Linux Operating systems are widely reagrded as being better for privacy and security than their Mac and Windows counterparts. One reason for this is that they are open-source, which means they are much less likely to be hiding backdoors for their developers, the NSA, or anybody else.
It is for this reason that Linux distros are the Operating System of choice for security professionals and privacy advocates as well as for the majority of computer servers around the globe.
There are plenty of Linux distros to choose from. And this can make it confusing for anybody wanting to move away from Windows in favor of something more secure. Even existing Linux users may be slightly unsure as to which Linux distro they ought to be using if they value privacy and security.
In this article, we will walk you through two of the best Linux distros for protecting your data and staying clear of hackers.
Which Linux flavour should I choose?
All Linux distros have specific peculiarities and advantages, meaning that they all do slightly different things. However, there are two Linux distros that stand out where privacy is concerned...
Qubes OS
The best Linux distro for privacy & security
Download: Qubes
Based on: Fedora OS
Why is Qubes good for privacy?
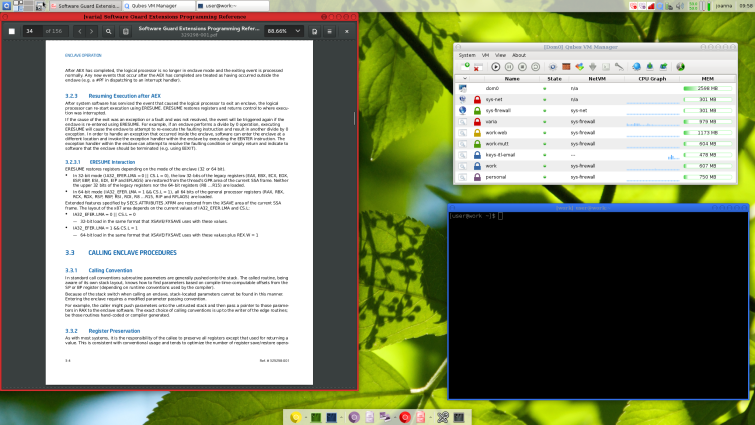
Firstly, Qubes works by isolating and virtualizing various Virtual Machines, thereby promoting "security by isolation”. This ensures that any risky app you might run is confined to a separate Virtual Machine (VM). As a result, Qubes protects your data by isolating it into completely sandboxed environments.
What is nice about Qubes, is that the desktop uses color-coded windows to easily identify virtual machines with different security levels. This makes it easy to keep track of your workflow in the various VMs.
In Qubes, the network stack and WiFi drivers run in a dedicated, unprivileged network VM (NetVM). This reduces the attack surface making it much less vulnerable to hackers. In addition, Qubes OS is firewalled by default so that no incoming ports are open. TCP and ICMP timestamps are disabled by default.
Qubes also makes it possible to protect against user data leaks by setting an empty NetVM field for the corresponding VM. These are all top-notch features that help to provide security and privacy while networking.
To protect users against the possibility of persistent malware across VM reboots, Qubes ServiceVMs can be set up as a Static DisposableVM. A disposable VMs can be used to quickly open untrusted apps, links, attachments, or anything else perceived to be a possible threat.
For added security, hardware threat minimization is in place that ensures microphones are never attached to VMs by default. And, to improve security users can opt to use a Yubikey for authorization purposes - which will protect against password snooping, and bolster USB keyboard security. What’s more, it is possible to isolate the USB stack in a dedicated USB VM, which protects the administrative domain (dom0) from untrusted USB devices.
Finally, Qubes implements full-disk encryption by default (it uses LUKS dm-crypt), and users can manually configure their encryption parameters if they wish. This ensures that data is always secured between sessions.
As is the case with many Linux Distros, Qubes is tricky to use and is definitely not for the "average” consumer. However, you do install Qubes directly (rather than booting up each time from a CD); which does make it better for day-to-day use than Tails.
To install the OS safely onto your machine, you should always verify the digital signature on the downloaded ISO. Because it is possible that the ISO server could have been compromised, it is also worth noting that immediately after installing the latest version of Qubes (4.0.1) you will need to upgrade manually all of your Debian and Whonix TemplateVMs in order to patch the APT update mechanism vulnerability that was discovered since its release.
Once authenticity has been verified you can opt for an installation medium such as a DVD or a USB stick. Anybody who wants to can install Qubes on a USB stick and boot from it (though this will be much slower than an internal hard drive it can be good for testing). However, you cannot install Qubes in a virtual machine; it won’t work.
