Welcome to this guide on proxy servers. We'll guide you through everything you need to know about both proxies and proxy servers.
What is a Proxy Server?
A proxy server (or "proxy”) is a computer that sits between your computer and a wider network. This "wider network” is usually the internet.
So a proxy server acts as an intermediary between your computer and the internet.
How Does a Proxy Work?
A proxy, much like a VPN will hide your Internet Protocol (IP) address from anyone on the internet. A website will see the IP address of the proxy server, instead of your real IP address.
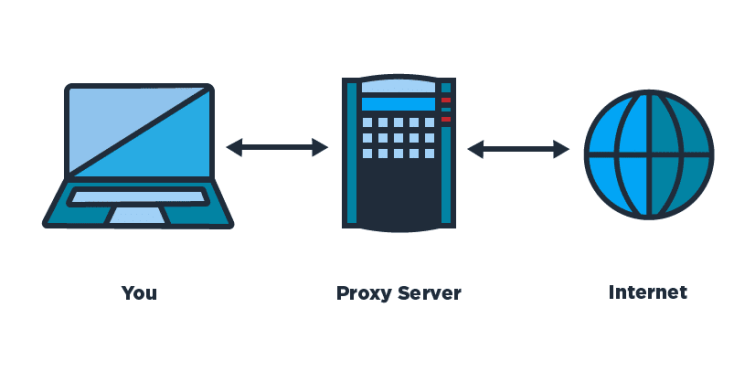
You will appear to access the internet from wherever the proxy server is physically located. If the proxy is located in a different country to where you are, you will appear to access the internet from that country.
Disadvantages of a proxy server:
- Whoever is running the proxy will be able to monitor all your unencrypted internet traffic. Note that most secure websites protect your connection using HTTPS. This includes banks, email services, and online shops. As with your Internet Service Provider (ISP), when you connect to an HTTPS website the proxy owner can see that you are accessing a website. However, it cannot know what you get up to on that site.
- The proxy owner will also know your real IP address.
Many (but not all) proxies use encryption. This means that it will encrypt the traffic between you and the server.
- When using an encrypted proxy, your ISP cannot see what you get up to on the internet.
- ISPs usually cooperate with government surveillance. Therefore, encrypted proxies can be effective at preventing blanket, un-targeted government surveillance.
- The proxy owner will still be able to monitor traffic when not connected to HTTPS websites, as it is the proxy server that encrypts and decrypts traffic entering and exiting it.
- You will need to trust your proxy provider
Both Virtual Private Networks (VPNs) and the Tor Network are specific examples of encrypted proxies.
Public and Free Proxy Servers
A public proxy is a proxy server that someone makes available free of charge to the general public. In theory, these usually are run by well-meaning volunteers. Alternatively known as free or open proxy servers, public proxies come in unencrypted (HTTP), encrypted (HTTPS), and Socket Secure (SOCKS, which may or may not be encrypted) flavors.

The most significant advantage of public proxies is, of course, that they cost no money to use. The fact that you can freely switch between proxies located all over the globe also has privacy benefits. However:
- They can be very unstable and regularly go offline without notice.
- They also tend to be very slow.
- You have no reason to trust the proxy operator who can snoop on all internet traffic that does not connect to an HTTPS website or service.
- Many proxy servers are run by criminals. Indeed, it is calculated that almost 70% of free proxies are not safe!
- In addition to snooping on unencrypted web traffic, almost 40% of free proxies actively tamper with your data as it passes through them. 18% are guilty of injecting HTML into static web pages viewed (ads), while 20.6% inject JavaScript.
- On the flip side, the proxy owner can get into trouble for any illegal activity you perform! This is because it looks as if that activity is coming from their server.
I strongly recommend against using free public proxies. If you absolutely must, then only connect to websites and services using HTTPS. And never use a public proxy that bans the use of HTTPS. The only possible reason for it to do this is so that it can snoop on or interfere with your web traffic.
Really… just don’t! Note that similar issues plague a free VPN.
