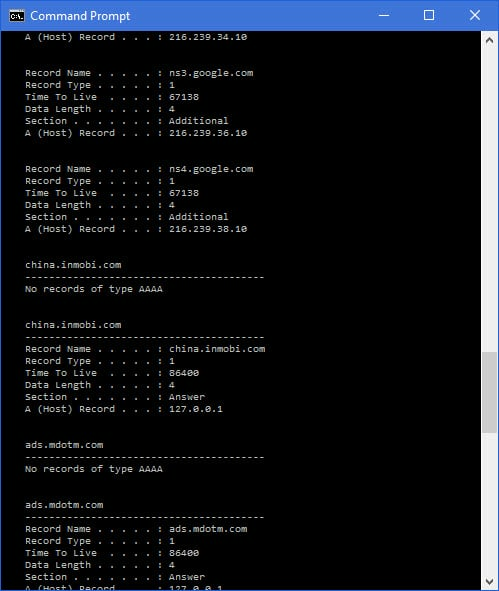
In Windows, you can see cached DNS information by typing "ipconfig /displaydns" at the command prompt (cmd.exe).
- To clear the DNS cache in Windows, open the command prompt window and type: ipconfig /flushdns [enter]
- Clear the cache in OSX 10.4 and under by opening Terminal and typing: lookupd -flushcache [enter]
- To clear the cache in OSX 10.5 and above, open Terminal and type: dscacheutil -flushcache [enter]
Clear flash cookies
A particularly insidious development is the widespread use of Flash cookies. Disabling cookies in your browser does not always block them, although modern browsers do.
Flash cookies can track you in a similar manner to regular cookies, and they can be located and manually deleted from the following directories:
- Windows: C:Users[username]AppDataLocal\MacromediaFlash Player #SharedObjects
- macOS: [User directory] /Library/Preferences/Macromedia/Flash Player/#SharedObjects
and [User directory] /Library/Preferences/Macromedia/Flash Player/macromedia.com/support/flashplayer/sys/
A better tactic, however, is to use the CCleaner utility (available for Windows and macOS). This cleans out pesky Flash cookies with a minimum of fuss. It also cleans out a host of other rubbish that slows your computer down and leaves traces of your activity behind. To do this, you need to properly configure CCleaner.
Thanks to a growing awareness of Flash cookies, including so-called "zombie cookies" (bits of persistent Flash code which respawn regular cookies when they are modified or deleted), and the fact that most modern browsers include Flash cookies as part of their regular cookie control features, the use of Flash cookies is declining. They still represent a serious threat, however.
Other web tracking technologies
Internet companies make far too much money to take user backlash against tracking lying down. They are, therefore, deploying a number of increasingly devious and sophisticated tracking methods.
Browser fingerprinting
The way in which your browser is configured (especially the browser plugins used), together with details of your Operating System, allows you to be uniquely identified (and tracked) with a worryingly high degree of accuracy.
A particularly insidious (and ironic) aspect of this is that the more measures you take to avoid tracking (for example, by using the plugins listed below), the more unique your browser fingerprint becomes.
The best defense against browser fingerprinting is to use as common and plain vanilla an OS and browser as possible. Unfortunately, this leaves you open to other forms of attack. It also reduces the day-to-day functionality of your computer to such an extent that most of us will find the idea impractical.
The more browser plugins you use, the more unique your browser is. Drat!
Using the Tor browser with Tor disabled is a partial solution to this problem. This will help make your fingerprint look identical to all other Tor users, while still benefiting from the additional hardening built into the Tor browser.
In addition to browser fingerprinting, other forms of fingerprinting are becoming more common. The most prominent of these is canvas fingerprinting, although audio and battery fingerprinting are also possible.
HTML5 web storage
Built into HTML5 (the much-vaunted replacement to Flash) is web storage, also known as DOM (Document Object Model) storage. Creepier and much more powerful than cookies, web storage is an analogous way of storing data in a browser.
It is much more persistent, however, and has a much greater storage capacity. It also cannot normally be monitored, read, or selectively removed from your web browser. And remember:
- All browsers enable web storage by default, but you can turn it off in Firefox and Internet Explorer.
- Firefox users can also configure the BetterPrivacy add-on to remove web storage automatically on a regular basis. Chrome users can use the Click&Clean extension.
- Using these add-ons will increase your browser fingerprint uniqueness.
Tracking tags
Lots of social media sites append their URL with what looks like a bunch of junk, but this is actually a unique tag that gives analytic insights to a business. This string of characters should be stripped out whenever you share a link with other people or third parties, however. Why? Well, because the URL often exposes information about the provenance of the link, as well as unique tracking tags that allow analytics to begin profiling who clicked on the link by using referral data – and that's deeply invasive.
ETags
Part of HTTP, the protocol for the World Wide Web, ETags are markers used by your browser to track resource changes at specific URLs. By comparing changes in these markers with a database, websites can build up a fingerprint, which can then be used to track you.
ETags can also be used to respawn (zombie-style) HTTP and HTML5 cookies. And once set on a site, associate companies can use them to track you as well.
This kind of cache tracking is virtually undetectable, so reliable prevention is very hard. Clearing your cache between each website you visit should work, as should turning off your cache altogether.
These methods are arduous, however, and will negatively impact your browsing experience. The Firefox add-on Secret Agent prevents tracking by ETags, but, again, will probably increase your browser fingerprint (or because of the way it works, maybe not).
History stealing
Here's where things get really scary. History stealing (also known as history snooping) exploits the very design of the web – and allows a website you visit to discover your past browsing history.
The bad news is that this information can be combined with social network profiling to identify you. It's also almost impossible to prevent.
The only good news here is that social network fingerprinting, while scarily effective, is not reliable. If you mask your IP address with a good VPN (or Tor) then you will be taking a significant step towards disassociating your real identity from your tracked web-behavior.
Privacy-enhancing browser extensions
Pioneered by Firefox, all modern browsers now support a host of extensions. Many of these aim to improve your privacy while surfing the internet. Here's a list of my favorites – extensions that I don't think anyone should surf without:
uBlock Origin (Firefox)
A lightweight FOSS ad-blocker that does double duty as an anti-tracking add-on. Chrome and Internet Explorer/Edge users can instead use Ghostery. Many users find this commercial software's funding model to be somewhat shady, however.
Privacy Badger (Firefox, Chrome)
Developed by the Electronic Frontier Foundation (EFF), this is a great FOSS anti-tracking add-on that works overtime as an ad-blocker. It is widely recommended to run Privacy Badger and uBlock Origin together for maximum protection.
HTTPS Everywhere (Firefox, Chrome, Opera)
Another essential tool from EFF. HTTPS Everywhere tries to ensure that you always connect to a website using a secure HTTPS connection, if one is available.
Self-Destructing Cookies (Firefox)
Automatically deletes cookies when you close the browser tab that set them. This provides a high level of protection from tracking via cookies without "breaking" websites. It also provides protection against Flash/zombie cookies and ETags, and cleans DOM storage.
NoScript (Firefox)
This is an extremely powerful tool that gives you unparalleled control over which scripts you run on your browser. However, many websites will not play ball with NoScript, and it requires a fair bit of technical knowledge to configure and tweak.
It's comparatively easier to add exceptions to a whitelist, but even this requires some understanding of the risks that might be involved. Not for the layperson then, but for web-savvy power-users, NoScript is difficult to beat. ScriptSafe for Chrome performs a similar job.
