Looking for a VPN that'll take your digital privacy as seriously as you do? After some tips on how to stay secure online when using a VPN? Either way, you're in the right place! We'll take a look at five of the most secure VPN services on the market in this guide – and explain how they can prevent third-party snooping.
Most modern websites implement robust encryption, but browsing the web without a VPN leaves you vulnerable to snooping at the hands of your ISP or other third parties, as well as exposing information about your location to website operators and other users on P2P networks. That's where a VPN comes in handy.
A VPN creates an encrypted tunnel between your computer and the VPN operator's servers, this protects all the traffic that travels between these two points. Any network interactions between your computer and the internet will, as a result, look like they're originating from the VPN's IP, hiding your whereabouts and allowing you to access geo-restricted content.
Picking a VPN can be confusing and it's important to choose a provider that's secure, trustworthy, and packed with features. Even a small mistake in setting up the cryptography could lead to your IP being exposed, which is why we carefully compare each service.
What are the most secure VPNs in 2024?
Below, you'll find our list of the most secure VPNs. The ProPrivacy team has been putting VPNs to the test since 2013, and all of our recommendations are grounded in first-hand experience and industry familiarity. All the services mentioned in this article have battle-tested encryption, advanced security features, and apps for all platforms, so you can enjoy round-the-clock protection. You can scroll down for a more in-depth look at our top picks.
- ExpressVPN - The best secure VPN. A superb service packing OpenVPN encryption and a robust suite of tools, plus a 30-day money-back guarantee.
- NordVPN - The best value secure VPN. With well-implemented encryption, plenty of worldwide servers, and an array of security features.
- Private Internet Access - The best privacy-oriented VPN. Not only is it packed with security features, but it has proven its no-logs policy in court!
- PrivateVPN - The cheapest secure VPN on our list. An incredibly affordable no-logs service with strong encryption and reliable speeds.
- Surfshark - The best multi-device secure VPN. Featuring unlimited simultaneous connections and OpenVPN encryption, for a budget price.
See the full list & in-depth analysis
All VPNs should provide users with a secure connection. That much is fundamental, but some services do a much better job than others. Because the VPN market is so overcrowded, it can be difficult to find a secure VPN with all the features you need to adequately safeguard your digital privacy.
The true mark of a secure VPN lies in its technical security. To accomplish this, a VPN service must offer the following features:
We recommend that you keep an eye out for these key features when picking out a security-oriented VPN service – and we've made sure that our top ten picks tick all these boxes.
In addition, where possible we try to recommend VPNs that have completed a full third-party audit of their service, and that run on diskless servers for added protection.
10 most secure VPN services in 2024 | In-depth analysis
Let's take a closer look at our shortlist of the most secure VPN services available today.
ExpressVPN is the best secure VPN. It's chock-full of impressive security features, offers solid encryption, and doesn't compromise on speeds. ExpressVPN Demo I'm consistently impressed by ExpressVPN's ability to balance superb security with a customer-focused experience. The provider ticks all the right boxes, offering a variety of encryption protocols, 24/7 live chat support, and easy-to-use apps for all of your devices. Right off the bat, ExpressVPN scores top marks for its no-logs policy. The provider just isn't interested in monitoring your online activity or keeping logs about what you get up to – and have even invited one of the industry's top auditing firms, PwC, to confirm these claims. ExpressVPN also runs its very own DNS and supports P2P activity, so you'll be able to torrent securely and enjoy unprecedented digital privacy. Plus, it's good to know that ExpressVPN is headquartered in the British Virgin Islands far from the reach of the 14 Eyes Alliance. ExpressVPN packs truly outstanding technical security that stands above the other secure VPNs in our list. It implements AES-256 cipher for OpenVPN, with an RSA-4096 handshake and SHA-512 keyed-hash message authentication code (HMAC). Perfect forward secrecy is provided courtesy of Elliptic Curve Diffie–Hellman (ECDH) key exchanges for data channel encryption. Users get to take their pick of a number of VPN protocols, too. I'd suggest sticking to OpenVPN if security is your main concern (seeing as it's been widely audited and is open-source). However, if you're looking for something a bit speedier, it's well worth trying ExpressVPN's very own proprietary protocol, Lightway. As the name suggests, Lightway is a lightweight option well suited to streaming and online play. Additional features Express is jam-packed with security features, including: With all of these features, it becomes clear that ExpressVPN offers exceptional VPN security. You can put this to the test yourself