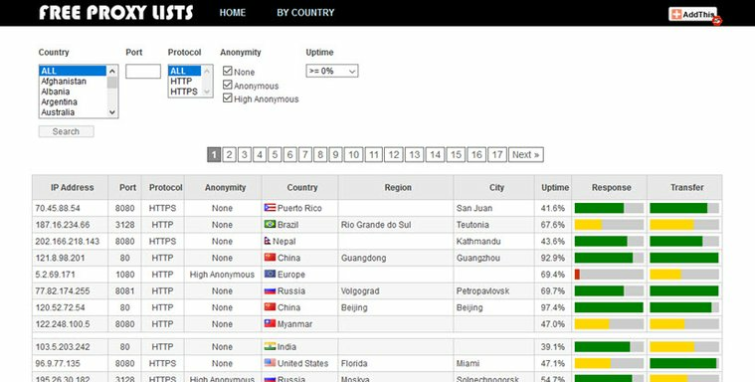
Free Proxy Server List
Unlike some other websites, we will not recommend any free proxy servers as there is just no reason to trust them.
If you do wish to use a public proxy, then Google will provide you with plenty of free proxy server lists.
Private Proxy Server
Individuals or companies can run their own private proxy servers for their personal use, or the use of their staff. The term "private proxy,” however, also refers to commercial proxies that offer the use of their server(s) for a fee. VPNs are by far the most common form of private commercial proxy.
Private proxies and VPN services are generally much faster and more reliable than free proxies. The fact that they are businesses rather than random individuals also makes them a known quantity that can be held to account.
Indeed, many VPN companies have built up fearsome reputations for their dedication to security and privacy. That said, it is essential to take care to choose a reputable VPN service.
The same advice holds true for all commercial proxy services, but thanks to the popularity of VPNs, other forms of commercial proxy service represent a fairly small and unexamined market. No proxy-only services that I am aware of have built up the reputation, or received nearly as much scrutiny, as the big-name VPN companies.
It is worth noting that some VPN companies also offer more conventional HTTP/HTTPS or SOCKS proxy servers.
Types of Proxy Server
HTTP Proxy
HTTP is the standard protocol used to connect elements of the World Wide Web. Importantly, connections to HTTP servers are not encrypted.
On the plus side, no encryption means vastly reduced computational overheads. This means HTTP proxies can readily accept multiple connections without severely impacting internet speeds for users. Note, however, that the physical distance your data must travel will impact your internet speeds.
An HTTP proxy interprets network traffic. This allows it to do high-level things with the traffic. Such as search its cache to see if it can serve a response without going to the destination. Or consult a whitelist/blacklist to see if a URL is allowed.
By default, HTTP proxies are "blind” to Transmission Control Protocol (TCP) traffic and will just ignore it. This makes them great for accessing unencrypted HTTP web pages, but little else.
HTTP proxies can handle TCP traffic if the HTTP CONNECT method is used, but its use is entirely dependent on the proxy owner. Because the HTTP protocol cannot interpret the TCP traffic, all TCP traffic is simply forwarded. This gives HTTP proxies that use CONNECT much of the flexibility of SOCKS proxies.
You must configure each software client to connect to the proxy. The same is also true of HTTPS and SOCKS proxies.
HTTPS Proxy
HTTPS stands for HTTP Secure (or HTTP over SSL/TLS). Any website that needs to secure users’ communications will use it. When you connect to an HTTPS proxy, it will encrypt all the data between you and the server.
HTTPS uses TCP port 443, so all HTTPS proxies must use the HTTP CONNECT method in order to establish a TCP connection.
SOCKS Proxy
Socket Secure (SOCKS) proxies work at a lower level than HTTP proxies. They do not try to interpret web traffic, and just pass along all requests they receive. This makes them much more versatile than regular HTTP proxies.
SOCKS proxies can handle all kinds of internet traffic, including POP3 and SMTP for emails, Internet Relay Chat (IRC), and File Transfer Protocol (FTP) for uploading files to websites. They can also handle torrent traffic, which is why SOCKS proxies are sometimes referred to as "torrent proxies.”
Due to this flexibility, SOCKS servers usually handle a much higher volume of traffic than HTTP servers. This means that SOCKS proxies are generally much slower than regular proxy servers.
SOCKS5 is the latest version of the SOCKS protocol and adds various authentication methods. This is useful for commercial providers who wish to limit access to their proxy servers to customers only.