That last one is particularly worth paying attention to. It's worth keeping NoScript installed even if you "Allow Scripts Globally" as this still protects against nasty things such as cross-site scripting and clickjacking.
uMatrix (Firefox, Chrome, Opera)
Developed by the team behind uBlock Origin, uMatrix is something of a half-way house between that add-on and NoScript. It provides a great deal of customizable protection, but requires a fair bit of work and know-how to set up correctly.
Note that if you use either NoScript or uMatrix then it is unnecessary to also use uBlock Origin and Privacy Badger.
In addition to these extensions, most modern browsers (including mobile ones) include a Do Not Track option. This instructs websites to disable tracking and cross-site tracking when you visit them.
It is definitely worth turning this option on. However, implementation is purely voluntary on behalf of website owners, so it's no guarantee of privacy. You should also be aware that using any browser plugin increases the uniqueness of your browser. This makes you more susceptible to being tracked by browser fingerprinting.
Block "Reported Attack Sites" and "Web Forgeries" in Firefox
These settings are useful for protecting against malicious attacks, but also impact your privacy by sharing your web traffic in order to work. If these tracking issues outweigh the benefits in your opinion, you'll want to disable them.
Mobile browser security
The above extension list concentrates on desktop browsers. It is just as important to protect our browsers on smartphones and tablets.
Unfortunately, most mobile browsers have a great deal of catching-up to do in this regard. Many Firefox extensions, however, will work on the mobile version of the browser. These include:
- uBlock Origin
- HTTPS Everywhere
- Self-Destructing Cookies
To install these add-ons in Firefox for Android or Firefox for iOS, visit Options ->Tools -> Add-ons -> Browse all Firefox Add-ons, and then input your search.
Thankfully, Private Browsing, Do Not Track, and advanced cookie management are becoming increasingly commonplace on all mobile browsers.
Use a search engine that doesn't track you
Most search engines, including Google (in fact, particularly Google), store information about you. This includes:
- Your IP address.
- Date and time of search queries.
- Query search terms.
- Cookie ID; this cookie is deposited in your browsers cookie folder, and uniquely identifies your computer. With it, a search engine provider can trace a search request back to your computer.
The search engine usually transmits this information to the requested web page. It also transmits it to the owners of third-party advertising banners on that page. As you surf the internet, advertisers build up a (potentially embarrassing and highly inaccurate) profile of you.
This is then used to target adverts tailored to your theoretical needs.
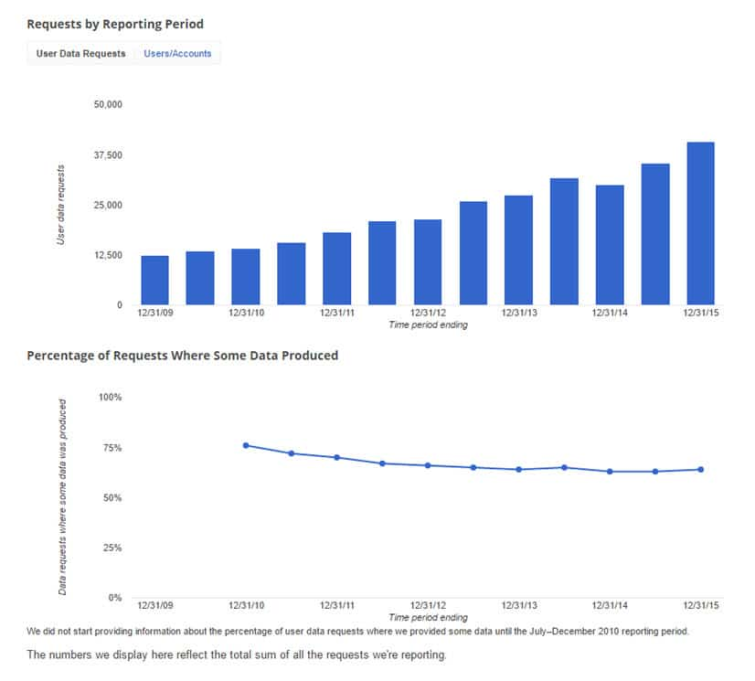
In addition to this, governments and courts around the world regularly request search data from Google and other major search engines. You can bet that this is duly handed over, too. For more details, see the Google Transparency Report on the number of User Data Requests received, and the number (at least partially) acceded to.
There are some search engines, however, that do not collect users' data. These include:
DuckDuckGo
One of the best-known private search engines, DuckDuckGo pledges not to track its users. Each search event is anonymous. While an infiltrator could track these search queries in theory, there is no profile attached for them to access.

DuckDuckGo says that it would comply with ordered legal requests, but as it doesnt track users, "there is nothing useful to give them." I've enjoyed using DuckDuckGo over the years, and through the use of "bangs", it can also search other popular search engines anonymously.
Unfortunately, many users do not find DDGs search results to be as good as those returned by Google. The fact that it is a US-based company is also a concern for some.
StartPage
Another popular Google alternative is StartPage; a Netherlands-based browser that returns Google search engine results. StartPage anonymizes these Google searches and promises not to store or share any personal information or use identifying cookies.
Ixquick
Maintained by the same people who run StartPage, Ixquick returns results from a number of other search engines, but not Google. These searches are as private as those made through StartPage.
YaCy
The above search engines rely on trusting the search engine providers to maintain your anonymity. If this worries you, then you might consider YaCy. It is a decentralized, distributed search engine built using P2P technology.
This is a fantastic idea, and one that I really hope takes off. For now, however, it is more of an exciting curiosity than a fully-fledged and useful Google alternative.
To see some other alternatives, check out our list of the best private search engines.
The filter bubble
An added benefit of using a search engine that does not track you is that it avoids the "filter bubble" effect. Most search engines use your past search terms (and things you "like" on social networks) to profile you. They can then return results they think will interest you.
This can produce a filter bubble – only showing you search results in line with your point of view. You won't get to see alternative viewpoints or opinions because they'll be downgraded in your search results.
This denies you access to the rich texture and multiplicity of human input. It is also very dangerous, as it can confirm prejudices and prevent you from seeing the "bigger picture."
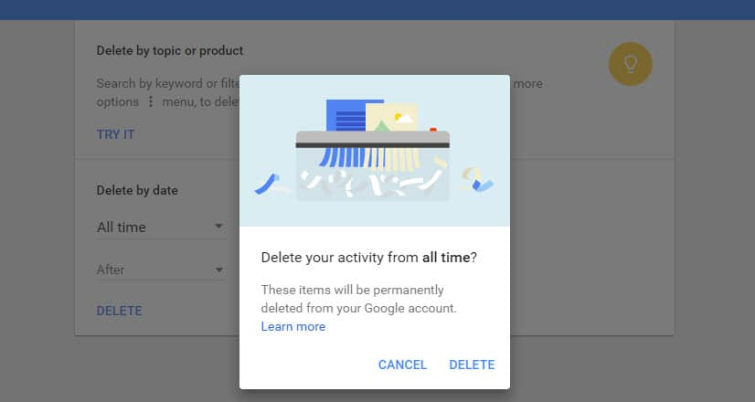
Delete your Google history
You can view the information Google collects about you by signing in to your Google account and visiting My Activity. From here you can also delete items by topic or product. Since you're reading this privacy guide, you'll probably want to Delete -> All time.
Of course, we only have Google's word that they really delete this data. But it certainly cant hurt to do this!
In order to prevent Google contintuing to collect new information about you, visit Activity Controls.
These measures wont stop someone who is deliberately spying on you from harvesting your information. However, it will help put a stop to Google's profiling.