with a 30-day money-back guarantee protecting you if you change your mind. NordVPN is the best value secure VPN. A subscription won't break the bank, and bags users strong encryption, obfuscation measures, and sleek apps. Nord Demo NordVPN is a secure service with a robust zero-logs policy, making it perfect for people who demand high levels of privacy from their VPN provider. When it comes to encryption, NordVPN implements OpenVPN as default on Android and Windows. In addition, outdated protocols such as PPTP are completely unavailable (which is a blessing). OpenVPN is implemented well above our minimum standards for security (AES-256-CBC cipher with an RSA-2048 handshake and HMAC SHA256 data authentication), and Perfect Forward Secrecy (PFS) is provided by a DHE-4096 key exchange. On the iOS app, Nord is also secure. However, it does not implement OpenVPN, instead offering IKEv2, implemented with robust AES-256-GCM cipher and HMAC SHA2-384 data authentication. PFS is provided by a DHE-3072 exchange. Privacy-conscious users will be glad to hear that NordVPN makes its home in Panama. Doing so keeps the VPN out of snooping jurisdictions like the UK and US. In addition, NordVPN is an audited zero-logs provider – meaning you won't have to worry about your connection timestamps, browsing history, or other identifiable logs being stored. NordVPN's suite of security features is impressive... and relatively unmatched! Subscribers get access to an automatic kill-switch that will prevent their original IP address from leaking in the event of a VPN dropout, as well as DNS leak protection. And, for folks looking for more staunch security, there are XOR obfuscated servers and a handy double hop encryption feature. I constantly find myself recommending NordVPN to VPN beginners thanks to its easy-to-use apps. These apps are compatible with just about every device, install in a few clicks, and aren't cluttered with countless buttons and menus. It's incredibly easy to pick a server from the location list (or the interactive map) and get connected. Plus, if you do need help getting things set up (or want some advice about which protocol to use), you can field your questions to the NordVPN customer service team, available 24/7 via live chat. Private Internet Access is the best privacy-oriented VPN. It has proven that it keeps no logs, implements encryption to an impressive level, and has global coverage. PIA Demo Private Internet Access (PIA) is based in the US, so is not a provider for the more NSA-phobic out there. However, it keeps no logs, which is a claim that it has actually proven in court! And as well as being customizable, its security protections are extremely good. At maximum settings, OpenVPN encryption uses an AES-256 cipher with HMAC SHA256 for authorization and an RSA 4096 handshake for the data channel, and an AES-256 cipher with HMAC SHA384 authentication for the control channel. Perfect Forward Secrecy is delivered with a Diffie Hellman exchange (DHE) for RSA handshakes (or ECDHE+ECDSA for ECC handshakes). PIA's desktop software supports multiple security options, a VPN kill switch, DNS leak protection, and port forwarding. Up to 10 simultaneous connections are permitted. Its Android app is almost as good, and PIA boasts excellent connection speeds. You can test the service risk-free with a 30-day money-back guarantee. I loved that they offer strong OpenVPN encryption and WireGuard on their Mac apps. Some services only offer IKEv2 for Mac users, this is still a secure encryption protocol, but it's not as secure as OpenVPN. I also really like that this service offers a full Linux GUI client. PIA offers a wide range of features including an adblocker called MACE, which works but blocking the domains that serve adverts. I personally really liked the feature I thought it worked really well. They also offer port-forwarding, highly customizable apps with a dark mode, split tunneling, and more. PrivateVPN is the cheapest secure VPN on our list. This fast, no-logs VPN implements solid encryption standards, and it can unblock most streaming services as an added bonus. PrivateVPN Demo PrivateVPN is a provider based in Sweden that is true to its namesake. The VPN has excellent apps for all platforms that provide robust military-grade OpenVPN encryption that is implemented securely with a strong AES-256 cipher, a robust handshake, and watertight authentication on the control channel. This makes it completely reliable in terms of data privacy and security. During my tests I found the VPN to be not only highly secure but also great in terms of usability. It comes set up with strong encryption by default, which means it is perfect for beginners, and it has a kill-switch to ensure you never leak any data to your ISP by accident. PrivateVPN is a no-logs provider, which means that it will never hold any records about what you have done online while connected to its network. This means that it can never comply with data requests or warrants if the government approaches it. Due to its features, I found it to be great for torrenting and I particularly enjoyed the fact that it had obfuscation, which makes it suitable for anybody living in oppressive regimes that implement a lot of censorship. I tested PrivateVPN for streaming services such as Netflix and BBC iPlayer and found it to be super-effective. An