Price
Perfect Privacy offers its subscribers three options when it comes to selecting a subscription plan. All of those plans are identical in terms of features, and differ only in that they become cheaper the longer that you subscribe for. This is standard fare for premium VPNs which like to encourage consumers to commit for a longer period of time.
However, unlike most VPNs - which tend to drop the price substantially - Perfect Privacy offers only a small discount. A single month will set you back $12.99, and if you commit for a year that price reduces by just 23% to $9.99 per month. For the largest possible discount of 31%, users must subscribe for two years. However, even then that only reduces the price to $8.95 per month.
This is disappointing and means that Perfect Privacy can definitely be considered one of the more expensive premium VPNs on the market. Whether it is worth paying more for this VPN is largely going to personal requirements and choice.
Perfect Privacy payment options
For anybody that is interested in a subscription, the option is there to test the service thanks to its 7-day VPN money back guarantee. This guarantee is useful and means that those interested in the service can give it a test run if they want to.
Subscribers can opt to pay via credit or debit card, Amex, PayPal, or one of the 60 methods provided by the service PaymentWall. The firm also accepts Bitcoin and Bitcoin Cash payments which are made via the well-known service BitPay. This means that users can opt to pay for the service relatively anonymously if they prefer.
Does Perfect Privacy Unblock Netflix?
If you are looking for a VPN for Netflix, you may want to look elsewhere.
Despite the high price of this VPN, it is unfortunately not a good service when it comes to unblocking popular streams. During our tests, this VPN failed to provide access to either the US or UK Netflix catalogs. In addition, we could not connect to Hulu or BBC iPlayer. This is unfortunate and likely means that this VPN is not active in its attempts to seek out clean IP addresses that are not blocked by those popular services.
Thus, while this service may be considered advanced in terms of privacy and security features, for those who want a simple service for unblocking streams it is better to look elsewhere.
Features
Perfect Privacy is a service that is extremely well-rounded when it comes to advanced security features. For this reason, it is an interesting VPN choice that may be of interest to certain VPN users. Below you can see a comprehensive list of the features provided by this VPN, alongside descriptions of its more unique attributes.
- Servers in 26 countries
- Apps for all platform
- Choice of OpenVPN or IPsec encryption
- Killswitch
- DNS leak protection
- Multi-hop VPN chaining (up to 4 servers can be manually chosen)
- Unlimited number of simultaneous connections
- Obfuscated servers for bypassing ISP firewalls and concealing VPN use
- SSH Manager for establishing HTTP or SOCKS5 proxy connections
- Tor over VPN
- Port-forwarding
- Dedicated bare-metal servers throughout network
- Full IPv6 support
- TrackStop filter provides ad blocking, anti-tracking, and anti-malware (server side).
NeuroRouting feature. This unique server-side multi-hop feature automatically bounces your data via a number of Perfect Privacy servers for added privacy.
As you can see, Perfect Privacy has a large number of interesting features including its TrackStop and NeuroRouting features; both which can be setup server side. Below we will outline some of these rarer features to explain exactly how they can benefit you.
Alternative Choices for You
|
|
From $6.67 |
ProPrivacy.com Score
9.6 out of 10
|
Visit Site Read review |
|
|
From $3.69 |
ProPrivacy.com Score
9.4 out of 10
|
Visit Site Read review |
|
|
From $2.19 |
ProPrivacy.com Score
8.6 out of 10
|
Visit Site Read review |
TrackStop
The nice thing about TrackStop, is that users can set it up to filter out unwanted data from arriving on your machine. This can increase the speed of your internet browsing experience by decreasing page load times and decreasing the load on your CPU. Users can opt to setup the filter manually to block websites and data according to their own specific needs.
This even includes the ability for parents to setup parental blocks from within the VPN; a unique feature that gives parents the ability to protect their children from adult content while still allowing them to gain the digital privacy afforded by the VPN. And, because this feature can be setup server side, it applies to all devices on the VPN network meaning that it can be setup via a router to act as a catch-all parental block for the entire home.
