Hacking and the mysterious figures who do it have been demonized and mythologized in almost equal measure.
The term hacking can refer to harmlessly modifying or altering equipment or processes to do things they were originally designed for, or it can refer to unauthorized intrusion into a computer or a network - which is what this article discusses. Many hackers do what they do for criminal motives, while others hone and deploy their hacking skills for benign, and sometimes even noble, purposes. It’s these people this article is intended to help.
What is ethical hacking?
For some, ethical hacking is simply a stepping stone to a well-paid respectable career. The skill-set looked for by those recruiting system security professionals and penetration testers is identical is to the skill-set tet already possessed by talented hackers.
The result is that companies recruit heavily from the hacker community, and any kid with an internet connection can learn to hack in their bedroom.
For others, ethical hacking is a form of political activism or hacktivism. As always, though, one man’s freedom fighter is another man’s terrorist.
Some people just love the challenge of hacking but want to use their skills for good.
Whatever your reasons for wanting to get into ethical hacking, this article aims to provide some practical advice on how to get started. Ethical hacking is often referred to as penetration testing (pentesting), although correctly, the two terms have slightly different meanings.
Ethical hacking involves the use of any and all tools at a hacker’s disposable, while pentesting is a more specific term that focuses on discovering vulnerabilities in a target environment without actually exploiting them or the target systems.
Core hacking techniques
Although not exhaustive, the following list highlights some of the main techniques employed by hackers (ethical or otherwise).
- Password cracking: whether using brute force (guessing the password until you get it right), social engineering, cyberstalking (following a target’s social media accounts in order to obtain clues about the passwords they might use), or other means.
- Packet sniffing: intercepting WiFi or Ethernet data packets so you can analyze transmitted data (which may include, among other things, passwords).
- Vulnerability scanning: assessing computers or networks for weaknesses. The simplest (and most common) form of vulnerability scanning is port scanning for open ports.
- Viruses: one of the most effective ways to compromise a target system is to introduce a virus (known to hackers as a "payload”) into it. This can be done physically (using a USB stick, for example), via a payload hidden in an innocent-looking email or document, and in many more ways.
- Rootkits: software which gives the user illicit administrator (root) access to a computer. Rootkits usually work clandestinely so that authorized users are not aware of their existence.
- Trojans: A program that appears to be a different (benign) program, but which allows backdoor access to a system.. Trojans are often attached to working legitimate programs in order to avoid alerting the victim about their presence.
- Social engineering: manipulating people to divulge confidential information (such as passwords) or to gain access to gain physical access to target computers or systems.
- Keylogging: recoding the keys pressed by users of a target computer. Which can, of course, include passwords. In the past, keylogging was usually performed by somehow introducing keylogger software to the target system, but the popularity of insecure wireless keyboards makes wireless keyboard sniffing an increasingly effective tactic.
Bastille KeySniffer

Gear
It may be stating the obvious, but your ethical hacking career is not going to get very far without a computer and an internet connection. Other than that, there are a huge number of gadgets available to the serious hacker or cybersecurity security professional.
If you are just starting out, though, the following gear is pretty essential:
1. Kali Linux
You can use Windows or macOS for many hacking projects. Hell, you can probably manage some hacking on an Android phone (although less so on an iPhone). But serious hackers use Linux. And hackers’ Linux distro of choice these days is Kali.
The prominent use of Debian-based Kali on the Mr. Robot TV show is in part responsible for its popularity, but thanks to this popularity it has developed into a powerful hacking tool with over 600 penetration testing tools installed out-of-the-box.
If you only want to dip your toe into ethical hacking then custom VitualBox and VMware images are available for running Kali inside a Virtual Machine. Also rather cool is Kali Linux NetHunter, which replaces Android on Nexus and One Plus devices.
Although Kali has become a sort of default "hacker OS,” there are many other good alternatives out there, each with their own strengths and weaknesses. These include Blackbox, Parrot Security OS, Live Hacking OS, DEFT Linux and more.