excellent VPN that is well worth testing using its 30-day money-back guarantee. Surfshark is the best multi-device secure VPN. Impressively cheap despite offering unlimited simultaneous connections and an arsenal of privacy features. Surfshark Demo Surfshark is a low-cost provider that is known to be a superb all-rounder. The VPN has apps for all platforms that come with all the advanced privacy and security features you need. This includes a kill-switch, DNS leak protection, obfuscation, and OpenVPN encryption, and its OpenVPN is implemented with a strong AES-256 cipher and reliable Perfect Forward Secrecy. This ensures that your data is always protected against eavesdroppers and hackers. Plus, its no-logs policy ensures that Surfshark never has any data about what you do online. Due to its advanced privacy features, this VPN can be trusted by journalists, lawyers, and other citizens looking for the highest privacy levels. I really love how Surfshark's kill-switch, military-grade encryption, and outstanding privacy features kept me safe and secure online regardless of what device I am using and regardless of whether I'm at home or on the go. Especially when out and about and connected to public Wi-Fi, I know that Surfshark's got my back, helping users stay safely out of the reach of hackers and cybercriminals. Surfshark is suitable for doing sensitive tasks such as torrenting, however, it doesn't support port-forwarding. A VPN with servers in 100 countries
that can unblock virtually any geo-restricted international or censored websites and services. You can test it on unlimited devices simultaneously, and completely risk-free, thanks to its 30-day money-back guarantee. VyprVPN is the best feature-rich secure VPN. Vypr implements robust encryption across all of its apps so you are never left exposed, regardless of the device you're using. VYPR Demo VyprVPN is a provider based in Switzerland – a location that is generally accepted as being the best place in the EU for a privacy service to be based. VyprVPN is a no logs service that ensures nobody ever finds out what you do online. They went the extra mile and got a third party to independently audit their no logs claims and they proved they "do NOT log or retain any information from VyprVPN sessions". What makes you safe when using a VPN? Well, good security features certainly do – choosing a VPN has top-notch privacy tools to ensure that you are kept safe and private online. VyprVPN has these, it implements high standard encryption and provides advanced privacy and security features such as a kill-switch, DNS leak protection, and obfuscation, an ad and malware blocker, and much much more. The security features offered by this service ensure that the VPN is suitable for doing sensitive tasks such as torrenting or unblocking government censored content. With VyprVPN, OpenVPN encryption is implemented to a high standard using a strong cipher and Perfect forward Secrecy. This ensures that the VPN is future-proof and that your data cannot be intercepted even by government snoops. This service also instills an enhanced sense of safety for me because of its network ownership. VyprVPN owns and maintains all of their servers, so I know that the network’s hardware perimeter is secured and no third parties can access it, so that made me feel safer. I love that VyprVPN has servers in over 70 countries around the world. The fact that this VPN paid for a full third-party security audit means you can trust the service to protect your data. It's well worth testing using its 30-day money-back guarantee. CyberGhost is the best easy-to-use secure VPN. If you want peace-of-mind without having to tinker with settings, then CyberGhost is for you. CyberGhost Demo CyberGhost VPN manages to combine a wealth of features with an easy-to-use interface – meaning that it's a great pick for VPN newbies. The provider packs very strong encryption, and the 7 simultaneous connection allowance is quite generous. Being based in Romania and keeping no meaningful logs is also a big draw. Like ExpressVPN, some minimal statistics are kept, but with no timestamp or IPs recorded, these present no threat to users' privacy. The OpenVPN encryption used by CyberGhost is as strong as it gets. Data channel used an AES-256-CBC cipher with SHA256 hash authentication and control channel uses an AES-256 cipher, RSA-4096 key encryption, and SHA384 hash authentication. Perfect forward secrecy is provided by an ECDH-4096 key exchange. Whenever we have used our leak testing tool to check if CyberGhost is as watertight as the provider claims, we've found CyberGhost comes out unscathed. Encryption-wise, It's really hard to fault – they use the strongest protocols on the market and they're implemented to a very high standard – and they have a private DNS server too. Due to this, we feel really safe and relaxed when using CyberGhost. CyberGhost's top-notch logging policy, decent local (burst) speeds, and fully featured software gave it a spot on our list. We'd recommend trying it out for yourself, and you can do so with a generous 45-day no-quibble money-back guarantee on subscription plans longer than one month. AirVPN is the best advanced secure VPN. With well-implemented encryption, VPN over TOR, and zero-logs. AirVPN Demo AirVPN is at the top of the game when it comes to