Below we have listed all the different kinds of filtering that can be achieved using TrackStop:
- Tracking and Adblock blacklists over 30,000 tracking and ad domains
- Fraud filter blocks over 45,000 known malware domains and 20,000 phishing domains
- Block Facebook domains and Facebook trackers on all websites
- Block all Google domains (more than 400)
- Social Media filter: block all large social media domains
- Parental filter to block adult content, gambling sites, violent websites and ads that are not suitable for kids
- Fake news filter that blocks a known list of fake news sites websites (via a list that is published and updated on GitHub)
NeuroRouting
This feature uses open-source machine learning (TensorFlow) to automatically bounce your traffic around Perfect Privacy’s network before exiting via the best possible server location. This dynamic multi-hop routing ensures that the exit node used by a subscriber differs depending on which service their traffic is bound for. As a result, the VPN IP address that is visible to each internet service they use is different.
NeuroRouting can be set up to work either with OpenVPN or IPsec and must be set up server-side. This means that NeuroRouting can be set up to work for every instance of the VPN, and will work by default for all your traffic if you install Perfect Privacy VPN directly on a VPN-enabled router.
While this feature has previously been compared to Tor by some reviewers (due to the way it works dynamically and automatically to bounce a user’s traffic via various nodes), it should be noted that this feature helps to provide added privacy; but not anonymity. This is because unlike with Tor, Perfect Privacy does all the routing to bare metal servers under its control. And while it does not store any logs of what its users do while connected to its servers - it is possible that the firm could monitor traffic in real-time as it passes through its network.
So, why is this feature interesting? With NeuroRouting, you don’t need to constantly disconnect and connect to different server locations in order to use geo-restricted services in those countries. Instead (as long as Perfect Privacy has a server in that location) you will automatically get a local IP that lets you appear to be in the country the service is based in. This kind of automated multihop is unique to Perfect Privacy, and it is great in terms of ease of use for subscribers.
Speed and Performance
Here at ProPrivacy.com we use a custom, server-based speed checking system to monitor VPN connection speeds in real-time. Our unique server-based solution checks VPNs for maximum (burst) speeds and average download speeds across four server locations - four times per day.
These connection speeds are updated in real-time to assess what the fastest services are on our fastest VPNs page. Our custom speed testing system tests VPNs with OpenVPN encryption enabled, and it tests both local and international connection speeds from test servers located in Hong Kong, the UK, the US, and the Netherlands.
Unfortunately, when our DevOps added Perfect Privacy to the speed test system, their servers all timed out. Downloads were so slow that the test runner app killed tests after 2600 seconds. As a result of not being able to get any data, we were forced to resort to testing the VPN manually using the online speed test resource speedtest.net.
We tested Perfect Privacy on a 50Mbps BT internet connection in the UK. We tested the connection to get base results with no VPN connection and found it to be getting download speeds of around 49 Mbps. Next, we connected to a UK VPN server and tested it three times. We found download speeds dropped by just under a half to 27Mbps. Upload speeds when from 17 Mbps without a VPN to 14 Mbps with. These results are pretty good and mean that the VPN should perform fine for streaming in HD.
To check its international server we decided to speed test its Amsterdam server in the Netherlands. The Netherlands server performed a touch faster than the UK server, a surprise considering that the data must travel further. Download speeds of 29 Mbps mean that, again, this server is going to perform well for streaming. Finally, we decided to check the connection speeds of an East Coast server in the USA. Unsurprisingly, considering the distances involved New York did perform a little slower. We clocked in average download speeds of 18 Mbps, which would still allow me to stream in HD without any trouble.
Overall, we were pretty impressed with the speeds provided by this VPN, and while it might not be the fastest VPN in the world, it definitely has what you need to stream and do other data-intensive tasks while connected to the VPN.
IP leaks, DNS leaks, and WebRTC leaks
In order to establish that a VPN is functioning properly and that it is correctly providing the privacy it claims, it is essential to test it for leaks. Leaks could potentially ruin the privacy being provided by the VPN, rendering it useless.