Overall, Qubes is a highly stable OS that is not prone to crashes and that is built from the ground up with privacy and security in mind. It also makes extremely efficient use of system resources, which is great for performance.
TAILS
The best Linux distro for remaining anonymous
Download: Tails
Based on: Debian
Why is Tails good for privacy?
Tails is a Linux distro (based on Debian) that is generally accepted as being the best for users who want to remain super-anonymous online. When we use the internet, we are constantly monitored; cookies are placed on our machines to track us as we visit websites and our IP address is tracked.
Tails is designed to completely solve these problems and others. It is for this reason that Tails is the Linux distro of choice for whistleblowers like Edward Snowden or journalists like Glenn Greenwald.
Unlike Qubes which you can install directly on your machine - and can use day to day - Tails is designed to always run off a LiveCD. This ensures that it leaves no traces on your computer. The whole point of Tails, in fact, is that you never save anything permanently to your hard disk. When you finish a session, you reboot your PC, wipe the machine’s RAM; and it is like you were never there at all!
For this reason, Tails is not really an option for a daily driver (and should only be used by people who require secure single session functionality). Anybody wanting a daily driver should stick to Qubes or Whonix.
So, why is Tails so good for privacy? Tails route everything through Tor so that you can never be tracked online. This gives you complete anonymity. The anonymity provided by Tor’s onion network (added to the fact that the OS never leaves any traces behind after each session) makes Tails extremely appealing to users who want to ensure their data is never susceptible to intrusion or data theft. Remember, that while Qubes encrypts your disk for security - Tails solves the problem by literally guaranteeing that nothing is ever left behind. This is called an amnesiac system.
Tails can be booted from a LiveCD, USB, or SD card. However, it is much more secure to always boot from a LiveCD. This is because a CD is permanently burned and can not be altered (this is not the case with the other boot mediums; which are susceptible to malware).
Let it be said that Tails is not for the faint-hearted. It is complicated, hard to install, and only runs on certain computers. However, if you have a Linux-friendly machine (without a high-powered video card or some other hardware that might mess things up) you should be able to get it going.
It is also worth noting that while it is possible to get a stable setup going, there are many ways that users can accidentally ruin their own security settings. As a result, this OS really is for advanced users who have the knowhow (and patience) to get it working correctly.
For those users, a Tails LiveCD can even be used to boot a session in an internet cafe or library. Even if a computer has Windows on it, Tails users can boot from the CD and the PC will ignore Windows and sideload Tails onto the machine; providing a fresh session loaded in RAM that completely disappears when the PC is rebooted. And, the most recent versions of Tails can even hide you within a local network, performing MAC address spoofing to make you harder to track.
Once inside a booted version of Tails, users gain access to specialist versions of applications for web browsing, email, chat, etc. Those applications are specifically hardened for privacy, which might take some getting used to. On the plus side, it is a useful collection of open source programs ideally suited to Tails users. And Tails employs state-of-the-art cryptography to encrypt your files, emails, and instant messaging to make them secure while in transit.
Overall, Tails is an advanced Linux distro that is ideal for anybody wanting to avoid tracking and gain privacy online, while also retaining a completely neutral and clean machine. It is not for people who want to use the internet on a day-to-day basis - to browser normal websites and services.
In addition, Tails is not effective at protecting against cyber attacks with exploits and root exploits. For this kind of functionality Qubes and Whonix are a better option.
Best Linux distro for privacy (beginners)
The Linux distros mentioned above are considered two of the best for privacy (both have very specific capabilities that makes each better for different use cases and threat models). However, there are others such as Whonix (a privacy distro that connects to Tor and boots in a VM) that may also be of interest to specific users.
What it is important to remember is that there is not really a "best” Linux distro for privacy - because they all do slightly different things that may be better for individual use case scenarios.
It is also worth noting that the Linux distros mentioned in this article are not considered suitable for beginners making their way over to Linux for the first time. For those users, it is better to opt for a Linux distro such as Mint or Ubuntu.
Those versions of Linux are considered better than Windows and Mac for privacy and security - because they are open source. However, they are also much more suited to regular day to day use.
The nice thing about those Linux distros is that they are bloat-free, better for system performance, and free! So, if you want to move over to a more privacy-conscious environment consider Ubuntu or Mint before working up to more advanced versions of the OS.