Even if you plan on checking out one of the "no tracking" services listed above, most of us have built up a substantial Google History already, which anyone reading this article will probably want to delete.
Of course, deleting and disabling your Google history will mean that many Google services which rely on this information to deliver their highly personalized magic will either cease to function, or not function as well.
Want to have some fun? You can skew the picture that Google is building about you using our Ruin my Search History tool.
Secure your email
Most email services provide a secure HTTPS connection, and Google has even led the way in fixing the main weakness in SSL implementation. They are therefore secure email services. However, this is no good if the email service simply hands over your information to an adversary, as Google and Microsoft did with the NSA!
The answer lies in end-to-end email encryption. This is where the sender encrypts the email, and only the intended recipient can decrypt it. The biggest problem with using an encrypted email system is that you cannot impose it unilaterally. Your contacts – both recipients and senders – also need to play ball for the whole thing to work.
Trying to convince your granny to use PGP encryption will likely just lead to bafflement. Meanwhile, trying to convince your customers to use it might make many of them suspicious of you!
PGP
Most people regard Pretty Good Privacy (PGP) as the most secure and private way to send and receive emails. Unfortunately, PGP is not easy to use. At all.
This has resulted in a very low number of people willing to use PGP (basically just a few crypto-geeks).
With PGP, only the body of a message is encrypted, but the header, recipient, send time, and so forth, is not. This metadata can still be very valuable to an adversary, even if they cant read the actual message.
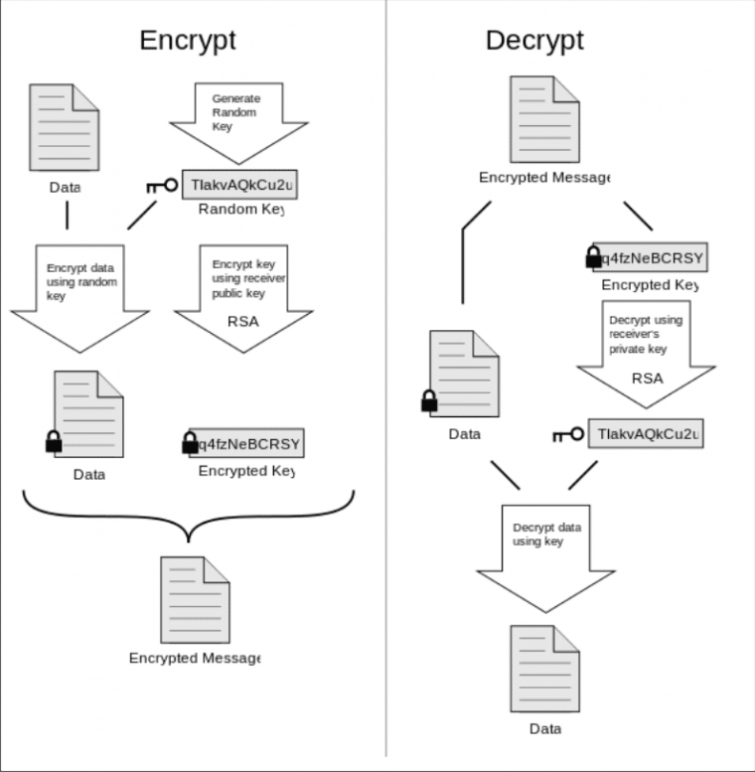
Despite its limitations, PGP remains the only way to send emails securely.
GNU Privacy Guard
PGP was once open-source and free, but is now the property of Symantec. The Free Software Foundation has taken up the open source OpenPGP banner, however, and with major funding from the German government has released GNU Privacy Guard (also known as GnuPG or just GPG).
GnuPG is a free and open source alternative to PGP. It follows the OpenPGP standard and is fully compatible with PGP, and is available for Windows, macOS, and Linux. When referring to PGP, most people these days (including myself) mean GnuPG.
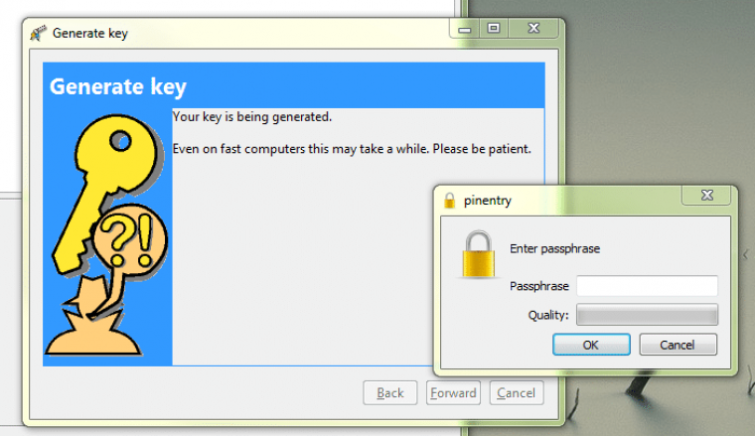
Generating a PGP key pair in Gpgwin
Although the basic program uses a simple command-line interface, more sophisticated versions are available for Windows (Gpg4win) and Mac (GPGTools). Alternately, EnigMail adds GnuPG functionality to the Thunderbird and SeaMonkey stand-alone email clients.
PGP on mobile devices
Android users should be pleased to know that an Alpha release GnuPG: Command-Line from the Guardian Project is available.
K-9 Mail is a well-regarded email client for Android with PGP support built in. It can be combined with Android Privacy Guard to provide a more user-friendly PGP experience. iOS users can give iPGMail a try.
Use PGP with your existing webmail service
PGP is a real pain to use. Such a big pain, in fact, that few people bother. Mailvelope is a browser extension for Firefox and Chrome that allows end-to-end PGP encryption within your browser.
It works with popular browser-based webmail services such as Gmail, Hotmail, Yahoo! and GMX. It makes using PGP about as painless as it gets. However, it is not as secure as using PGP with a dedicated email client.
Use a dedicated encrypted webmail Service
Encrypted webmail services with a privacy focus have proliferated over the last two years. The most notable of these are ProtonMail and Tutanota. These are much easier to use than PGP and, unlike PGP, hide email metadata. Both services now also allow non-users to securely reply to encrypted emails sent to them by users.
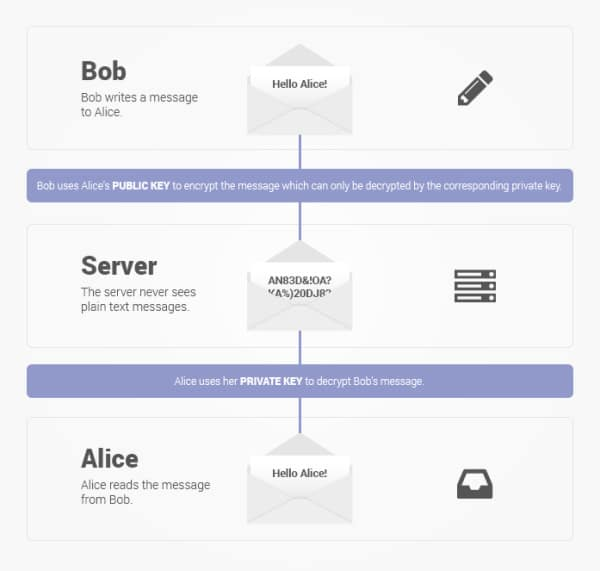
Protonmail is much more secure than most webmail services.
Unfortunately, to work, both ProtonMail and Tutanota implement encryption within the browser using JavaScript. This is fundamentally insecure.