fast, secure VPN technology, but its tech-heavy focus and rather brusque support manner may alienate many would-be users or VPN greenhorns. AirVPN took me a while to get used to, seeing as it doesn't feel quite as slick as some of the bigger names in the industry, but its no-logs policy speaks for itself. The provider doesn't monitor your activities, but it does stay transparent about the aggregate data it collects in real-time – you can even view it yourself. Once I warmed to AirVPN, I actually really enjoyed the communal feel of the service, which very much prioritizes privacy. OpenVPN uses AES-256 with RSA-4096 handshake, HMAC SHA1 data channel authentication, HMAC SHA384 control authentication, and DHE-4096 for perfect forward secrecy. It allows users to connect completely anonymously to its servers via the Tor network and can hide OpenVPN communications inside a Secure Shell (SSH) and Secure Sockets Layer (SSL) tunnel. The open-source desktop client disables IPv6, and its "network lock" feature acts as a kill-switch and prevents DNS leaks. WebRTC leaks are blocked by both the network lock function and at the server level. This protects users from WebRTC leaks, even when using the generic OpenVPN app. Furthermore, AirVPN runs its own bare-metal servers. It also has secure VPN Apps called Eddie which works on Android and Linux. Give it a go with a three-day trial for just €2. AirVPN also provides users with real-time user and server statistics, a three-day trial, five simultaneous connections. Overall, I thought it was a solid VPN service. Hide.me is the best all-round secure VPN. Able to unblock streaming platforms, supports P2P downloading, and stuffed with security features. Hide.me Demo Hide.me is a VPN provider from Malaysia that is always considered an excellent choice for anybody who cares about privacy and security. The VPN has a lot of advanced features that you won't find on the majority of VPN services available on the market. This includes a kill-switch, DNS leak protection, obfuscation, and full IPv6 compatibility (making it fully featured in terms of advanced security features). It has secure apps for Android, iOS, Windows, Mac, Blackberry, Linux, routers and browser extensions for Firefox and Chrome. Privacy is always near the top on our list of must-haves for any VPN provider, and Hide.me has a great, robust no-logs policy. You can browse the web, stream, or torrent (Hide.me's servers are all P2P friendly) without feeling like someone's watching. Being based in Malaysia means Hide.me isn't required to keep hold of user logs, so the service would have nothing to hand over even if asked, and we're impressed that Hide.me also invited an independent auditor to validate its no-logs claims. OpenVPN is also available, and it is implemented extremely robustly with an AES-256 cipher and Perfect Forward Secrecy. This makes it one of the most secure VPNs on the market and means you can trust it for privacy purposes. Plus, Hide.me provides port forwarding for anybody who requires it for torrenting. All of these things are important when looking for a secure VPN provider. Hide.me also recently bolstered its product by allowing users to unblock sought-after services such as Netflix US. Plus, you can see how it stands up against our other recommendations thanks to its 30-day money-back guarantee. ProtonVPN is the best customizable secure VPN. With an established pedigree and a handy double-hop feature, as well as a zero-logs policy. Proton Demo ProtonVPN is, as its name suggests, a VPN service from the people who reinvented secure email with the now-famous ProtonMail service. ProtonVPN is based in privacy-friendly and NSA-free Switzerland, and all its apps are super-secure and open-source which is fantastic. I really liked that the Android app is available on F-droid, so if you have ditched Google you can still use it on your smartphone. If you're looking for a forthright and transparent VPN provider, I would have to recommend ProtonVPN – it's one of the few services that actually publishes its audit reports, and all of its apps are open source, too. It's this level of dedication that's led me to feel safe using the service whilst tormenting, as well as the optimized P2P servers! The Windows client and Linux script use OpenVPN, while the macOS, Android, and iOS VPN apps use IKEv2. The OpenVPN settings used are an AES-256-CBC cipher with HMAC SHA-512 hash authentication on the data channel and AES-256 cipher with RSA-2048 handshake encryption and HMAC SHA-1 hash authentication on the control channel. Perfect forward secrecy is provided by a Diffie-Hellman key exchange (key length unknown). IKEv2 uses an AES-256 cipher with RSA-2048 handshake encryption. ProtonVPN uses only bare metal servers and I have never detected an IP leak of any kind when testing the service. Its Windows and macOS clients feature kill switches that are firewall-based but do not use the OS system firewalls. ProtonVPN's SecureCore feature is a double-hop VPN setup designed to foil end-to-end timing attacks. ProtonVPN also has a free VPN service which is really good, however, if you are looking to stream content or torrent then it's probably not suitable for you as it's pretty slow. It is a great tool for improving your internet privacy though. 1. ExpressVPN
Pricing
Pros
Cons
Logging policy
IP Leak detected?