We used the well-known tool ipleak.net to check for leaks on both an IPv4 and IPv6 connection. We did the tests in incognito on a Virtual Machine to ensure fair and unadulterated results on both Mac and Windows. Our tests revealed that the VPN suffers from no leaks, meaning that Perfect Privacy is reliable for privacy purposes and concealing your location.
We tested the VPN and found it to have no IPv4 or IPv6 leaks, DNS leaks, or WebRTC leaks. This is excellent and means that the VPN works as it is intended to. Full IPv6 compatibility is a rarity, most VPNs simply block IPv6 connections and revert back to IPv4. However, with Perfect Privacy the tunneling works over IPv6 with no issues.
To test your own Perfect Privacy connection for leaks visit websites like ipleak.net, test-ipv6.com, or our own leak testing tool.
Test Your VPN for IP Leaks
Since reviewing this VPN service, we have created our own VPN leak test. It is easy to use and 100% reliable.
Privacy and Security
Perfect Privacy is a VPN service based in Switzerland; a location that is generally agreed to be great for digital privacy. In Switzerland, the government tends not to throw its weight around and it is very rare that it will use warrants to coercively make firms part with data about consumers. It is for this reason that Switzerland is thought to be a good place for privacy services to be based, and why privacy services such as Proton Mail, Proton VPN, and VyprVPN are also based there.
On the whole, we consider this zero-logs VPN to be true to its name. Its privacy policy is GDPR compliant and it gives no indication that any connection logs whatsoever are being collected. And, because this VPN provides high-end privacy features and strong encryption (see more below) this VPN can be considered particularly strong when it comes to providing privacy for its subscribers.
Encryption Protocols
Perfect Privacy focuses on providing two VPN encryption protocols; OpenVPN and IPsec/IKEv2. Those protocols are both considered secure, which means that subscribers will be fine to use either.
As is always the case with custom VPN clients, the iOS client only provides access to the latter-mentioned IPsec/IKEv2 protocol. As a result, anybody wanting to make use of OpenVPN will need to use the third party OpenVPN connect app (this is true of all VPNs and is not a negative aspect of this particular provider).
While IPsec/IKEv2 is considered secure, here at ProPrivacy.com we tend to recommend OpenVPN encryption. This is because it is a highly audited and secure VPN protocol that is agreed to provide the highest levels of privacy and security. To those ends, here at ProPrivacy.com we always analyze each VPN’s implementation of the protocol to ensure it meets our minimum standards. We asked Perfect Privacy VPN to provide us with those implementation standards and the VPN told us the following:
- Control channel: An AES-256 cipher with HMAC SHA384 hash authentication. RSA is used to secure the TLS handshake, but we are not able to ascertain the default key length used. Perfect forward secrecy is achieved using a DHE key exchange.
- Data channel: an AES-128-CBC cipher with HMAC SHA-512
Those implementation standards are secure, and the addition of tls:crypt on the control channel is an added layer of security. The only thing stopping us completely appraising these encryption standards is our lack of knowledge of the TLS handshake key length. However, it seems fair to presume that it uses OpenVPN minimum default standards (RSA-2048).
As you can see, this VPN also provides Perfect Forward Secrecy using Diffie Hellman Ephemeral (DHE) keys, which adds to the overall security of the protocol. As a result, this VPN can be trusted to provide watertight privacy and there is no reason to worry about the VPN tunnel being cracked for a long time into the future.
User Experience
Perfect Privacy is a VPN provider that runs on well designed and implemented apps for all platforms. It is even compatible with Amazon Fire Stick, Raspberry Pi, Synology, and a large number of routers (AsusWRT, AsusWRT Merlin, pfSense, DDWRT, Tomato, eBlocker).
The website is generally well laid out and provides a good amount of information about what the VPN has to offer. On the other hand, it is worth mentioning that the website is a little lacking in terms of important technical data (such as the OpenVPN implementation details mentioned above). However, this is a minor quibble, and it is possible to contact customer support for information if needs be.