One issue with all Linux hacking distros, though, is one that plagues Linux users everywhere: lack of driver support for hardware. The situation is improving, but it does mean that users of Kali and the like must choose their hardware carefully.
2. A VPN or Tor connection
If you're going to be naughty on the internet (Please: remember that this is an article on ethical hacking), then it is important to hide your identity from your targets.
A good no-logs VPN will provide more than sufficient privacy for most ethical operations without having a noticeable impact on your internet experience. If you are doing something very criminal, or which will get powerful people or organizations really pissed at you, then Tor is your best bet for achieving true anonymity.
3. A WiFi adapter that supports monitor mode and wireless injection
Not strictly necessary, but other than your computer itself, a WiFi adapter that supports monitor mode and wireless injection should be next on your hardware shopping list.
With the right software tools (such as Aircrack-NG), these handy devices can crack WEP and WPA2 connections in order to intercept and modify data sent over WiFi networks.
There are plenty of these available if you search online for "Kali WiFi adapter,” although models from Alpha, such as the reliable old workhorse Alfa AWHUS036NH or the newer AC-capable Alfa AWUS036ACH always make solid recommendations.
Alternatively, more advanced WiFi pentesting tools such as the WiFi Pineapple are very powerful in the right hands.
4. The most powerful graphics card you can afford
GPUs are great at crunching numbers, which is why they are so important when building cryptocurrency mining rigs. This also makes them great at brute-forcing passwords using tools such as Hashcat.

At the time of writing, the NVidia GTX 1070 range of graphics cards provide a lot of bang for buck to budding ethical hackers, while those with money to burn can build an awesome password cracking rig using a bank of Nvidia RTX 2080 Ti cards!
5. Worker overalls, a fake mustache, lockpick set, and a badge-making machine
In many people’s imagination, hacking is a purely cerebral high-tech activity. Many of the most effective hacking techniques, though, require a much more boot-on-ground approach.
Searching through a target’s trash cans is a tried and tested way to discover valuable passwords or at least clues to what those passwords might be. Similarly, gaining illicit access to an office environment is a great way to scope out passwords and other valuable information written on whiteboards or Post-it notes carelessly stuck to staff computer screens.

Indeed, even when deploying more high-tech infiltration tactics, such as installing keylogger software on a target’s PC, introducing LAN Turtle or Packet Squirrel to a target organization’s local network, or plugging any number of powerful USB tools (for example a USB Rubber Ducky or Bash Bunny) into a target computer, you will somehow need to achieve need physical access to the target computer or network.
And often the only way to get this kind of unauthorized access is to use old-fashioned physical sneakiness. As an ethical hacker, though, please remember to stay on the right side of the law (or at least have a strong and ethical reason for crossing the line).
6. Virtual server space
Renting a virtual private server (VPS) costs pennies these days, but VPSs are an essential tool in any ethical hacker’s armory. You can use a VPS to host phishing or Tor hidden services (.onion) website. A VPS can also host Nmap scripts and payloads, act as a private VPN server, or as a deniable platform for Metaspoilt pentesting sessions.

Ideally, you should use a VPS hosting service that allows you to sign to up without providing personal details and that allows you to pay anonymously (e.g. using properly mixed Bitcoins). These are usually more expensive than regular VPS services, but even ethical hackers require as much deniability as possible.
Software tools
As we have already noted, Kali Linux comes with over 600 hacking and pentesting tools pre-installed. They (and others) all have their uses, but some of the most important ones you should familiarize yourself with include:
Metasploit
A collection of utilities that provide a framework for developing your own exploit code and executing it against remote target systems. A powerful hacking tool, Metasploit is also an invaluable tool for corporate pentesters, as it allows you to simulate real-world attacks in order to identify vulnerabilities in a system.
Burp Suite
A GUI tool for testing Web application security. Clearly, of great use to corporate pentesters, Burp Suite also allows hackers to automate custom payloads and modify specific requests. It can also act as an interception proxy to give the user control over requests sent to the server.