WebRTC Leak detected?
Encryption protocols
Jurisdiction
Website

Strong privacy features
Unbreakable encryption
A selection of protocols
Pricing
Pros
Cons
Logging policy
Encryption protocols
Jurisdiction
Website

Excellent OpenVPN implementation
Outside of the 14 Eyes' jurisdiction
Ideal for VPN newcomers
Pricing
Pros
Cons
Logging policy
IP Leak detected?
WebRTC Leak detected?
Encryption protocols
Jurisdiction
Website

Strong encryption
Great desktop clients
Lots of features
Pricing
Pros
Cons
Logging policy
IP Leak detected?
WebRTC Leak detected?
Encryption protocols
Website

Strong OpenVPN encryption
A no logs VPN
Suitable for streaming and torrenting
Pricing
Pros
Cons
Logging policy
IP Leak detected?
WebRTC Leak detected?
Encryption protocols
Jurisdiction
Website

Advanced security features
Stay safe on public WiFi
Other things you need to know
6. VyprVPN
 www.vyprvpn.com
www.vyprvpn.com
Pricing
Pros
Cons
Logging policy
IP Leak detected?
WebRTC Leak detected?
Encryption protocols
Jurisdiction

A proven no-log VPN
Great security features
The only service to own and maintain all its servers
Pricing
Pros
Cons
Logging policy
IP Leak detected?
WebRTC Leak detected?
Encryption protocols
Jurisdiction
Website

A no logs provider from Romania
Well-implemented encryption
Guaranteed not to leak
Pricing
Pros
Cons
Logging policy
IP Leak detected?
WebRTC Leak detected?
Encryption protocols
Website

Great for privacy, but not for VPN beginners
The techy stuff
On your desktop
Additional features
Pricing
Pros
Cons
Logging policy
IP Leak detected?
WebRTC Leak detected?
Encryption protocols
Website

Advanced features
A private service
Strong encryption protocols
Pricing
Pros
Cons
Logging policy
IP Leak detected?
WebRTC Leak detected?
Encryption protocols
Jurisdiction
A transparent service
Secure apps
Other things you should know
How we research the most secure VPNs - VPN testing methodology
Finding a VPN that offers high-end security is one of the top priorities for most users. However, with so many options on the market, it can be challenging to choose the right one. While military-grade 256-bit encryption is the standard level of protection for most premium VPNs, some offer more advanced features that go to extra lengths to protect your privacy.
To help you understand our process, we've put together this short list of how we find the most secure VPNs.
- What level of security does it provide? At the minimum, we expect a VPN to offer AES-256 encryption with 2048-bit key lengths. This is the standard for most premium VPNs on the market. Anything less than this should be avoided.
- Does it include extra privacy features? In addition to robust encryption, a secure VPN may offer other security features such as a kill-switch and DNS leak protection. A kill-switch prevents your IP address from being exposed if the VPN connection drops, while DNS leak protection ensures that your web traffic is always routed through the VPN server and not your ISP.
- Does a third party audit it? An independent security audit is one of the best ways to gauge how seriously a VPN takes its security. If a VPN has undergone an external security audit, it's a good sign that the company is committed to protecting its users' data.
- What is its logging policy? A no-logging policy is essential for a VPN to protect your privacy truly. This means that the VPN doesn't keep any records of your online activity, making it impossible for anyone to identify you or your web usage habits.
Considering all of these factors, we can be confident we're finding the most secure VPNs on the market. This ensures that our users can browse the web confidently, knowing that their data is always safe and sound. You can find more about our selection criteria in our testing process.
