You’ll often hear of "five eyes countries” (and "nine eyes” and "14 eyes” countries) in the context of online privacy.
This guide lays out what these terms mean. Furthermore, which countries are part of them, and everything else you need to know.
So, let’s begin with the basics:
Who are the Five Eyes countries?

The Five Eyes countries are:
- United States
- United Kingdom
- Australia
- New Zealand
- Canada
Five Eyes (sometimes referred to as FVEY) is an intelligence alliance that dates back to the early 1940s.
Who are the Nine Eyes countries?
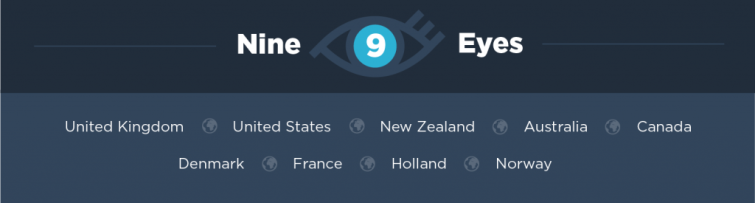
The Nine Eyes countries are:
- The 5 Eyes Countries
- Denmark
- France
- Netherlands
- Norway
As you might suspect, Nine Eyes is an extension of the core Five Eyes alliance.
Who are the 14 Eyes countries?
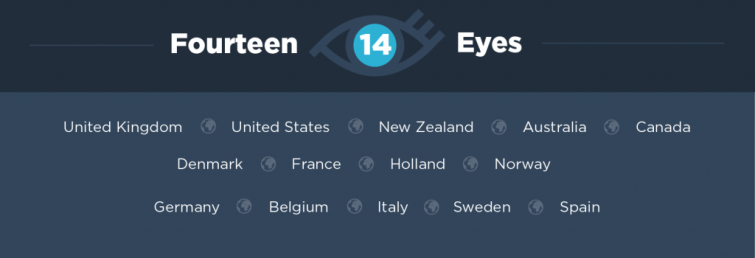
The 14 Eyes countries are:
- The 9 Eyes Countries
- Germany
- Italy
- Belgium
- Sweden
- Spain
This alliance is also known as SIGINT Seniors Europe (SSEUR). According to Wikipedia, it’s there to coordinate "the exchange of military signals intelligence among its members”.
History of the Five Eyes Alliance
Five Eyes originally came about as a way for the core countries to share intelligence. It was founded as the informal UKUSA agreement in 1941. Official formalization between the UK and USA was in 1946, in the wake of the second world war. However, since then it also encompasses other core countries.
Beyond the core Five Eyes countries come the other nations that form the Nine and 14 Eyes groups. These nations joined the scheme as "3rd party countries”. Furthermore, it’s widely believed that other countries in the schemes beyond the core countries listed. The suspected countries include "Pacific allies” such as South Korea and Singapore.
Five Eyes and similar arrangements are (by their nature) always secret. Wikipedia suggests that it was nearly 30 years after the original formation of the agreement before the Australian Prime Minister even became aware of it. Furthermore, Five Eyes only came to public attention in 2005. Since 2010 it’s been possible to read some of the details of it online on the Research Gate website.
Recent Years Controversy
The Five Eyes agreement gained modern mainstream relevance when links to the NSA were proven. These were made public as part of the infamous Edward Snowden leaks. His revelations showed and confirmed that agreements made during the Cold War are being extensively used in the pursuit of widespread digital surveillance.
It became clear that these countries are using intelligence sharing agreements for purposes that go beyond signals intelligence. Therefore, they effectively allow the intelligence services in multiple countries to liaise with each other. Thereby sharing information relating to anything from human and defense intelligence to matters of national security.
An example of how this can work in practice came out with Snowden’s revelations in 2013. It emerged that the American NSA effectively outsources work to the UK’s GCHQ.
Most controversially for advocates of privacy, the Snowden revelations showed that governments make use of the Five Eyes framework to get around laws about monitoring their own citizens. As an example, the UK’s MI5 can ask the US NSA to tap UK phones, thus "allegedly circumventing laws.”
Here’s how De Spiegel described it at the time:
"Britain's GCHQ intelligence agency can spy on anyone but British nationals, the NSA can conduct surveillance on anyone but Americans, and Germany's BND foreign intelligence agency can spy on anyone but Germans. That's how a matrix is created of boundless surveillance.”
What do the 5 / 9 / 14 Eyes alliances do?
If you’re a privacy conscious individual, this is a very valid question. Furthermore, it’s more than reasonable to argue that what the agencies within these alliances do goes far beyond what they need to do to ensure they keep the world "safe.”
One of Edward Snowden’s most headline-grabbing revelations related to the NSA’s PRISM program, a mass data collection initiative whose participants include all the big players in the Internet world, including Microsoft, Google, and Facebook. PRISM has made it incredibly easy for the NSA (even its "low-level agents”) to access information on commonly-used platforms. Therefore, due to the alliances, other countries easily tapped into this ability as well. Unfortunately, even those who believe they have "nothing to hide and nothing to fear” would be spooked by the ease with which the NSA – and therefore their alliance partners – can tap into anything from Skype conversations to email messages.
Then we can add to that the fact that these security agencies have been shown to engage in practices that are at best – underhand. These include cracking encryption algorithms and bribing companies to weaken their own IT security systems
We’re not suggesting that the 5 / 9 / 14 Eyes alliances’ sole purposes are to snoop on citizen’s day-to-day lives. Unfortunately, the by-product of much of the related agencies’ work allows them to do just that.
The Alliances and VPN Use
For many, the whole point of using a VPN (Virtual Private Network) service is to avoid government surveillance. Thereby being able to browse the Internet with a reasonable level of privacy.
As you can see from the information above, you can easily defeat that object by choosing a VPN provider based in one of the countries. Particularly the Five Eyes countries, or one that locates its servers in one of those countries. Thereby, authorities could compel a provider to hand over details of your online activities. Furthermore, thanks to the information sharing, it could be ANY of the countries on the list!
Using a VPN server in a 5 Eyes Country
A commonly asked question is what the position is if someone uses a VPN provider in a country outside of the 5 / 9 / 14 Eyes jurisdiction. Then uses it to connect to a server in a country that IS within that jurisdiction, such as in the US or UK.
Without going into too much technical detail, there is some risk here. The FVEY country could subpoena the server provider for connection logs (or even perform its own monitoring of connections into and out of the server). However, if the VPN provider is taking the right security precautions on their infrastructure, the risk should be relatively small.
That said, people keen to minimize their exposure to the broad jurisdiction of these intelligence alliances should take the lowest-risk approach. That would be using a provider outside the 5 / 9 / 14 Eyes jurisdiction AND only connecting to servers outside of the jurisdiction.
So which VPN should I choose?
A good starting point is to look at our Best VPN no logs guide.
These VPN services don’t keep any record of your browsing activity. Therefore, if they were ever required to hand over details of usage, they wouldn’t have any of that information to share.
Therefore, choose a VPN that’s outside the far-reaching jurisdiction of 5 / 9 / 14 eyes, AND one that doesn’t keep activity logs. Thereby you are doing all you can to minimize the chance of your online activity being subject to a questionable level of surveillance. This is why we do not recommend using a free VPN as they can be dangerous and they often sell your data.
Conclusion
In conclusion, you should avoid Five Eyes countries as much as possible. Furthermore, even the nine and fourteen eyes alliances should be avoided where possible.
Lastly, using a VPN is a great way to help protect your online privacy. However, there is a lot to more to be careful of. Check out our useful guides and news to get more information on internet privacy and security.