Hashcat/oclHashcat
A password cracking tool for brute-forcing passwords. Hashcat uses your CPU to perform the grunt work, while oclHashcat offloads processing to your graphics card. In addition to straight brute-forcing, it can perform dictionary attacks, hybrid attacks, rule-based attacks, and more.
As with all brute force methods of password cracking, its viability very much depends on the strength of the password chosen by the user.
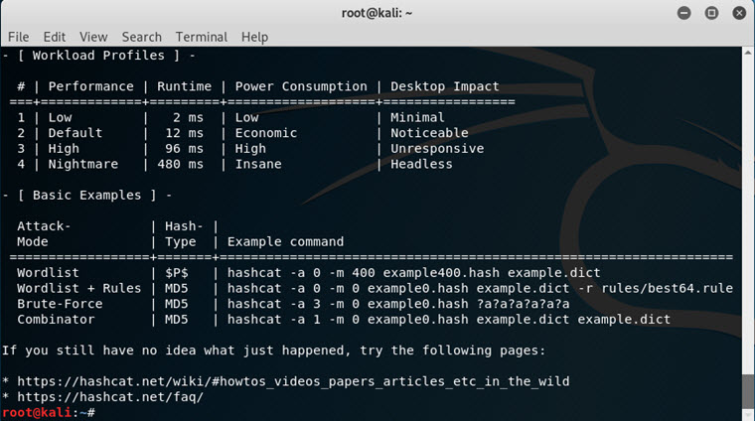
John the Ripper is a popular CPU-based alternative to Hashcat, while and Cain and the very flexible Able is often preferred by Windows users.
Nmap
A network and port scanning tool widely used for network reconnaissance and security auditing. It features a suite of tools useful for probing networks for vulnerabilities but really comes into its own through the use of scripts which provide advanced functionality such as service detection, vulnerability detection, and more.
Wireshark is the network packet analyzer of choice for network engineers everywhere. Although only a passive tool, and therefore not directly useful for active hacking, many hackers swear by it for performing WiFi reconnaissance.
Aircrack-ng
This tool provides a much more proactive approach to hacking WiFi networks. It is a packet sniffer capable of intercepting and cracking WEP and WPA/WPA2 traffic. To get the most out of it you will need a WiFi adapter that supports monitor mode and wireless injection.
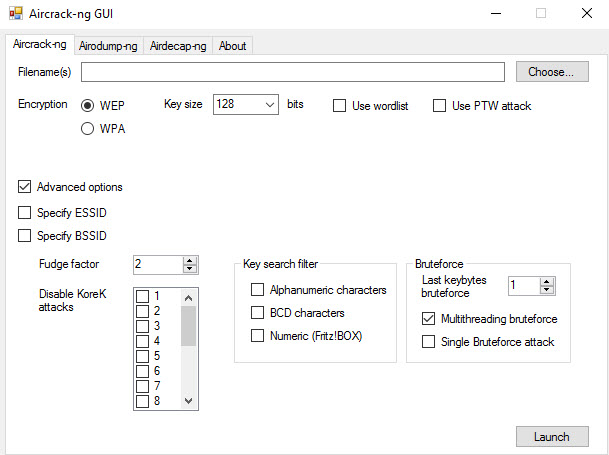
Aircrack-ng is also effective as a generic password cracker. The Linux app (including for Kali, of course) is command-line only, but a GUI version (shown above) is available for Windows.
Social-Engineer Toolkit (SET)
This unusual program is an invaluable tool for pentesters because it addresses the human side of many hacking techniques. The Social-Engineer Toolkit can simulate a variety of social engineering attacks, including spear phishing attacks, credential harvesting, and more.