How fast are our recommended secure VPNs?
All of our recommended secure VPNs are fast enough to handle even the most data-intensive tasks, such as online gaming, VoIP calls, and streaming in full HD. To help you better understand what speeds you can expect from our top secure VPN picks, we run speed tests on them regularly and display the most recent results in the table below. This way, you know which VPNs are the fastest right now.
| ExpressVPN | NordVPN | Private Internet Access | |
|---|---|---|---|
| ProPrivacy.com SpeedTest (average) | 100 | 85.9 | 62.2 |
| Speed | 100 | 568.0 | 254.93 |
| Performance | 10 | 9 | 8 |
| Reliability | 9 | 8 | 8 |
 ExpressVPN Discount Coupon
ExpressVPN Discount Coupon What are the different VPN encryption protocols?
In order to establish a secure connection, the VPN software on your device negotiates an encrypted connection with the VPN server. The mechanism used to do this is called the VPN protocol, which uses a series of authentication and encryption algorithms to ensure the connection is secure.
The main VPN protocols you are likely to encounter are:
PPTP – Not Secure
A widely supported VPN protocol that is no longer considered secure. There is very little reason to use it these days, and it should, therefore, be avoided.
L2TP – Will Not Secure Your Data From Surveillance
A widely supported protocol. It's not secure against the NSA, unfortunately, but is still suitable for general use. That said, we'd suggest sticking to IKEv2 and OpenVPN!
IKEv2 – Secure and ideal for Android & iOS
IKEv2 stands for Internet Key Exchange Version 2. The protocol is often referred to as IKEv2/IPSec because IKEv2 is never implemented without the IPSec encryption.
It is generally considered more lightweight and stable than OpenVPN, but it is only available over UDP, which is blocked by some firewalls.
OpenVPN – The most secure VPN protocol
An open-source protocol that is widely regarded as the most secure and versatile VPN protocol available. We generally always recommend using OpenVPN whenever possible (although IKEv2 is also a good option).
WireGuard – Revolutionizing the way VPN protocols are implemented
WireGuard is a promising competitor to OpenVPN that focuses on being a quick, lightweight alternative, only implementing the most important VPN features and a few cryptographic protocols that have been hand-picked to guarantee the highest level of security.
WireGuard does have some problems with recording user IPs internally for Network Address Translation (NAT). To address this, many VPN providers use WireGuard as a base for their own protocol – like NordVPN's NordLynx and ExpressVPN's Lightway protocols.
How do we assess VPN encryption?
Encryption is what keeps a VPN secure, so we spend a lot of time testing and researching how encryption is implemented by VPN services. We primarily focus on the OpenVPN and IKEv2 protocols, and this is because:
- OpenVPN and IKEv2 are the only VPN protocols we know to be fully secure – which is why we recommend you stick to them.
- Just about every VPN service offers OpenVPN. This allows us to compare like for like across services.
- The care a provider takes over the details of its OpenVPN encryption is a strong indicator of the care it takes over security in general.
OpenVPN is made up of several elements – but the devil is in the detail.
The security of OpenVPN comes from how well it has been implemented. Meaning that if OpenVPN has been implemented poorly by a VPN service, then it's no better than the other (lesser) protocols we mentioned above.
Below is a list of the component parts of the OpenVPN protocol:
- Cipher AES-256-CGM
- Control hash auth HMAC SHA-1
- Handshake RSA-4096
- Forward security DHE-4096
- Connection logs
- Traffic logs
We recognize that implementing encryption protocols like OpenVPN to a high standard is a key feature of a secure VPN – so, we made it one of our main considerations when putting together our list of the ten most secure VPN services. Simply put, if we find that a particular VPN service can't implement encryption protocols to a high standard, we don't recommend the service.
We do not accept standard implementations of WireGuard as acceptable for a VPN. While the default WireGuard protocol is highly secure, it has not been designed with privacy in mind.
We prefer to see each VPN provider implement an extended version of WireGuard that mitigates the NAT logging issue. Some providers will solve this problem by periodically wiping their NAT tables or regenerating the keys associated with a certain IP, although this only minimizes the risk, and does not eliminate it. We will evaluate how each provider solves NAT IP logging in WireGuard on a case-by-case basis.
The importance of logging policies
In our opinion, a VPN cannot be considered secure if it keeps logs of your connection and traffic. A VPN that does keep logs is liable to hand that data over to the authorities at a moment's notice. This definitely isn't something you want your VPN provider doing!
