Want to protect your personal data from prying eyes? The best way is by encrypting it, and many of us previously relied on TrueCrypt to do so. However, as the popular encryption app has been mysteriously discontinued, we've put together this article to find five of the best TrueCrypt alternatives.
Anyone serious about their digital security should look into encrypting their own data, rather than relying on a third-party to do it for them. This is what's known as end-to-end-encryption (E2EE).
But even if you're using E2EE, how do you know that your encryption software isn't up to something untoward – like secretly sending your encryption keys to its developers, or creating a backdoor in its encryption?
Open-source code is the only guarantee we have against this kind of nefarious behavior. Only if a program can be freely examined to ensure it does what it is supposed to (and only what it is supposed to) can we place a reasonable amount of confidence in it.
Of course, we can place even more confidence in a program that's been audited by a reputable third-party. This isn't a foolproof tactic, however, as code can always be changed the moment the auditors leave the building. So, simply being able to audit the code is the surest guarantee possible that any encryption program is secure.
TrueCrypt alternatives
We've listed the best TrueCrypt alternatives below. Most of these options use the industry-standard AES cipher – and if you're interested in learning more about how AES encryption works, we've got a guide for that!
VeraCrypt
Platforms: Windows. MacOS, Android, and Linux. Third-party Android and iOS apps allow you to open and access data stored VeraCrypt containers.

VeraCrypt is a fork of TrueCrypt and its direct successor – so don't be put off by the minor branding changes. Its front-end looks the same and functions identically to TrueCrypt. Its code has been fully audited, and the uncovered problems fixed.
As such, VeraCrypt is widely regarded in the security world as the go-to open-source full-disk encryption program. It allows you to create a virtual encrypted disk (volume) which you can mount and use just like a real disk. Or it can even be used to encrypt an entire disk partition or storage device (e.g. a hard drive or USB stick), including the drive your Operating System boots from.
By default, VeraCrypt encrypts all data stored in a volume with an AES-256 cipher, although when creating a volume you can specify an alternative cipher. The NIST averse, for example, can opt to use a Twofish, Serpent, or Camellia cipher. Data is then authenticated using SHA-512 by default, but again, users can select an entirely different hashing algorithm depending on their preference.
A notable feature of VeraCrypt is that any file, for example, an innocent-looking photo file, can be used as the container for a VeraCrypt volume. Even more notable is its hidden volume feature, which provides plausible deniability. It does this by hiding an encrypted volume inside another VeraCrypt volume in such a way that, if the correct precautions are taken, it is impossible to prove the second hidden volume exists.
Data stored in VeraCrypt containers can be securely synced across devices by storing a volume in (and mounting it from) a cloud storage sync folder. VeraCrypt can be used in this way to store data securely on otherwise insecure platforms such as Dropbox.
It is not an ideal tool for this job, however. Volume sizes can be large and are of a fixed size, which you must specify when creating them. And when any data inside a volume is changed, the entire volume must be re-uploaded.
Of all the software discussed in this article, VeraCrypt is by far the most thoroughly audited open-source encryption solution available.
Please check out our guides on VeraCrypt & how-to basics and A Guide to VeraCrypt hidden volumes for deep dives into this important encryption program. Or, check out our how to create a virtual machine inside VeraCrypt.
AESCrypt
Platforms: Windows, macOS, Linux, Android (third party but open source).
A third-party AESCrypt for iOS app is also available, although it is closed source and free users are limited to simply viewing files pre-encrypted on the desktop using AES Crypt.
AES Crypt is a free open source (FOSS) cross-platform per-file encryption app which secures files using the AES-256 cipher. As a per-file encryption app, it allows you to manually encrypt individual files. Batch file encryption is not supported, although this limitation can be overcome somewhat by creating zip files out of folders, and then encrypting the zip file with AES Crypt.
This very easy-to-use Java-based file program integrates with the OS, providing simple file encryption using the right-click menu button in Windows, or drag and drop in macOS and Linux (or an extension allows right-clicking in macOS).
File decryption is performed by simply double-clicking the encrypted.aes file, and entering the password you supplied when creating it. It should also be noted that when you create an encrypted version of a file, the original unencrypted version remains untouched. This is great if you just want to store the encrypted version online, but for maximum security, you should delete the original. Just don't forget the password!
AxCrypt
Platforms (free): Windows. Free MacOS, Android, and iOS apps are available which allow you to open and view files, but not encrypt them.
Platforms (Premium): Windows, macOS, Android, and iOS.
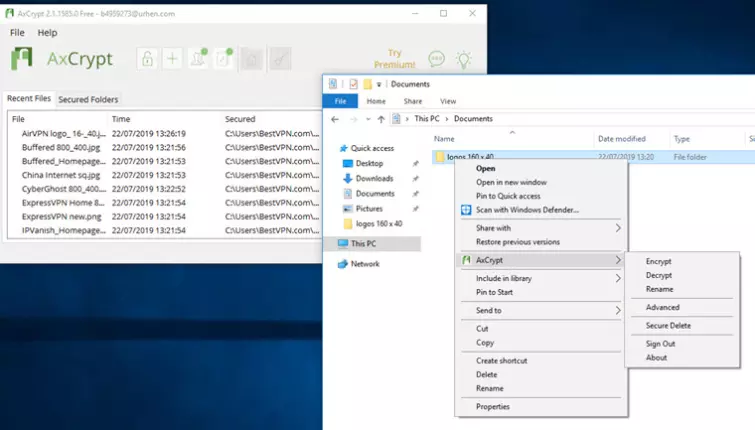
Like AES-Crypt, AxCrypt is an open-source cross-platform per-file encryption app which secures files using AES. It is, however, a quite different beast. It comes in a free version aimed mainly at Windows users and a premium version, which costs $35 USD per year (30-day free trial).