The bottom line with such services is that they are as easy to use as Gmail, while being much more private and secure. They also won't scan your emails to sell you stuff. However, never regard them as being anywhere near as secure as using PGP with a stand-alone email program.
Other email privacy precautions
If you're solely interested in protecting files, you can encrypt these before sending them by regular email.
It is also possible to encrypt stored emails by encrypting the email storage folder using a program such as VeraCrypt (which I'll discuss later).
At the end of the day, emails are an outdated communications system and fundamentally broken when it comes to privacy and security. End-to-end encrypted VoIP calls and instant messaging are much more secure ways of communicating online.
Secure your voice conversations
 Regular phone calls (landline and mobile) are never secure, and you can't change this. It's not just the NSA and GCHQ you have to worry about, either. Governments everywhere are keen on recording citizens' phone calls.
Regular phone calls (landline and mobile) are never secure, and you can't change this. It's not just the NSA and GCHQ you have to worry about, either. Governments everywhere are keen on recording citizens' phone calls.
Unlike emails and internet use, which can be obfuscated (as this article tries to demonstrate), phone conversations are always wide open.
Even if you buy anonymous and disposable "burner phones" (behavior which marks you out as either worryingly paranoid or engaged in highly criminal activity), a lot of information can be gathered through the collection of metadata.
Burner phones are also totally pointless unless the people you're calling are equally paranoid and also using burner phones.
VoIP with end-to-end encryption
If you want to keep your voice conversations completely private, then you need to use VoIP with end-to-end encryption (except, of course, when talking in person).
VoIP (Voice over Internet Protocol) apps allow you to talk securely over the internet. It'll often also allow you to make video calls and send instant messages. VoIP services allowing cheap or free calls anywhere in the world have thus become extremely popular. Skype, in particular, is now a household name.
Unfortunately, Skype is owned by Microsoft and has perfectly demonstrated the problem with most such services (a problem they share with emails). VoIP connections to and from a middleman may be secure, but if the middleman just hands over your conversations to the NSA or some other government organization, this security is next to meaningless.
So, as with email, what is needed is end-to-end encryption where an encrypted tunnel is created directly between the participants in a conversation. And no-one else.
Good Skype alternatives
Signal is available for Android and iOS, and in addition to being probably the most secure Instant Messaging (IM) app available, it also allows its users to make secure VoIP calls.
As with messaging, Signal leverages your regular address book. If a contact also uses Signal, then you can start an encrypted VoIP conversation with them. If a contact does not use Signal, then you can either invite them to use the app, or talk with them using your regular insecure cellular phone connection.
The encryption Signal uses for VoIP calls is not as strong as the encryption it uses for text messaging. This is probably due to the fact that encrypting and decrypting data uses processing power, so stronger encryption would negatively impact the quality of calls.
Your threat model may vary
For most purposes, this level of encryption should be more than sufficient. If you need higher levels of privacy, however, you should stick to text messaging.
Jitsi (Windows, macOS, Linux, Android) is a free and open-source software offers all the functionality of Skype. Except everything is encrypted using ZRTP. This includes voice calls, videoconferencing, file transfers, and messaging.
The first time you connect to someone, it can take a minute or two to set up the encrypted connection (designated by a padlock). But the encryption is subsequently transparent. As a straight Skype replacement for the desktop, Jitsi is difficult to beat.
For more information, check out our list of secure video conferencing apps (AKA Zoom alternatives).
Secure your text messages
There's plenty of crossover here with our previous section on VoIP. Plenty of VoIP services, including Signal and Jitsi, also offer built-in chat and IM functionality.
Signal (Android, iOS), developed by crypto-legend Moxie Marlinspike, is widely regarded as the most secure text messaging app on the market. It's not without its issues, but Signal is as good as it gets when it comes to having a secure and private conversation.
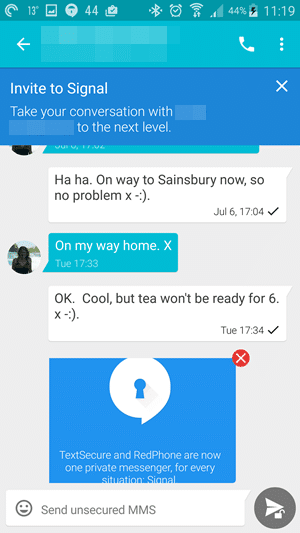
Signal replaces your phones default text messaging app and uses your regular contact list. If a contact also uses Signal, then any messages sent to or received from them are securely end-to-end encrypted.
If a contact does not use Signal, then you can invite them to use the app or send an unencrypted text message via regular SMS. The beauty of this system is that Signal is almost transparent in use, which should make it easier to convince friends, family, and colleagues to give it a go.
For more information, check out our full Signal messenger review.
Jitsi (Windows, macOS, Linux, Android (experimental)) is a great desktop messenger app, and is very secure. It is almost certainly not quite as secure as Signal, however.
A note on WhatsApp
The very popular WhatsApp app now uses the same end-to-end encryption developed for Signal. Unlike Signal, however, WhatsApp (owned by Facebook) retains metadata and has other weaknesses not present in the Signal app.
Despite these issues, most of your contacts likely use WhatsApp and are unlikely to be convinced to switch to Signal. Given this all-too-common situation, WhatsApp provides vastly improved security and privacy that your contacts might actually use.
Unfortunately, this argument has been undermined by a recent announcement that WhatsApp will start sharing users' address books with its parent company Facebook by default. This can be disabled, but the vast majority of users will not bother to do so.
Facebook is just the tip of the iceberg, however. Find out how other social media platforms track you with our social media privacy index.
Ditch the cell phone!
Whilst we're on the subject of phones, I should also mention that your every movement can be tracked as you carry yours around. And not just by the usual culprits like GPS and Google Now/Siri.
Phone towers can easily track even the most modest cell phone. In addition to this, use of Stingray IMSI-catchers has proliferated among police forces the world over.
These devices mimic cell phone towers. They can not only uniquely identify and track individual cell phones, but can intercept phone calls, SMS messages, and unencrypted internet content.
Using an end-to-end encrypted messaging app such as Signal will prevent this interception. However, if you dont want to be uniquely identified by your phone and tracked, the only real solution is to leave your phone at home.
Secure your cloud storage
As internet speeds increase, server-level storage becomes cheaper, and the different devices we use to access the internet become more plentiful, it is becoming increasingly clear that cloud storage is the future.
The problem, of course, is ensuring that files stored in the "the cloud" remain secure and private – and the big players have proven themselves woefully inadequate. Google, Dropbox, Amazon, Apple, and Microsoft have all worked in cahoots with the NSA. They also reserve the right to investigate your files and hand them over to the authorities if they receive a court order – and this is outlined in the terms and conditions.
To ensure that your files are secure in the cloud, there are a number of approaches you can take.
Manually encrypt your files before uploading them to the cloud
The simplest and most secure method is to manually encrypt your files using a program such as VeraCrypt or EncFS. This has the advantage of allowing you to continue using your favorite cloud storage service, no matter how inherently insecure it is, as you'll hold all the encryption keys to your files.
As discussed later, mobile apps that can handle VeraCrypt or EncFS files exist, allowing for synchronization across devices and platforms. Features such as file versioning will not work with individual files as the encrypted container hides them, but it is possible to recover past versions of the container.
If you're in the market for a good Dropbox alternative, you may like to check out our best secure backups list.
Use an automatically encrypted cloud service
These services automatically encrypt files before uploading them to the cloud. Avoid any service that encrypts files server-side, as these are vulnerable to being decrypted by the service provider.