One thing we did notice is that the NeuroRouting feature page is overly boastful and makes some bogus claims such as “In the best case, the traffic is not exposed to the Internet at all.'' Your traffic has to pass over the internet (including passing encrypted through your ISP’s servers in order to get to the VPN servers, it must pass over the internet between server hops, and it must pass over the internet to get to the website you are visiting. This kind of overt misrepresentation (for the purpose of making sales) is a little unnecessary considering that the feature itself is unique, and potentially attractive in its own right to users who need or want it.
The website’s leak test page is a useful feature that can check whether the VPN is working correctly, however, we would tend to recommend sticking to using a trusted third party service to run these tests.
The Windows client
We tested the Perfect Privacy Windows client thoroughly to get a good idea of how it performs. We found it to be easy to set up and use, and it has all the important VPN features you would expect.
While the client certainly isn’t the most exciting app to look at, it does provide a lot of excellent information. Available bandwidth gives you an idea of how much load a server is being exposed to, so that you can pick a server that will give you better performance.
One thing we did notice is that Perfect Privacy takes quite a long time to establish a connection. However once a connection is established it remains stable. This is a testament to the stability of its bare-metal server network.
Clicking on settings allows you to opt between IPsec and OpenVPN. OpenVPN connection comes on UDP by default, but clicking on Program Settings permits you to change to TCP if you prefer. This window also allows you to configure the encryption by opting for various ciphers variations. Consumers looking for slightly better speeds can fall back to AES-128 without any concerns about privacy.
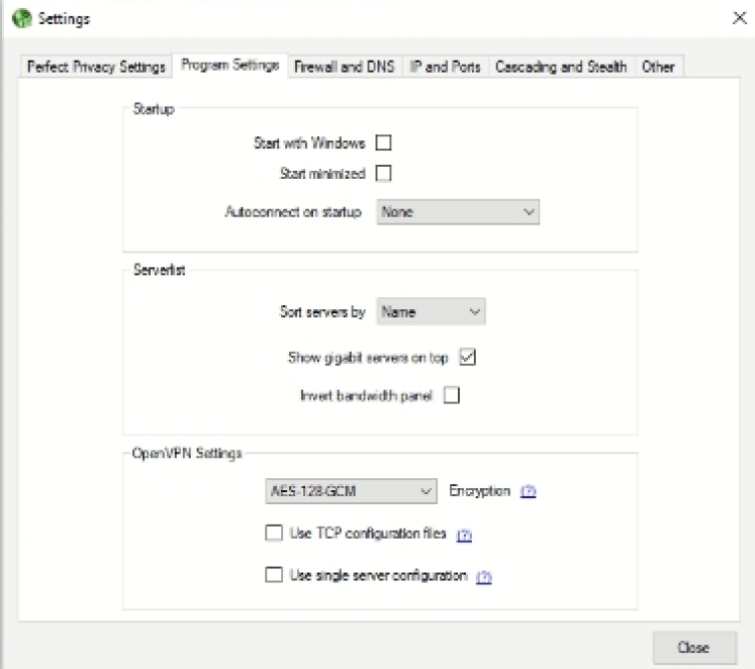
One little niggle is that the app does not clarify whether the VPN implements L2TP/IPsec or IKEv2/IPsec. We generally recommend sticking to OpenVPN, which we presume is set up to run over UDP as this provides better speeds for streaming.
Some other notable features are the full IPv6 DNS leak protection, port forwarding, customizable multiphop, auto-connect, and customizable firewall settings (VPN killswitch).