AxCrypt Free integrates with the Windows OS to provide seamless on-the-fly AES-128 file encryption. Rather than setting a password each time you encrypt a file, you sign into the app and then all selected files are automatically encrypted and decrypted using that password.
Folders themselves cannot be encrypted using AxCrypt Free, but all files in a folder can be batch-encrypted. Or you can select as many files as you want from anywhere on your PC and perform batch encryption on them.
For Windows users, then, AxCrypt Free offers many advantages over the rather basic AES Crypt. What you lose, however, is cross-platform compatibility. Free apps for macOS, Android, and iOS (but not Linux) allow you to open and view encrypted files, but not encrypt them.
A premium AxCrypt subscription solves this problem, with full support for all platforms. Users also get access to plenty of useful extra features, including full folder encryption (with sub-folder encryption), key sharing, account key backup, anonymous file names, and more.
GoCryptfs
Platforms: Linux (DEB package or compile from source), macOS (using Homebrew).
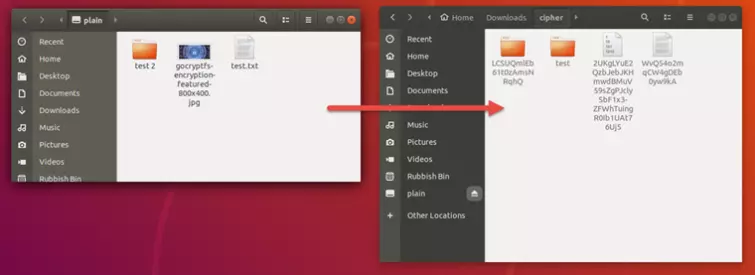
GoCryptfs is inspired by the brilliant but flawed EncFS. Like Encfs, it creates paired folders or "volumes". One volume contains the unencrypted files (let's call it the "private folder"), while the second matching volume (let's call it the "encrypted folder") holds an encrypted version of the files in the first (private) volume.
Unlike VeraCrypt, each file in a volume is encrypted and stored individually, so a change to one file does not mean re-uploading an entire encrypted container.
This makes GoCryptfs much better than VeraCrypt at storing files on cloud services such as Dropbox, as local files are kept unencrypted in the private volume, but are mirrored on Dropbox (etc.) in encrypted form by simply placing the matching "encrypted volume" in a cloud folder.
What GoCryptfs does not do is simply encrypt a file. Someone with access to the "personal folder" has access to the unencrypted files. In addition to this, files names in the encrypted folder are obscured, but metadata such as directory structure and file size are not.
Whilst GoCryptfs is command line only, setup is incredibly straightforward, meaning that even first-time users will have no problem encrypting files. Once you have your app up and running, you can drag-and-drop files to and from the private folder using your regular GUI file manager. Alternatively, SiriKali is a GUI frontend compatible with GoCryptfs.
SecureFS and Crysfs are similar EncFS-inspired apps. SecureFS fixes the issues with EncFS and is notable for being available for all major platforms, including Windows (requires MS Visual C++ 2015 redistribution package). Crysfs' support for Windows is still very experimental, but it fully supports Linux and macOS, and improves on gocrypt and SecureFS by encrypting file metadata and directory structure.
Cryptomator
Platforms: Windows, macOS, Linux, Android, iOS.
Cryptomator provides transparent encryption of files stored in the cloud. The encrypted vault is stored in your cloud folder, but is decrypted and mounted locally as a virtual drive for seamless drag-and-drop functionality.
Files are encrypted individually, so when changes are made, only the corresponding encrypted file is changed. In addition to the content of files, the directory structure is hidden, although file modification dates cannot be hidden without breaking your cloud provider's synchronization feature.
Vaults are secured using AES-256-CTR and unlocked using a passphrase which is protected against brute force attacks using the scrypt key derivation function.
Cryptomator's desktop client is available for a "pay what you want" model – which is particularly attractive to folks on a budget. You can even get your hands on Cryptomator for free, but users are encouraged to donate funds towards its development. Currently, the mobile apps (which support fingerprint unlock) are available for $11.99.
Final Thoughts
VeraCrypt is a drop-in replacement for the now discontinued TrueCrypt. If you have differing encryption needs – don't panic! The open source tools discussed in this article reflect a variety of use-cases.
You may need to choose between AES Crypt and AxCrypt, and between GoCryptfs (or other Encfs-inspired variant) and Cryptomater, but most apps lists here do their own specific thing with very little crossover in functionality between them.
The best advice, therefore, is to deploy a variety of encryption apps. This way, you'll get first-hand experience and find the right tools for the job, rather than waste time trying to knock square pegs into round holes with a single app that can't complete the task you'd like it to.
And, if you need one final reminder of our top picks for TrueCrypt alternatives, you'll find all the info you need in the table below:

From $0.00/month
The best advanced TrueCrypt alternative, and users will be able to batch encrypt files and entire folders. Free and premium versions of the service are available to download.
- ProPrivacy TrustScore:
- 9.8 out of 10