Any changes to files or folders sync with locally decrypted versions before being secured and sent to the cloud.
All services listed below have iOS and Android apps, so you can easily sync across your computers and mobile devices. This convenience comes at a small security price, as the services briefly store your password on their servers to authenticate you and direct you to your files.
- TeamDrive - this German cloud backup and file synchronization service is primarily aimed at businesses. However, it also offers free and low-cost personal accounts. TeamDrive uses proprietary software, but has been certified by the Independent Regional Centre for Data Protection of Schleswig-Holstein.
- Tresorit- is based in Switzerland, so users benefit from the countrys strong data protection laws. It provides client-side encryption, although user data is stored on Microsoft Windows Azure servers. Given widespread distrust of all things US, this is an odd choice. But as client-side encryption ensures the cryptographic keys are kept with the user at all times, it shouldn't be a problem.
- SpiderOak - available for all major platforms, SpiderOak offers a "zero knowledge," secure, automatically encrypted cloud service. It uses a combination of 2048-bit RSA and 256-bit AES to encrypt your files.
Note that all of these cloud services are closed source. This means that we just have to trust them to do what they claim to do (although TeamDrive has been independently audited).
Use Syncthing for cloudless syncing
Syncthing is a secure decentralized peer-to-peer (P2P) file synchronization program that can sync files between devices on a local network or over the internet.
Acting more or less as a Dropbox replacement, Syncthing synchronizes files and folders across devices, but does so without storing them in the cloud. In many ways, it is therefore similar to BitTorrent Sync, except that it's completely free and open-source (FOSS).
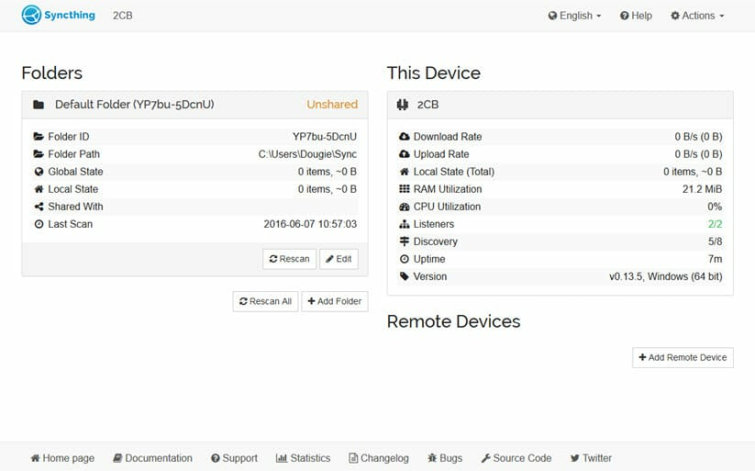
Syncthing allows you to securely backup data without the need to trust a third-party cloud provider. Data is backed up to a computer or server that you control directly, and is at no point stored by a third party.
This is referred to in techie circles as a "BYO (cloud) model," where you provide the hardware instead of a third-party commercial vendor. The encryption used is also fully end-to-end, as you encrypt it on your device and only you can decrypt it. Nobody else holds the encryption keys.
A limitation of the system is that, as it is not a true cloud service, it cannot be used as an extra drive by portable devices with limited storage. On the plus side, however, you are using your own storage, and so are not tied to cloud providers data limits (or charges).
Encrypt your local files, folders, and drives
While the focus of this guide is on internet security and privacy, an important aspect of securing your digital life is to ensure that locally stored files cannot be accessed by unwanted parties.
Of course, it's not just about local storage. You can also encrypt files before emailing them or uploading them to cloud storage.
VeraCrypt
Windows, Mac macOS, Linux. Mobile support for VeraCrypt containers is available via third-party apps.
VeraCrypt is an open source full-disk encryption program. With VeraCrypt you can:
- Create a virtual encrypted disk (volume) which you can mount and use just like a real disk (and can be made into a Hidden Volume).
- Encrypt an entire partition or storage device (for example, a hard drive or USB stick).
- Create a partition or storage drive containing an entire operating system (which can be hidden).
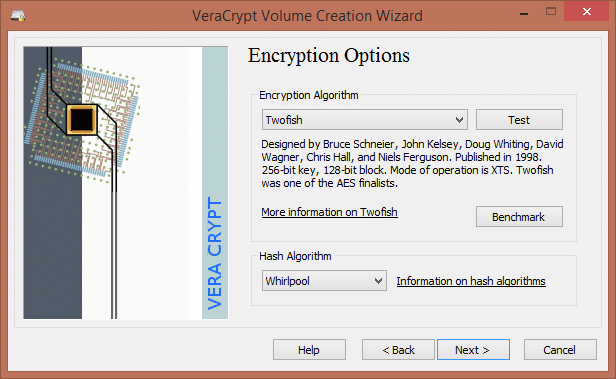
All encryption is performed on-the-fly in real time, making VeraCrypt transparent in operation. The ability to create hidden volumes and hidden operating systems provides plausible deniability, as it should be impossible to prove they exist (as long as all the correct precautions are taken).
AES Crypt
Windows, macOS, Linux (Crypt4All Lite for Android is compatible).
This nifty little cross-platform app is handy for encrypting individual files. Although only individual files can be encrypted, this limitation can be overcome somewhat by creating zip files out of folders, and then encrypting the zip file with AES Crypt.
Full disk encryption on mobile devices
All new iPhones and iPads now ship with full disk encryption. Some Android devices do as well. If not, you can manually turn it on. Please see our guide to encrypting your Android phone for more details.
Use anti-virus/anti-malware and firewall software
Anti-virus software
Note: ProPrivacy has dedicated to guides anti-virus software – we recommend starting with our best anti virus software list. Now, back to the guide...
It almost goes without saying, but as this is an "ultimate guide", Ill say it anyway:
Always use anti-virus software, and make sure that it's up-to-date!
Viruses can wreak havoc with your system and allow hackers in. They'll have access to all your (unencrypted) files and emails, webcam, passwords stored in Firefox (if no master password is set), and much more. Keyloggers are particularly dangerous, as they can be used to access bank details and track pretty much everything you do on your computer.
It's also worth remembering that it's not just criminal hackers who use viruses! The Syrian government, for example, launched a virus campaign known as Blackshade aimed at ferreting out and spying on political dissidents.
Most people are aware they should be using anti-virus software on their desktop computers, but many neglect their mobile devices. While there are fewer viruses targeting mobile devices at present, smartphones and tablets are sophisticated and powerful computers. As such, they are vulnerable to attack by viruses and need to be protected.
Mac users famously neglect anti-virus software, citing the "fact" that macOSs Unix architecture makes virus attacks difficult. This an illusion, however. Macs are not immune to viruses, and anyone serious about their security should always use good anti-virus software.
Free vs. paid-for anti-virus software
The agreed consensus is that free antivirus software is as good at preventing viruses as paid-for alternatives – but paid-for software provides better support and more comprehensive "suites" of software. These are designed to protect your computer from a range of threats by combining anti-virus, anti-phishing, anti-malware, and firewall functions.
Similar levels of protection are available for free but require the use of various different programs. Also, most free software is for personal use only, and businesses are usually required to pay for a license. A bigger concern, however, is how publishers can afford to offer free anti-virus products. AVG, for example, can sell users' search and browser history data to advertisers in order to "make money" from its free anti-virus software.
Although I recommend free products (as most major anti-virus products have a free version), it may therefore be a very good idea to upgrade to a premium version of the software if you have the means.