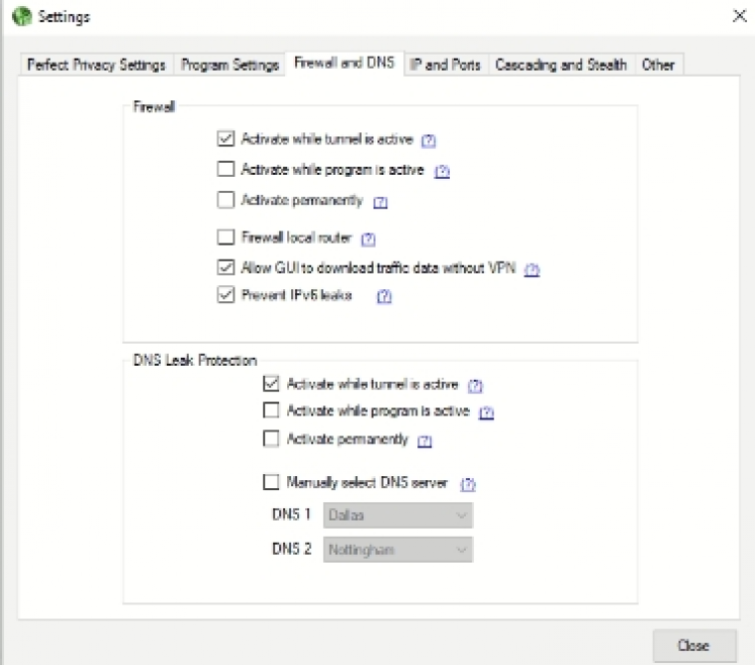
Clicking on the IP and Ports tab followed by Use random exit IP lets you select a randomized IP address on the server that you connect to. This means that if the VPN server you opt for has multiple IPs, you will get a different IP each time. Honestly, it is hard to consider this a feature considering that this is what most VPNs do automatically and it is recommended by Perfect Privacy that you leave it switched on.
For automatic cascading multihop head to the Cascading and Stealth tab followed by enable cascading; users can opt for up to 4 hops. We enabled this, but could not tell if anything was occurring because the exit server still registered the same on IPLeak.net, this is possibly due to the fact that it gives you three random hops before you arrive in your selected endpoint.
We tested the NeuroRouting feature by enabling it in the member’s area. This is supposed to mean that our traffic bounces around various servers and exits close to where the final destination is.
Next, we headed over to two different IP tools to see if the server-side features were resulting in different exit points. The good news is that while the DNS addresses are still resolved at the location you manually select, the IP address changed to the Netherlands for IPleak.net, and Canada for IPleak.org. Thus, it appears that the feature does work as advertised.
Stealth is available using Stunnel, Obfsproxy3, or SSH - which is a massive amount of choice. And, the client even permits you to manually select which Perfect Privacy server handles your DNS requests.
Overall, we found this client to be feature-packed. We tested the filters and found them to work fine, as long as you restart the VPN client. The Google filter stopped us from being able to access Google search and Youtube. The social media filter stopped us from accessing Facebook and Twitter. Ads appeared to be blocked successfully on a site that is notorious for serving a lot of ads. In addition, the child protection filter stopped PornHub from loading. Thus these features, which can be set in the member's area, all seem to work excellently.
Other clients
In addition to the Windows client that we tested thoroughly, Perfect Privacy also has apps for Android, and Mac that we took for a test run.
Mac
The Mac VPN client has all the same features as the Windows client, and while we did not give them an in-depth test run like we did on Windows, we can only presume that the settings work in entirely the same way. However, it is worth mentioning that the Mac client has a completely different look to its WIndows counterpart, and it generally much cleaner to look at.
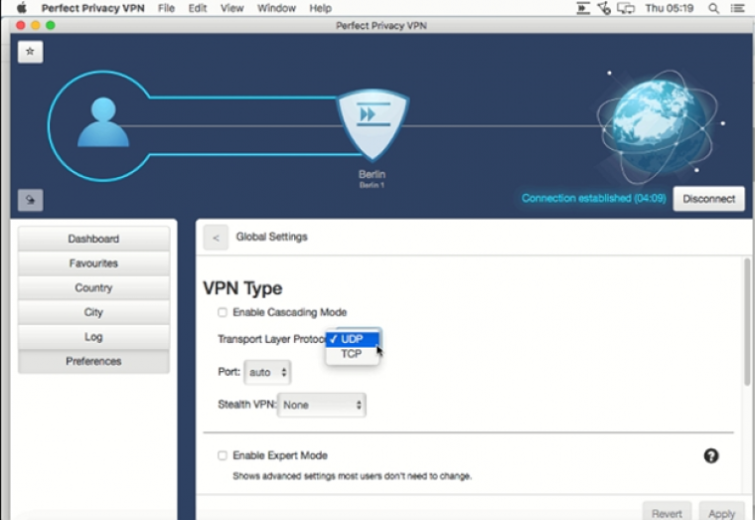
As is the case on Windows, users can opt for either OpenVPN UDP or TCP. However, users can not alter the cipher to Camelia or change the strength of the AES encryption as was the case on Windows.