The SOCKS protocol fully supports HTTPS, and it is common for SOCKS proxies to encrypt traffic in this way. One downside, however, is that SOCKS proxy connections are not as well supported by software clients as HTTP proxy connections. To find out more, check out our VPNs with SOCKS5 guide.
For more information about using a VPN when torrenting, see our best VPNs for torrenting guide.
Web Proxy
Web proxies allow you to connect to a proxy server from inside your browser window. This proxy server can be either an HTTP or HTTPS proxy. Web proxies are usually free and have the advantage that you do not need to download and install any extra software or configure your browser settings. They are therefore very easy to use.
Many free proxy websites, however, fund themselves using extensive advertising. Web proxies are also poor at handling complicated webpage layouts and tend to fall flat when encountering things such as Flash, Java, and JavaScript scripts (although this not necessarily a bad thing!). VPN provider Hide.me also offers a free web proxy.
Forward Proxy
Other than reverse proxies (see below), all proxies discussed in this article are technically referred to as forward proxies.
They sit between your computer and a broader network, which usually means the internet. Under this setup, you connect to the proxy server which then connects you to the internet.
Reverse Proxy
As its name suggests, a reverse proxy does almost the opposite of a standard forward proxy. It sits between the internet and a much smaller group of servers.
A typical setup would be a reverse proxy acting as a gateway between the internet and a corporate Local Area Network (LAN). In order to access resources on the LAN network, you would first need to connect to the reverse proxy.
In addition to acting as a gateway, the reverse proxy can protect the entire network using HTTPS. It can also perform load balancing, content caching, data compression, and other tasks useful to corporate LAN networks.
Transparent Proxy
Transparent proxies are so-called because they require no configuration on your part. You often don’t even know that you are using one.
Transparent proxies have many good uses. For example, content filtering in libraries, or to authenticate users of public WiFi. That sign-in page you see in your browser when you connect your laptop to the WiFi in Starbucks? That is a transparent proxy in action.
Reverse transparent proxies are often used by websites to protect against DDoS attacks. Transparent proxies can be a pain, however. If not implemented well, issues with caching and authentication can arise.

Browsers may also detect the proxy server and determine that it constitutes a security risk. In this case, they may refuse all connections through the proxy server.
Although potentially very annoying, there is a good reason for browsers to do this. Use of transparent proxies is a classic form of Man-in-the-Middle (MitM) attack. In these cases, the attacker redirects your traffic without your knowledge to a malicious server that can then intercept it.
In the library example above, I mentioned "content filtering” in a good context. But there is another word for it – censorship. ISPs, for example, can use transparent proxies to filter content on political, social, and religious grounds.
Note that using a VPN, encrypted proxy, or just connecting to an HTTPS webpage will prevent a transparent proxy from snooping on your web traffic or filtering content.
You can use a VPN, encrypted proxy, or a HTTPS webpage, to prevent a transparent proxy from snooping on you.
Just to prove that life is never simple, proxy lists often rate servers based on their anonymity level. I will discuss this in detail a little later, but proxies that provide very little "anonymity” are rated as transparent proxies.
Residential proxies
A Residential proxy is a proxy server which is operated by an internet service provider (ISP), rather than by a data center. This has the following advantages:
-
The IP is a "real” IP, so it will never get blacklisted by the likes of Netflix because it owned by a data center known leasing out IPs for VPN or proxy use. Datacenter IPs are sometimes viewed as being "shady” because they hide a user's real IP. Residential IPs are, to all intents and purposes, real IPs.
-
It points to a real physical address. Just not your real physical address. Which is great if you are serious about geo-spoofing your location.
Residential IPs can be shared or exclusive. They are a relatively new product on the market, although companies such as Bright Data are helping to popularize them. As with all proxies, how private a residential proxy is depends on its supplier.
The Tor Network
The Tor network is free and aims to provide users with true anonymity. It does this by routing all internet connections through at least three random nodes. These "nodes” are really just volunteer-run proxy servers.

The data is re-encrypted multiple times – each time it passes through a node. Each node is only aware of the IP addresses "in front” of it, and the IP address of the node "behind” it.
This should mean that at no point can anyone know the whole path between your computer and the website you are trying to connect to. The main downside is that the Tor network is very slow to use.
