Tor and VPNs are both proxy-based technologies that are designed to increase user privacy when using the internet. They are, however, very different beasts that rarely crossover on a real-life practical level. Fortunately, ProPrivacy is here to walk you through the differences and help you to understand which of the two technologies is right for protecting your privacy.
Tor or VPN - What should you use?
There's a particularly easy way to decide whether Tor is right for you, or whether you should use a VPN instead:

Going into more detail, Tor provides true anonymity and it's completely free, but it isn't without its caveats. Tor is the slower of the two options, so much so that it is a poor choice for day-to-day internet use and makes ordinary activities such as watching YouTube videos all but impossible. It is also not suitable for protecting yourself when torrenting, which we will discuss later in the article.
Conversely, VPNs do not provide true anonymity and are unlikely to protect you if you are doing something highly illegal or if your name is Edward Snowden. They do, however, provide real privacy benefits when surfing the internet with minimal cost to the experience, and can even unblock streaming catalogs from Netflix or BBC iPlayer outside of their target countries - for a price.
What is Tor?
The name Tor originated as an acronym for The Onion Router and refers to the way in which data encryption is layered. Tor passes data between a number of randomly selected Tor nodes run by volunteers, encrypting it each time.
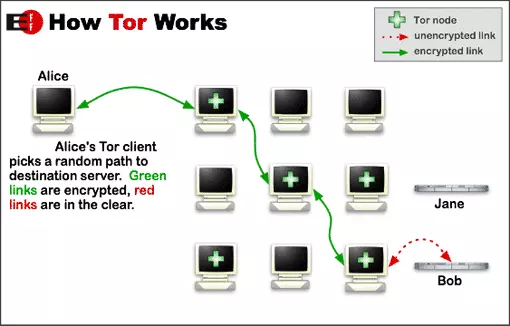
Each node knows where the connection comes from and the node it is going to, but cannot see the whole route (circuit). This is the beauty of Tor, in that no trust is required as no-one should be able to connect a user with their activity on the internet.
The entry node can see who you are, but not what you do on the internet, while the exit node can see what you do, but does not know who you are. As a result, Tor affords users a level of true anonymity when using the internet.
Each node is run by a volunteer. It goes without saying, then, that the more volunteers there are, the safer Tor is for all its users. For a more detailed look at Tor, including at its potential vulnerabilities, please see our full Tor Review.
Tor pros
- Offers true anonymity
- Very secure
- A powerful anti-censorship tool
- Distributed network – almost impossible to shut down or attack meaningfully
- Free
Tor is required in order to access the dark web (Tor Hidden Services). But since this comparison article only really compares Tor with VPNs for accessing the open internet, we won’t list this important feature as a "pro” here.
Tor cons
- Very slow – your data is randomly bounced through a number of nodes, each of which could be anywhere in the world and, therefore, painfully slow your experience. If your internet connection is fast enough, then Tor may suffice for casual web browsing, but severe buffering issues always make streaming video content wildly impractical
- Not suitable for P2P filesharing – there is no way to stop you from using BitTorrent over Tor (and people do it), but its diabolically poor speed can have a domino-effect by slowing the entire torrenting network for every other user. Worse yet, if copyrighted material is involved, Tor node volunteers can get in trouble for the actions of others - which could be critical and possibly life-threatening for some
- It's easily blocked - the list of Tor exit nodes is published openly, meaning providers can easily restrict access. This problem can be mitigated, though, through the use of Tor bridges.
- Captchas - CloudFlare takes an aggressive stance towards Tor users. And because CloudFlare hosts a very large percentage of the world’s websites, Tor users are likely to find themselves repeatedly challenged by CAPTCHAs and other similar security measures.
Want to access the dark web?
If you want to access the dark web, then you will need Tor or another an encrypted browser such as I2P. However, using a VPN with Tor can help you maintain anonymity. Although an encrypted browser hides what you get up to online, your ISP will know that you have downloaded Tor. Check out our best VPN for Tor article for a list of services that will help protect your identity and to find out more about accessing the dark web securely.
What is a VPN?
A Virtual Private Network (VPN) connects your device to a VPN server, usually operated by a commercial VPN provider. This VPN server acts as an intermediary between your device and the internet.
-
Websites and anyone else on the internet can’t see who you are (i.e. you’re real IP internet address). All they see is the IP address of the VPN server.
-
Your internet provider (ISP) can’t see what you get up to on the internet. It can see that you have connected to the VPN server’s IP address, but nothing else.
-
Your ISP also can’t see the content of your internet data because the connection between your device and the VPN server is securely encrypted.
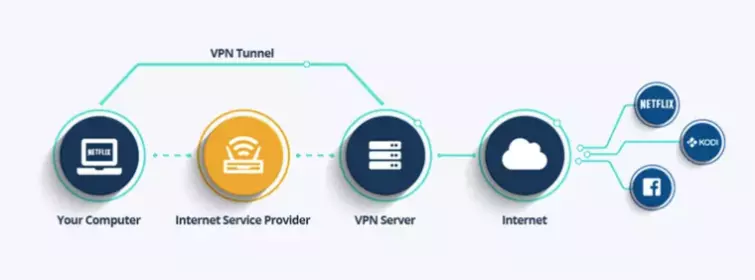
Naturally, what your ISP can’t see, your government won’t see unless it has singled you out for targeted surveillance. For a detailed look at what VPNs are and what they do (and can’t do), please see what is a VPN and how does it work?
VPN pros
-
Faster - using a VPN does have some impact on your internet browsing speeds, but compared to Tor this impact is negligible (and is minimized by connecting to a VPN server near your real geographic location)
-
No prying eyes - it protects you from blanket government surveillance, surveillance by your ISP, and the most basic form of web tracking (IP logging)
-
Unblocks and supports streaming libraries - VPN providers operate VPN servers in countries all around the world, making VPNs great for unblocking streaming services such as BBC iPlayer or Netflix’s regional catalogs which geographic restrictions placed on them
-
Circumvents censorship - like Tor, this also makes VPNs great for defeating many forms of censorship. If your government censors content, then simply connect to a VPN server located somewhere that does not censor it
-
Some support torrenting - many VPN services cater specifically to P2P torrent users.
VPN cons
-
VPNs do not provide true anonymity - depending on your threat model they can provide a high level of privacy when surfing the internet, but the VPN provider always knows your real IP address and can tie this to your internet history.
Using a good no logs VPN mitigates against this problem but this only protects historical activity and still requires you to trust that the VPN is doing what it says it is doing implicitly. A VPN provider can always start logging when pressured to do so, and no VPN staff will ever be willing to go to prison in order to protect you. -
They do cost - Most reliable VPN services are priced at a few dollars per month (although exceptions to this rule do now exist).
Final thoughts
If you are a whistleblower, political dissident, or might otherwise get into serious trouble for your activities on the internet, then use Tor. Nothing is guaranteed in this world, but Tor provides the highest level of anonymity possible on the internet.
Everyone else, however, should use a VPN. A good no logs VPN protects you from blanket surveillance by your government and ISP, prevents websites and suchlike from seeing your real IP address, and is effective at combating many forms of internet censorship.
VPNs are also great for fun stuff like watching the full US Netflix catalog and torrenting. And unlike Tor, they do these things with a negligible impact on your day-to-day internet experience.