We tested the client for leaks and found that it suffered from none. IPv6 connections are disabled automatically in this client, which ensures that the VPN connection works flawlessly over IPv4.
Other notable features include the Killswitch which must be toggled on in “expert” mode. However, this client does not have port forwarding, multihop, cascade, or stealth mode as is the case in Windows. Thus, this Mac client is a much more standard VPN client with the basic essentials for protecting your privacy.
The good news, is that Mac users can still enable ad blocking and other filters, as well as the NeuroRouting feature from inside the member's area - and this will still work as advertised.
iOS
Unfortunately, Perfect Privacy does not have a custom iOS VPN app. In order to use this VN on an iPad or iPhone, you will need to download .ovpn config files to connect using the third-party OpenVPN connect client.
This is a slight drawback, however, the firm does provide a walkthrough for setting it up this way. And the Connect client is excellent, meaning that you will be able to use this VPN without too much trouble. However, it is worth noting that OpenVPN connect for iOS is a basic client that does not offer any of the advanced features available on Windows.
Android
We downloaded the Android VPN client and gave it a quick test run to check what features are available. We found this client to be the nicest to look at.
However, it is completely lacking in advanced features. The client lets you connect and disconnect and that is all. No killswitch is available and you cannot use any of the advanced features you get with Windows.
Customer support
Considering the cost of this VPN, it is fair to say that support is an area where it is severely lacking. No live chat support is available, which means that you will need to use its FAQs or the ticket system in order to ask questions. We found the guides and the FAQs to be useful, and they definitely answer most of the important questions people are likely to ask.
Sending a ticket off with a request is not hard, and you do get an automated response to let you know that the question has been received. From that point on it is a waiting game. However, we found the firm to respond extremely quickly and they did provide the answers we required.
We would prefer to see this VPN add a live chat feature to its member's area. However, as long as you know your way around a VPN and don’t mind communicating via the email ticket systems this shouldn’t cause you too much grief.
Final thoughts
Perfect Privacy is a VPN that can be considered fairly average on all platforms but Windows. As a Windows VPN it comes into its own, providing a huge number of features that are unavailable with many providers on the market. The zero-logs policy is a winner, and being based in Switzerland certainly puts it out of reach of invasive governments such as the US and the UK.
While this VPN isn’t as premium in terms of feel and looks like many other VPNs on the market, it certainly can get the job done. And as long as you don’t mind the lack of a killswitch - the Android client is Okay.
The fact that this VPN lets you use your account on an unlimited number of devices is good. However, the VPN does remind you that it is for a single person’s use only. However, the VPN keeps no logs and it does not monitor simultaneous connections - meaning that it must rely on people's honesty for fair use.
Due to the cost of this VPN we are a little unimpressed with this VPN overall. If you are looking for a Windows VPN with specialist features, then this VPN is worth considering. And if the NeuroRouting feature appeals to you, this VPN is worth a test run.
However, the experience when using this VPN on anything but Windows is pretty average and it is hard to consider it good value for money. Perhaps if this VPN was cheaper it could come more heavily recommended for anything but Windows.
On the other hand, this VPN does provide a 7-day money-back guarantee - so you have no reason not to test it if any of its unique VPN features interest you. Definitely worth a test run if you are looking for a Windows VPN.
0 User Reviews
Leave a Review
Thanks for your review!
15 Comments
Write Your Own Comment
Your comment has been sent to the queue. It will appear shortly.

C
Ray Walsh replied to C
C replied to C
Douglas Crawford replied to C
myself
Douglas Crawford replied to myself
Arkanum
Douglas Crawford replied to Arkanum
Willian Waznes