Proxy URL
A proxy URL is not really a proxy (server) at all! It is a web address (URL) that forwards to another address. The most common use for proxy URLs is to evade censorship blocks.
Proxy vs. VPN
As noted earlier, VPN servers are a specialized form of proxy. The primary differences between VPNs and regular proxies are:
- VPNs work at the system level, rather than on a per-app basis. Therefore, it only needs configuring once.
- They use a variety of encryption protocols, which are usually very strong.
In general, VPN connections are more secure and easier to configure than regular proxy connections. This makes commercial VPN services more popular than commercial proxy services. This, in turn, has allowed some VPN services to establish very good reputations.
How To Use a Proxy
Private proxy services (including VPNs) will provide you with all the details you need to connect to their servers. They often supply very detailed setup guides.
Except for VPNs, you must individually configure each program (or app) you use to connect to the proxy server. To connect to a proxy, you need its IP address (proxy server address) and port number. You may also need a username and password if authentication is required.
There are estimated to be "hundreds of thousands” of public proxies on the internet. To find one, just type "free proxies,” "public proxy servers,” "open proxy list,” (or similar) into your search engine.
To configure a proxy server in Firefox, go to Options -> General -> Network Settings -> Settings. Select "Manual proxy configuration:” and enter the IP address and port number of the server.

Exclude localhost, 127.0.0.1 (default setting) if you want to access local network resources such as printers and NAS drives unproxied. Configuration details depend on the individual software, but hopefully, you get the idea.
Anonymity Levels for Proxies
Many proxy lists categorize proxies based on the level of "anonymity” they provide. Just to be clear, these ratings relate to what websites and other internet resources see when you are using the proxy.
The proxy owner knows exactly who you are from your IP address, and can monitor your non-HTTPS internet traffic. Thus you are never "anonymous.” It would, therefore, be better to describe these ratings as privacy ratings. They come in three levels, with Level 1 providing the highest degree of privacy.
Transparent Proxies (Level 3)
The confusingly named transparent proxies forward a great deal of information about you to any website you visit. They, therefore, provide almost no privacy and are primarily used for caching (which is why they are often called caching proxies).
Technically, a transparent proxy (in this context) will hide your real IP address, but only very superficially. Your real IP address still appears in the request header sent to the webpage and is therefore very easy to find out.
Anonymous Proxies (Level 2)
So-called anonymous proxies provide a much higher level of privacy. They hide your IP address from any website you visit but do not hide that you are using a proxy server.
Indeed, anonymous servers usually identify themselves as proxy servers by attaching "FORWARDED” headers to each page request.
Elite Proxies (Level 1)
Also known as high anonymity proxies, elite proxies will not only hide your IP address but will also not alert a website (or another internet resource) that requests are being made via a proxy.
The website will, of course, still know the IP address of the proxy server. Elite servers tend to be the most popular kind of open server, which also means they can be the slowest.
Proxy exclusivity
Commercial proxy providers sometimes categorize proxies based on exclusivity. The more exclusive a proxy is, the more it will cost.
- Dedicated/ exclusive proxy – you have a proxy all to yourself. Having a dedicated proxy also usually means that you have a static IP address. Dedicated proxies are likely to provide better performance than ones shared with others, and are useful for evading IP blocks such as those imposed by Netflix. On the other hand, they are less "anonymous” because that IP address is only yours.
- Semi-shared proxy – usually means that you share the proxy with three other people.
- General proxy – same as a free proxy that anyone can use – so in all likelihood you will share that proxy with many other people.
Conclusion
Proxies are very popular and can be very useful. Open proxies, however, tend to be slow and unstable. They are also dangerous to use. Commercial HTTP/HTTPS and SOCKS proxy services provide a much more satisfying experience and are much safer to use.
There is a reason, however, why these are not as popular as VPN services. For a similar price per month, VPN services are easier to configure, protect your entire internet connection, and usually use stronger encryption. Many (but by no means all) have also established strong reputations as reliable companies that will protect your privacy.
Recommendations
In theory, it would be possible to recommend some commercial proxies, but we cannot do this without reviewing a wide selection of services on offer.
We may get around to this at some point in the future, but at present, we have no grounds for recommending one proxy service over another.
What we do know about, however, are VPNs! And as I have discussed in this article, VPNs are almost always better than proxies!