Good anti-virus software options
Windows – the most popular free anti-virus program for Windows is Avast! Users can check out free Antivirus and AVG AntiVirus Free Edition (which I recommend avoiding for the reason above). Personally, I use the built-in Windows Defender for real-time protection and run a weekly manual scan using Malwarebytes Free. A paid-for version of Malwarebytes is also available that'll run scans automatically, plus provide real-time protection. If you want to know more, check out our best anti virus guide for Windows 10.
macOS– Avast! Free Antivirus for Mac is well regarded, although other decent free options are available. In fact, free software is better regarded than paid-for options, so I recommend saving your cash! For more information, see our best anti virus apps for Mac.
Android – again, there are a number of options, both free and paid for. I use Malwarebytes because it is nice and lightweight. Avast! is more fully-featured, however, and includes a firewall. Find out more with our best anti-virus apps for Android guide.
iOS – Apple is still in denial about the fact that iOS is as vulnerable to virus attacks as any other platform. Indeed, in a move that is as alarming as it is bizarre, it seems that Apple has purged the Store of anti-virus apps! A VPN will help somewhat by encrypting your data and protecting you from hackers and surveillance.
Linux – the usual suspects: Avast! and Kaspersky are available for Linux. These work very well.
Firewalls
A personal firewall monitors network traffic to and from your computer. It can be configured to allow and disallow traffic based on a set of rules. In use, they can be a bit of pain, but they do help ensure that nothing is accessing your computer and that no programs are accessing the internet when they shouldnt be.
Both Windows and Mac ship with built-in firewalls. These are, however, only one-way firewalls. They filter incoming traffic but not outgoing traffic. This makes them much more user-friendly than true two-way firewalls – but much less effective, as you cannot monitor or control what programs (including viruses) already installed on your computer are doing.
The biggest problem with using a two-way firewall is determining which programs are 'ok to access the internet and which are potentially malicious. Perfectly legitimate Windows processes can, for instance, appear pretty obscure. Once set up, however, they become fairly transparent in use.
Recommended two-way firewall programs
Windows – Comodo Firewall Free and ZoneAlarm Free Firewall are free and good. Another approach is to use TinyWall. This very lightweight free program is not a firewall per se, but instead adds the ability to monitor outgoing connections to the built-in Windows Firewall.
Glasswire is also not a true Firewall because it does not allow you to create rules or filters, or block specific IP connections. What it does do is present network information in a clear manner. This makes it easy to understand what is going on, and therefore easier to make informed decisions.
macOS – Little Snitch adds the ability to monitor outgoing connections to the built-in macOS firewall. It's great, but is a little pricey at $25.
Android – as noted above, the free Avast! for Android app includes a firewall.
iOS – the only iOS firewall I know of is Firewall iP, and it requires a jailbroken device to run.
Linux – there are many Linux firewall programs and dedicated firewall distros available. iptables is bundled with just about every Linux distro, and is an extremely flexible firewall utility for anyone who cares to master it.
Those a little less fearless might prefer a more user-friendly Linux firewall such as Smoothwall Express or pfSense. Check out our pfSense VPN page for more details about how a VPN can improve security.
Miscellaneous security tips and tricks
Use Linux rather than a commercial OS
As I noted near the beginning of this guide, no commercial software can be trusted not to have a back-door built into it by the NSA.
A more secure alternative to Windows (especially Windows 10!) or macOS is Linux. This is a free and open source operating system. Note, though, that some builds incorporate components which are not open source.
It is far less likely that Linux has been compromised by the NSA. Of course, that's not to say that the NSA hasnt tried. It is a much more stable and generally secure OS than its commercial rivals.

TAILS is a secure Linux distro favored by Edward Snowden. The default browser is IceWeasel, a Firefox spinoff for Debian that has been given the full Tor Browser Bundle treatment.
Despite great strides made in the right direction, Linux, unfortunately, remains less user-friendly than either Windows or macOS. Less computer-literate users may, therefore, struggle with it.
If you are serious about privacy, however, Linux is the way forward. One of the best things about it is that you can run the entire OS from a Live CD without the need to install it. This makes it easy to try out different Linux distros. It also adds an extra layer of security when you access the internet.
This is because the OS exists completely separately from your regular OS. The temporary OS could be compromised, but as it exists only in RAM and disappears when you boot back into your normal OS, this isn't a major problem.
Example Linux distributions
There are hundreds of Linux distros out there. These range from full desktop replacements to niche distributions.
- Ubuntu – is a very popular Linux distro due to the fact that it is one of the easiest to use. There is a great deal of assistance available for it from an enthusiastic Ubuntu community. It, therefore, makes a good starting point for those interested in using a more secure operating system.
- Mint – is another popular Linux distro aimed at novice users. It's more Windows-like than Ubuntu, so Windows refugees are often more comfortable using it than Ubuntu. Mint is built on top of Ubuntu, so most Ubuntu-specific tips and programs also work in Mint. This includes VPN clients.
- Debian – Mint is based on Ubuntu and Ubuntu is based on Debian. This highly flexible and customizable Linux OS is popular with more experienced users.
- Tails – is famously is the OS of choice for Edward Snowden. It is very secure and routes all internet connections through the Tor network. It is, however, a highly specialized privacy tool. As such, it makes a poor general purpose desktop replacement to Windows or macOS.
Ubuntu, Mint, and Debian all make great, user-friendly desktop replacements to Windows and macOS. Ubuntu and Mint are widely recommended as good starting points for Linux newbies.
We go into more detail on the subject in our best Linux Distros for privacy guide, if you would like to learn more.
Think like an attacker
To get the full picture of just how much of your life is visible online, you'll need to get creative. Start with a piece of easily accessible or widely known information, such as an email address or phone number, and start searching to see where it crops up. Look at your Facebook profile from an outside account and check what's exposed. Look up your name in a reverse person search and see if you're easily identified.
Do you own a website? If so, does your Whois information expose your real name and address? Do you own a company? If so, do your results on Companies House expose your name and address? Are you registered to vote? If so, are you on the Open Register, which may expose your real name and... you get the point.
There are thousands of data points connected to both your online identity and real self, and fraudsters will leverage on the overlap between them to separate you and your money. By understanding how someone might go about retrieving that information, you gain control over where and how you expose yourself online.
Use a virtual machine (VM)
An additional level of security can be achieved by only accessing the internet (or only accessing it for certain tasks) using a 'virtual machine. These are software programs that emulate a hard drive onto which an operating system such as Windows or Linux is installed. Note that VM-ing macOS is tricky.
This effectively emulates a computer through software, which runs on top of your normal OS.
The beauty of this approach is that all files are self-contained within the virtual machine. The "host" computer cannot be infected by viruses caught inside the VM. This is why such a set-up is popular among hardcore P2P downloaders.
The virtual machine can also be entirely encrypted. It can even be "hidden," using programs such as VeraCrypt (see above).
Virtual machines emulate hardware. They run another whole OS on top of your "standard" OS. Using one therefore requires substantial overheads in terms of processing power and memory use. That said, Linux distros tend to be quite lightweight. This means that many modern computers can handle these overheads with minimal impact on perceived performance.
Popular VM software includes the free VirtualBox and VMWare Player, and the premium ($273.90) enterprise-level VMware Workstation. As noted above, VeraCrypt lets you encrypt an entire OS, or even hide its existence.
Give Whonix a try
Whonix works inside a VirtualBox virtual machine. This ensures that DNS leaks aren't possible, and that "not even malware with root privileges can find out the users real IP."