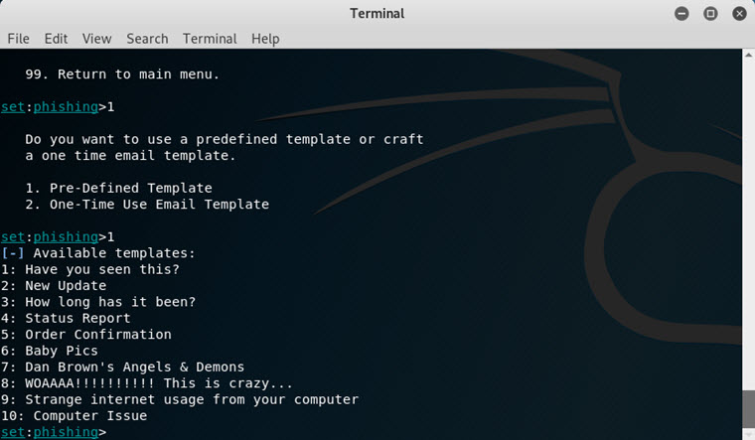
In Mr. Robot Elliot uses SET to perform an SMS spoofing attack.
These excellent hacking and pentesting software tools are, of course, just the tip of a very large iceberg. When you are ready to explore further, a very comprehensive list of hacking tools is available here.
Ethical hacking tips
Knowledge is power. And this is never truer than in the field of ethical hacking.
1. Learn how to script (or even better, code)
You don’t need to be a fully-qualified software developer proficient in C++ to hack effectively (although it doesn’t hurt!), but you should at least understand the basics of coding and know how to knock up a bash script.
Knowledge of more advanced scripting languages such as Perl, JavaScript, Java, and Python is a definite plus.
2. Learn about TCP/IP networking
TCP/IP is the group of protocols that underpin both the Internet and local intranets. To be an effective hacker you need a detailed understanding of how networking works in order to identify and exploit weaknesses.
3. Learn how to use Linux
As already mentioned, Linux is the hackers’ primary tool of choice. It is also the most popular server OS on the planet. So it is vital that you have a very firm grasp on how Linux works, one that goes way beyond being able to fire up Firefox in Ubuntu’s GUI interface!
You should understand its underlying architecture and be able to perform all routine tasks in Terminal without GUI assistance.
4. Know your tools
As we can see from the software tool list above, hackers have some very powerful tools at their disposal. But they are only powerful in the hands of those who know how to use them. So take the time needed to know your tools inside out.
5. Think outside the box
Security professionals go to great lengths to prevent hackers from compromising their systems, and they are generally pretty good at their jobs. So successful hacking often involves thinking of something that has simply not occurred to anyone else before.

6. Do your research
You should learn everything you can about your target system. A strong understanding of the target OS is a good place to start, followed by detailed network reconnaissance to fully map out your target system in order to identify weaknesses.
7. Polish your communications skills
The stereotypical script kiddie who operates out of his or her bedroom may not need much in the way communication skills. But as an ethical hacker or corporate penetration tester you need to communicate your findings clearly to network managers and non-tech-savvy company bosses.
Keeping notes of everything you find, including screenshots, log files, and personal notes can all help here.
8. Get involved with hacking communities
Joining communities of like-minded people is always the best way to immerse yourself in any subject, but (ethical) hacker communities are particularly useful since they can offer advice and support, answer questions, or even help brainstorm specific challenges you might face.
They are also a great way to find out about jobs and other ethical opportunities to monetize your hard-earned hacker skills. Some hacker communities are very secretive and hard to become a member of, but as an ethical hacker you probably want to avoid these.
The excellent Hackaday forums are defunct, but Evilzone, r/netsec , and Hack this Site host vibrant and helpful ethical hacker forums.
Become a qualified Hacker
It may seem counter-intuitive to the point of being surreal for many people, but it is now possible to get formal qualifications in hacking that are recognized by corporate penetration testing and IT security recruiters the world over.
The Certified Ethical Hacker (CEH) is the most recognized, but also broadest, such qualification. It is offered by the EC-Council, who also provides more advanced accreditation in the form of the Certified Network Defense Architect (CNDA).
This was designed for US government agencies, is ANSI accredited, and is part of GCHQ Certified Training (GCT).
Image credits: socrates471/Shutterstock, Africa Studio/Shutterstock, dotshock /Shutterstock, xactive/Shutterstock.
