It's old news that intelligence agencies like the NSA and the CIA like to use citizen’s technology against them. In fact, just recently the NSA altered the mission statement on its website to remove "honesty,” "trust,” and "openness,” from its core values. That seems pretty hilarious considering that James Clapper lied to Congress about Prism back in 2013. Honesty, it seems, was never particularly high on the NSA’s agenda.
Last year, news emerged via Wikileaks’ Vault 7 which revealed that the CIA regularly uses people’s mobile devices and smart TVs to snoop on them. In her book American Spies, Jennifer Granick paints a crystal clear picture of the types of loopholes employed by US authorities to place Americans under surveillance.
Ongoing snooping is occurring and will continue to happen. Indeed, just two weeks ago Congress approved the reauthorization of Section 702 of FISA. That legislation contains amendments that will allow US intelligence agencies to snoop on US citizens during the course of spying of foreigners. Yet more loopholes. At least the NSA was honest enough to remove honesty from its mission statement.
Bitter Taste
Now, news has emerged that reveals the US government has gotten a taste of its own medicine. A bitter taste has been left in the US' mouth at the hands of a popular electronic device - just like the ones it would usually appropriate to snoop on citizens.
The device in question is called a Fitbit. It is an innocuous-looking fitness monitoring gadget that people wear on their wrists. As well as recording the wearer's heartbeat, number of steps taken, and calories burned, the device uses GPS to keep tabs on the jogging routes taken by its users.
Fitbit’s developer Strava - which considers itself "the social network for athletes" - regularly publishes a map of around 27 million people’s jogging routes. Last November, that global database of exercise "hotspots” was updated, what it revealed has sent a shiver down US Central Command’s spine.

A training route around a suspected CIA base in Mogadishu has been revealed.
Military Bases Spotted
The chain of events began when US military personnel were issued Fitbits as part of a program to help them monitor their own fitness activities. At the time, it seemed like a reasonable plan. That is until last Saturday, when Nathan Ruser, an Australian student and analyst for the Institute for United Conflict Analysts, suddenly Tweeted that the Fitbit "heatmap” had made US military bases "clearly identifiable and mappable."
Somewhat disconcertingly, some of the obviously highlighted bases are supposed to be top-secret military compounds within the US and around the world.
With egg all over its face, the Pentagon has come forward to admit the unintended oversight. In a statement made on Monday, spokesperson, Col. Rob Manning, commented that the US Department of Defense would be reviewing its policy regarding smartphones and wearable devices:
"We take these matters seriously and we are reviewing the situation to determine if any additional training or guidance is required, and if any additional policy must be developed to ensure the continued safety of DoD personnel at home and abroad.”
Manning added that Defense Secretary, James Mattis had "been very clear about not highlighting our capabilities to aid the enemy or give the enemy any advantage, so that would be our approach going in on this one as well."
Too Late?
So, how much damage has been done? What is known, is that in 2013 around 2200 soldiers were issued Fitbit Flex wristbands. Then, in 2015 that program was expanded and 20,000 more soldiers and military personnel were given a Fitbit as part of a program called "Performance Triad."
According to the Australian student the Fitbits appear to have caused a very serious intelligence leak. This is what Ruser said on his Twitter account:
"If soldiers use the app like normal people do, by turning it on tracking when they go to do exercise, it could be especially dangerous. This particular track looks like it logs a regular jogging route. I shouldn't be able to establish any Pattern of life info from this far away."
Going by the military bases Ruser has discovered, it would appear that military personnel who were issued a Fitbit were not informed of the need to turn off GPS logging to Stava’s servers. Scott Lafoy, an open-source imagery analyst, says it is too early to say just how damaging the data might be. However, he admits it is troubling:
"In terms of strategic stuff, we know all the bases there, we know a lot of the positions, this will just be some nice ancillary data. From the site, it's possible to identify individuals' running routes. Tracking the timing of movements on bases could provide valuable information on patrol routes or where specific personnel are deployed.”
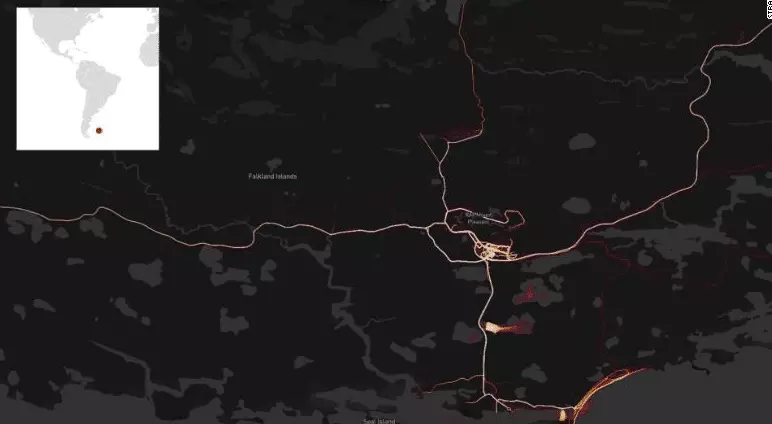
What seems likely, is that foreign military and intelligence agencies will be rushing - not only to see if they can pinpoint secret US bases - but also to find out if their bases have also been compromised. In the image below, the Strava map clearly "heats-up" an RAF base at Mount Pleasant in the Falklands: proving that it isn't just US military that has been affected.
Perhaps most troubling, is the prospect that militants in the Middle East and Africa could use the maps to track American soldiers’ movements. In theory, that intelligence could lead to an incursion at the hands of those militants. Lafoy commented:
"If the data is not actually anonymous, then you can start figuring out timetables and like some very tactical information, and then you start getting into some pretty serious issues."
The good news is that Strava has issued a statement saying that it is happy to cooperate with the US military to conceal parts of the map that it feels could be damaging. How long this will take, and how much damaging information might leak in the meantime is hard to say.
Opinions are the writer's own.
Title image credit: A. Aleksandravicius/Shutterstock.com
Image credits: Screenshots taken from Stava's heatmap