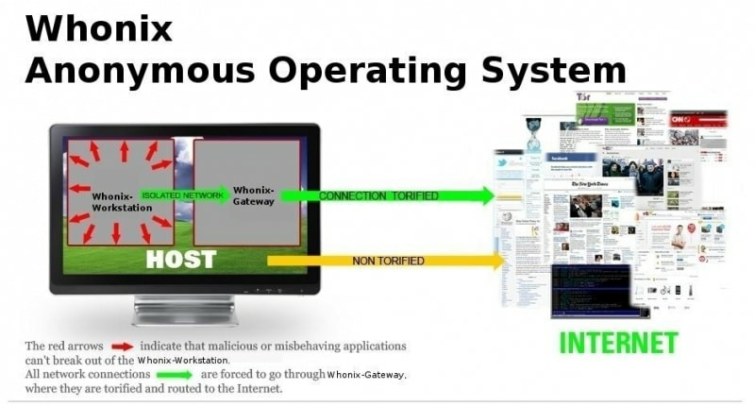
It consists of two parts, the first of which acts as a Tor gateway (known as Whonix Gateway). The second (known as a Whonix Workstation), is on a completely isolated network. This routes all its connections through the Tor gateway.
This isolation of the workstation away from the internet connection (and all isolated from the host OS inside a VM), makes Whonix highly secure.
A note on Windows 10 and 11
Windows 10 and 11 are a privacy nightmare. Even with data collection options disabled, Windows 10 continues to send a great deal of telemetry data back to Microsoft.
This situation has become even worse given the recent Anniversary Update (vers. 1607) which removed the option to disable Cortana. This is a service that collects a great deal of information about you in order to provide a highly personalized computing experience. Much like Google Now, it is useful, but achieves this usefulness by invading your privacy.
The best advice in terms of privacy is to avoid using Windows altogether and switch to Linux. You can always set up your system to dual-boot into either Linux or Windows and only use Windows when absolutely necessary. For example, when playing games, many of which only work in Windows.
If you really must use Windows, then a number of third party apps exist to help tighten up security and privacy more than Windows settings ever can. These typically get under the hood of Windows, adjusting registry settings and introducing firewall rules to prevent telemetry being sent to Microsoft.
They can be very effective. However, you are giving these programs direct access to the deepest workings of your OS. So lets just hope that their developers are honest! Use of such apps is very much at your own risk.
I use W10 Privacy. It works well but is not open source. Windows 10 Long Term Service Channel is also a viable option if you want to set and forget your privacy options, as it is designed for embedded systems that do not require regular updates over their lifecycle.
Password-protect your BIOS
 Full-disk encryption using VeraCrypt is a great way to physically secure your drives. But for this to be properly effective, it is essential to set strong passwords in BIOS for both starting up and modifying the BIOS settings. It is also a good idea to prevent boot-up from any device other than your hard drive.
Full-disk encryption using VeraCrypt is a great way to physically secure your drives. But for this to be properly effective, it is essential to set strong passwords in BIOS for both starting up and modifying the BIOS settings. It is also a good idea to prevent boot-up from any device other than your hard drive.
Disable flash
It's widely known that the Flash Player is an incredibly insecure piece of software (see also Flash Cookies). Many major players in the internet industry have made strong efforts to eradicate its use.
Apple products, for example, no longer support Flash (by default). In addition, YouTube videos are now served up using HTML5 rather than Flash.
The best policy is to disable Flash in your browser.
In Firefox, at the very least set Flash to "Ask to Activate," so you have a choice about whether to load the Flash content.
If you really must view Flash content, then I suggest doing so in a separate browser that you do not use for anything else.
Change DNS servers and secure your DNS with DNSCrypt
We are used to typing domain names that are easy to understand and remember into our web browsers. But these domain names are not the "true" addresses of websites. The "true" address, as understood by a computer, is a set of numbers known as an IP address.
The Domain Name System (DNS) is used to translate domain names to IP addresses.
By default, this translation process is performed on your ISPs DNS servers. This ensures your ISP has a record of all websites you visit.

Graffiti in Istanbul encouraging the use of Google Public DNS as an anti-censorship tactic during the governments 2014 crackdown on Twitter and YouTube.
Fortunately, there are a number of free and secure public DNS servers, including OpenDNS and Comodo Secure DNS. I prefer the non-profit, decentralized, open, uncensored and democratic OpenNIC.
I recommend changing your system settings to use one of these instead of your ISPs servers.
DNSCrypt
What SSL is to HTTP traffic (turning it into encrypted HTTPS traffic), DNSCrypt is to DNS traffic.
DNS wasn't built with security in mind, and it is vulnerable to a number of attacks. The most important of these is a "man-in-the-middle" attack known as DNS spoofing (or DNS cache poisoning). This is where the attacker intercepts and redirects a DNS request. This could, for example, be used to redirect a legitimate request for a banking service to a spoof website designed to collect victims' account details and passwords.
The open-source DNSCrypt protocol solves this problem by encrypting your DNS requests. It also authenticates communications between your device and the DNS server.
DNSCrypt is available for most platforms (mobile devices must be rooted/jailbroken), but does require support from your chosen DNS server. This includes many OpenNIC options.
DNS and VPNs
This DNS translation process is usually performed by your ISP. When using a VPN, however, all DNS requests should be sent through your encrypted VPN tunnel. They are then handled by your VPN provider instead.
Using the right scripts, a website can determine which server resolved a DNS request directed to it. This will not allow it to pinpoint your exact real IP address but will allow it to determine your ISP (unless you have changed DNS servers, as outlined above).
This will foil attempts to geo-spoof your location, and allows police and the like to obtain your details from your ISP. ISPs keep records of these things, while good VPN providers don't keep logs.
Most VPN providers run their own dedicated DNS servers in order to perform this DNS translation task themselves. If you're using a good VPN, you do not need to change your DNS server or use DNSCrypt as the DNS requests are encrypted by the VPN.
Unfortunately, DNS requests do not always get sent through the VPN tunnel like they're supposed to. This is known as a DNS leak.

Note that many VPN providers offer "DNS leak protection" as a feature of their custom software. These apps use firewall rules to route all internet traffic through the VPN tunnel, including DNS requests – and they're usually very effective.
Use secure passwords
We've all been told this often enough to make us want to pull our hair out! Use long complex passwords, using combinations of standard letters, capitals, and numbers. And use a different password for each service... Argh!
Given that many of us find remembering our own name in the morning a challenge, this kind of advice can be next to useless.
Fortunately, help is at hand!
Low-tech solutions
Here are some ideas that will vastly improve the security of your passwords and take almost no effort to implement:
- Insert a random space into your password - this simple measure greatly reduces the chance of anyone cracking your password. Not only does it introduce another mathematical variable into the equation, but most would-be crackers assume that passwords consist of one continuous word. They, therefore, concentrate their efforts in that direction.
- Use a phrase as your password - even better, this method lets you add lots of spaces and use many words in an easy-to-remember manner. Instead of having "pancakes" as your password, you could have 'I usually like 12 pancakes for breakfast" instead.
- Use Diceware - this is a method for creating strong pass phrases. Individual words in the pass phrase are generated randomly by rolling dice. This introduces a high degree of entropy into the result. Diceware pass phrases are therefore well-regarded by cryptographers. The EFF has recently introduced a new expanded Diceware word-list aimed at further improving Diceware pass phrase results.
- Use more than four numbers in your PIN - where possible, use more than four numbers for your PINs. As with adding an extra space to words, this makes the code mathematically much harder to break. Most crackers work on the assumption that only four numbers are used.