Because of this, all of the secure VPN providers we recommend in this guide have strict no-logs policies to ensure that none of your online activity is ever logged while connected to their network. A secure, no-logs VPN will have no data relating to what you get up to when connected to its servers – and therefore won't have anything to hand over to the authorities, even if served with a warrant. A no-logs policy ensures that your online privacy is fully protected.
What is IP leak protection and why is it important?
The second key element to a VPN's technical security is to have IP leak protection.
An IP leak happens when your VPN leaks your real IP address to the website or service you're visiting online. This is hugely dangerous, particularly if you're using a VPN to conceal your identity.
When using a VPN, no website you visit should be able to see your real IP address, or one belonging to your ISP that can be traced back to you. We have tested all the services in the list above to ensure that they do not leak your real IP Address.
How to test for IP Leaks yourself
We recommend testing your VPN service for leaks when you first sign-up for it. You can do this by using ProPrivacy's leak testing tool – and don't worry, we've made the process incredibly easy! All you need to do is follow the on-screen instructions:
- Make sure you are disconnected from the VPN and visit our VPN leak testing tool.
- Read the instructions and click Continue twice.
- Select your country or give the browser permission to access your location. Please note, ProPrivacy does not keep your location or any other information about you on record.
- Connect to a VPN server in a different country. This is important because connecting to a server in the same country can cause the results to be less accurate.
- Click "I've connected to a VPN" and let the automated process begin.
Once completed, your results will be displayed in a digestible format so you will know for certain whether you have a leak or not.
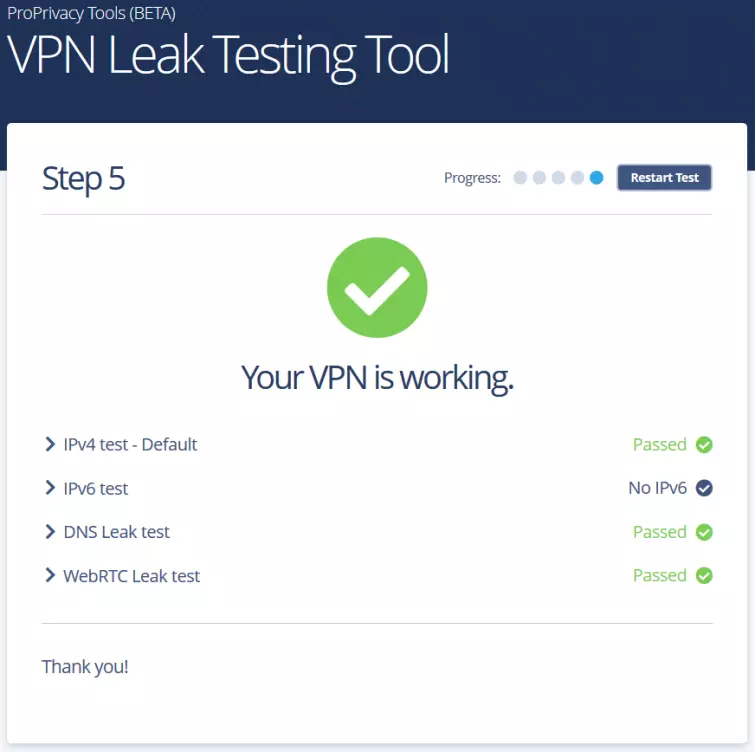
All tests were passed in the example image above, as indicated by the check marks to the right. You can find out more information by clicking on the drop-down boxes. If you instead see a red cross next to IPv4, IPv6, DNS, or WebRTC, then you have experienced a leak. In this case, you can troubleshoot by turning IPv6 off manually and disabling WebRTC, but it might be easier to just switch providers at that point if you detect a leak of any kind.
Check out our guide on how to fix the WebRTC bug if you are experiencing any WebRTC-related issues.
What are Kill-switches?
VPN connections do sometimes drop – for various reasons – and this is something that happens to even the best services. A secure provider will be prepared for this eventuality, however, and ensure your data remains private with the help of a kill-switch.
Kill-switches cut your internet connection the moment they detect a VPN dropout. This prevents your real IP address being exposed for the world to see! Kill-switches typically tend to be either reactive or firewall-based, and you can check out our kill-switch guide for more information about how these handy tools work.