High-tech solutions
Where mortals fear to tread, software developers jump in with both feet! There are a plethora of password management programs available. My pick of the bunch are:
KeePass (multi-platform) – this popular free and open-source (FOSS) password manager will generate complex passwords for you and store them behind strong encryption. A plethora of plugins allows for all sorts of customization and increased capability.
With plugins, you can use the Twofish cipher instead of the default AES, for example, while PassIFox and chromeIPass provide full browser integration. KeePass itself is Windows only, but KeepassX is an open-source clone for macOS and Linux, as are iKeePass for iOS and Keepass2Android for Android.
Sticky Password (Windows, macOS, Android, iOS)–is a great desktop password solution that impressed me with its ability to sync over Wi-Fi and support for so many browsers.
Its security measures also appear to be very tight. Given these solid foundations, the fact that Sticky Password works brilliantly on mobile devices (especially for Firefox mobile users) may be a compelling reason to choose this over its FOSS rival.
If you would like to know more, check out our guide to secure password managers.
Social networking
 Social networks – where you're encouraged to share every random thought that comes into your head, photos of what you had for dinner, and blow-by-blow accounts of your relationship meltdown.
Social networks – where you're encouraged to share every random thought that comes into your head, photos of what you had for dinner, and blow-by-blow accounts of your relationship meltdown.
It is the antithesis of concepts such as privacy and security.
Facebook is worse than Twitter in terms of privacy, as it sells every detail of your life to profiling-hungry advertisers. It also hands your private data over to the NSA. But all social networks are inherently about sharing information.
Meanwhile, all commercial networks make a profit from harvesting your personal details; likes, dislike, places you visit, things you talk about, people you hang out with (and what they like, dislike, etc.), and then selling them.
By far the best way to maintain your privacy on social networks is to avoid them altogether. Delete all your existing accounts!
This can be tricky. It is unlikely, for example, that you will be able to remove all traces of your presence on Facebook. Even worse is that these social networks are increasingly where we chat, share photos, and otherwise interact with our friends.
They are a primary reason for using the internet and play a central role in our social lives. In short, we aren't willing to give them up.
Below, then, are some ideas for trying to keep a modicum of privacy when social networking.
Self-censorship
If there are things you don't want (or that shouldn't be) made public, don't post details about them on Facebook! Once posted, it is very difficult to retract anything you have said. Especially if it has been re-posted (or re-tweeted).
Keep private conversations private
It is all too common for people to discuss intimate details of a planned dinner date, or conversely, to have personal rows using public channels. Make use of Message (Facebook) and DM (Twitter) instead.
This won't hide your conversations from advertisers, the law, or the NSA, but it will keep potentially embarrassing interactions away from friends and loved ones.
Use aliases
There is little to stop you from using a false name. In fact, given employers almost routinely check their staff's (and potential staff's) Facebook pages, using at least two aliases is almost a must. Opt for a sensible one with your real name, which is designed to make you look good to employers, and another where friends can post wildly drunken pictures of you.
You can also happily fib about your date of birth, interests, gender, where you live, or anything else that will put advertisers and other trackers off your scent.
On a more serious note, bloggers living under repressive regimes should always use aliases (together with IP cloaking measures such as a VPN) when publishing posts that may threaten their life or liberty.
Keep checking your privacy settings
Facebook is notorious for continually changing the way its privacy settings work. It also makes its privacy policies as opaque as possible. It is worth regularly checking the privacy settings on all social networks to make sure they are as tight as possible.
Ensure that posts and photos are only shared with Friends, for example, not Friends of Friends or "Public." On Facebook, ensure that "Review posts friends tag you in before they appear on your timeline" (under Privacy Settings -> Timeline and Tagging) is set to "On". This can help limit the damage "friends" are able to do to your profile.
Avoid all Five Eyes-based services
The Five Eyes (FVEY) spying alliance includes Australia, Canada, New Zealand, the United Kingdom, and the United States. Edward Snowden has described it as a "supra-national intelligence organization that doesn't answer to the known laws of its own countries."
Intelligence is freely shared between security organizations of member countries, a practice that is used to evade legal restrictions on spying on their own citizens. It is, therefore, a very good idea to avoid all dealings with FVEY-based companies.

Indeed, there is a strong argument that you should avoid dealing with any company based in a country belonging to the wider Fourteen Eyes alliance.
The US and NSA spying
The scope of the NSA's PRISM spying program is staggering. Edward Snowden's revelations have demonstrated it has the power to co-opt any US-based company. This includes monitoring information relating to non-US citizens and pretty much anybody else in the world. It also includes monitoring all internet traffic that passes through the US's internet backbone.
Other countries' governments seem desperate to increase their own control over their citizens' data. Nothing, however, matches the scale, sophistication, or reach of PRISM. This includes China's attempts at internet surveillance.
Suggesting that every US-based company may be complicit in handing every users' personal information over to a secretive and largely unaccountable spying organization might sound the stuff of paranoid science-fiction fantasy. As recent events have proved, however, this is terrifyingly close to the truth...
A note on data
Due to provisions in both the Patriot Act and the Foreign Intelligence Surveillance Act (FISA), US companies must hand over users' data. This applies even if that user is a non-US citizen and the data has never been stored in the US.
The UK and GCHQ spying
The UK's GCHQ is in bed with the NSA. It also carries out some particularly heinous and ambitious spying projects of its own. According to Edward Snowden, "they [GCHQ] are worse than the US."
This already dire situation is about to worsen. The impending Investigatory Powers Bill (IPB) "formalizes" this covert spying into law. It also expands the UK government's surveillance capabilities to a terrifying degree with very little in the way of meaningful oversight.
I therefore strongly recommend avoiding all companies and services based in the UK.
Conclusion
Is privacy worth it?
This question is worth considering. Almost all the measures outlined above mark you for special attention from the likes of the NSA. They also add extra layers of complexity and effort to everyday tasks.
Indeed, much of the functionality of new web-based services relies on knowing a lot about you! Google Now is an excellent case in point. The "intelligent personal assistant" software's ability to anticipate what information you require is uncanny.
It can, for example, remind you that you need to leave the office to catch the bus "now" if you want to get home at your usual time. It will also provide navigation to the nearest bus stop and alternative timetables should you miss the bus.
Some of the most exciting and interesting developments in human-computer interaction rely on a full-scale invasion of privacy. To box yourself in with encryption and other privacy protection methods is to reject the possibilities afforded by these new technologies.
I pose the question of whether privacy is worth it as food for thought. Privacy comes with a cost. It's worth thinking about what compromises you are willing to make, and how far you will go, to protect it.
The importance of privacy
In my view, privacy is vitally important. Everyone has a right not to have almost every aspect of their lives recorded, examined, and then judged or exploited (depending on who is doing the recording). However, maintaining privacy is not easy and can never be completely guaranteed in the modern world.

We all want the ability to share things with our friends, and with services that improve our lives, without worrying about this information being dissected and used to profile us.
If more people make efforts to improve their privacy, it will make government agencies and advertisers' jobs more difficult. Perhaps even to the point that it could force a change of approach.
Final thoughts
It may take a bit of effort, but it is entirely possible, and not too cumbersome, to take steps that greatly improve your privacy while online. Many experts differ on the best and most effective ways to protect your online privacy in 2024, so it's important to remember that nothing is foolproof. However, that's no reason to make things easy for those who would invade aspects of your life that should rightfully be yours and yours alone.
Privacy is a precious but endangered commodity. By implementing at least some of the ideas I've covered in this guide, you not only help to protect your own privacy but also make a valuable contribution to conserving it for everyone.