Reactive kill-switches
Reactive kill-switches detect that the connection to the VPN server has dropped, then shut down your internet connection to prevent leaks.
There is a danger, however, that an IP leak could occur during the micro-seconds it takes to detect the VPN dropout and cut your internet connection.
Firewall kill-switches
Firewall-based kill-switches solve the IP leak problem by simply routing all internet connections through the VPN interface. If the VPN is not running, then no traffic can enter or leave your device. Firewall-based kill-switches are therefore better than reactive ones, but any kill-switch is better than none!
Firewall-based kill-switches come in two types. The first kind is implemented in the client, and will therefore not work if the client crashes. The second kind modifies the Windows or macOS firewall rules so that even if the VPN software crashes, traffic cannot enter or exit your device.
The only problem with the second method is that it could, at least in theory, cause conflicts if you use a third-party firewall.
Is a VPN secure enough to bypass government censorship?
If you live in a country where the government imposes widespread restrictions online, you can use a VPN to bypass those blocks. Many people use VPNs in countries like the UAE, to regain access to VoIP apps and make free calls. The same is true in China, where many Western websites are restricted and it is necessary to use a VPN to access Facebook, YouTube, and many other popular sites.
The encryption and location spoofing provided by a VPN can allow you to bypass these restrictions, however, in order to bypass government blocks safely it is imperative that the VPN is secure.
Unfortunately, many VPNs have weak encryption, lapse privacy policies, and dangerous leaks that would allow ISPs to detect the websites you are visiting. These VPNs could pose a danger if you try to access websites or services that have been blocked by the government. This is why it is essential to use a reliable VPN with high levels of security.
The VPNs recommended in this guide all have strong AES encryption, a kill switch that cuts your internet if the VPN connection drops out, and a no-logs policy. Some of our recommendations also have added obfuscation to conceal your VPN traffic as regular HTTPS.
If you are located in a country that has strict online censorship, we strongly recommend that you choose a secure VPN that has all of these features, as this will help to give you the best protection possible and allow your o bypass any VPN blocks imposed using a firewall in those countries.
Can I bypass internet blocks at work with a secure VPN?
Yes. A truly secure VPN will allow you to bypass blocks on any WiFi network. This means that you can use the internet as if you were back at home. The best thing about a secure VPN is that you can not only regain access to any websites or internet services that have been blocked by your employer but also do so with complete privacy. As a result, you can watch YouTube videos, play games, access social media accounts, or do anything else while connected to the work's wifi.
Are there free secure VPNs?
Yes, you can get a reliable free VPN without spending any money – and there are high-quality free services out there that are secure enough to meet our exacting VPN standards. However, it's important to keep in mind that free VPN services typically come with limitations – like bandwidth limits, data caps, fewer server locations, and a minimum of features.
Genuine, privacy-oriented free VPN services are exceedingly rare. So, if you do opt to go with a free VPN, be sure that it does its part to protect your privacy and secure your traffic. The vast majority of free VPNs are either completely useless and provide little to no online security, or they make their money by selling your data to the highest bidder. Some free options can even be outright dangerous to use since they can be crawling with malware.
If you don't mind dropping a few bucks a month for one of the premium services listed in this guide, then you'd really be better off securing your connection with one of our recommended secure VPNs.
Can you get a secure mobile VPN app?
If protecting your online privacy while you're out and about is your main concern, you'll be happy to know that all our VPN recommendations also apply to the Android and iPhone apps as well. A quality, secure VPN provider will keep you secure on smartphones and tablets since it will offer the same privacy protections it offers on other platforms.
In fact, using a VPN on a mobile is the best way to protect your privacy on the go, especially if you're connecting your mobile device to a public Wi-Fi hotspot. Check out our iOS VPN or Android VPN pages for more information about using one on your mobile.
Check if your data has been compromised
Ever wondered whether your data has been compromised? Well, we've got a tool for that! It'll tell you if your email has ever been exposed in a data breach – simply input your email below to find out.
Powered by haveibeenpwned.com
FAQs
Final thoughts
However, a VPN's primary function is shoring up your digital privacy. Connecting to a VPN ensures that nobody will be able to keep tabs on your online activity – including your ISP, government, and nosey cybercriminals.
Now that we've covered what makes a VPN such a must-have tool, let's take a look at our top security-oriented picks:








