In this tutorial, we take a step-by-step look at how to set up KeePass 2.x. Please check out our full KeePass Review to find out more about this popular open-source password manager that secures your passwords using strong end-to-end encryption.
KeePass is a Windows-only program, but cross-compatible ports are available for macOS, Linux, Android, and iOS. This tutorial covers KeePass itself, desktop ports such KeePassXC for Windows, macOS, and Linux, work in a very similar way.
We may look at KeePassXC in more detail in a future article, and Android users can check out our KeePass2Android review.
How to set up KeePass password manager
1. Download, install and run the latest version of KeePass 2.x. KeePass1.x now exists only for backward compatibility reasons. Many businesses, for example, require this backward compatibility, but there is no reason for new users to choose it.
2. Go to File -> New… (or click the icon in the main window’s taskbar), click and select a location for your new .kdbx file.
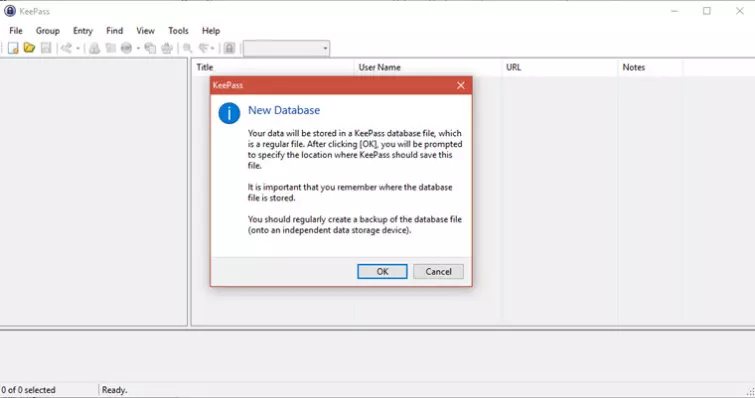
This .kdbx file is the encrypted container which houses your saved passwords. Because it is in-and-of-itself securely encrypted, you can securely store it anywhere. If you plan to sync passwords across devices, then you may as well save it to a cloud storage folder now.
3. Create a master password. Or better yet, a master passphrase (a sentence made up of a number of words separated by spaces).
This master password protects all your other passwords and be should the only password you ever need to remember again! It, therefore, needs to be strong, but also one that you won’t forget. KeePass provides a handy estimated quality bar to encourage you to pick a strong master password.
If you forget it, then its game-over as far as accessing your saved passwords is concerned. If you do need a backup, then write the password down on a bit of paper and store it offline somewhere safe.
If you are happy using just a master password to secure your .kbdx file, then click OK. For additional 2FA security, check the Show expert options box.
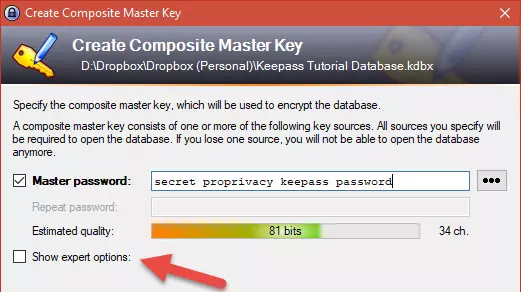
As well as a password, you can bind a key file and/or your Windows User Account to the composite master key.
We’re going to create a key file but will not bind the .kbdx file to a Windows User Account because we want to access our KeePass database from non-Windows devices.
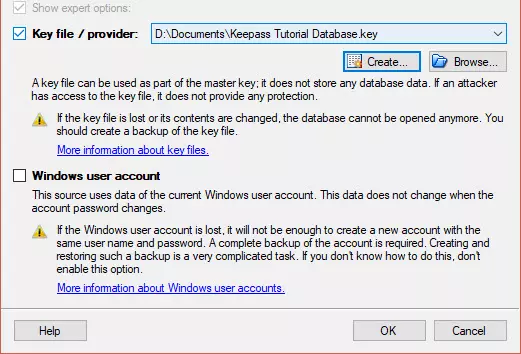
If creating a key file, then simply follow the instructions. When you are done, hit OK. Be sure to store this key file somewhere safe offline. To use the KeePass database on other devices, the key file must be present, but never transfer it online. You can transfer offline using memory cards, USB sticks, USB cables, and suchlike.
4. You can tinker with the database settings if you like, or just hit OK to go with the defaults.
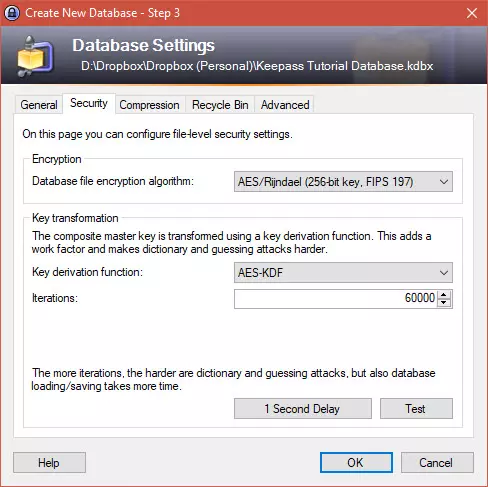
You will be provided the option to printout important database details (filling in your password by hand). If you do this, then store the printout somewhere safe offline.
5. Double-click your new .kbdx database file to open it. Enter your password and (if used) the path to where the associated .key file is stored. If you specified a Windows User Account when you created the database then you must be logged into it to open the file.
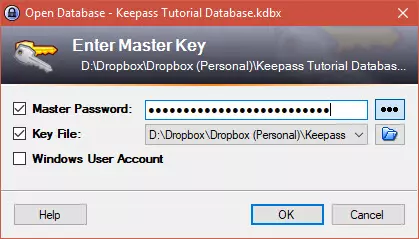
KeePass remembers recently opened databases, making this process fairly painless in day-to-day use.
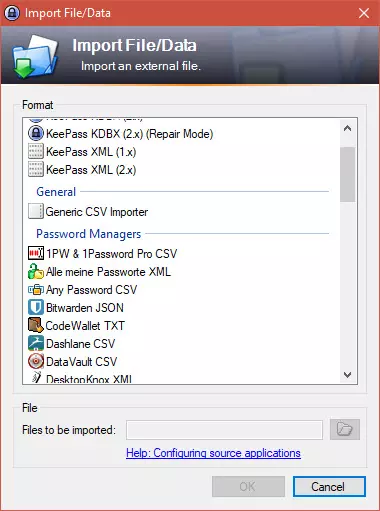
6 (optional). Go to File -> Import… to import passwords from another password manager. KeePass supports files exported from most popular password managers, Firefox, and Chrome.
Your KeePass database is now ready to use! You can manage passwords and cut-and-paste them wherever you want. But to get the best from KeePass you will really want to implement browser integration…
Browser integration
Browser integration is achieved using a combination of plugins + browser add-ons. Others exist, but we recommend KeePassHTTP-Connector.
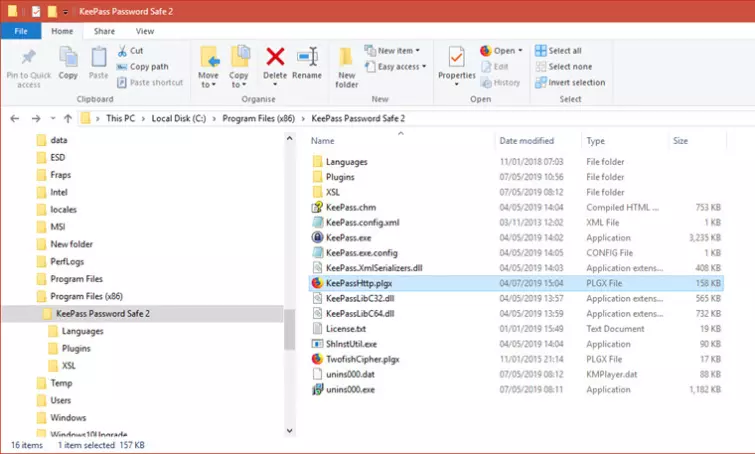
1. Download the KeePassHttp plugin and copy it to your KeePass installation folder (C:\Program Files (x86)\KeePass Password Safe 2 by default).
2. Install the KeePassHTTP-Connector browser add-on for Firefox and/or Chrome.
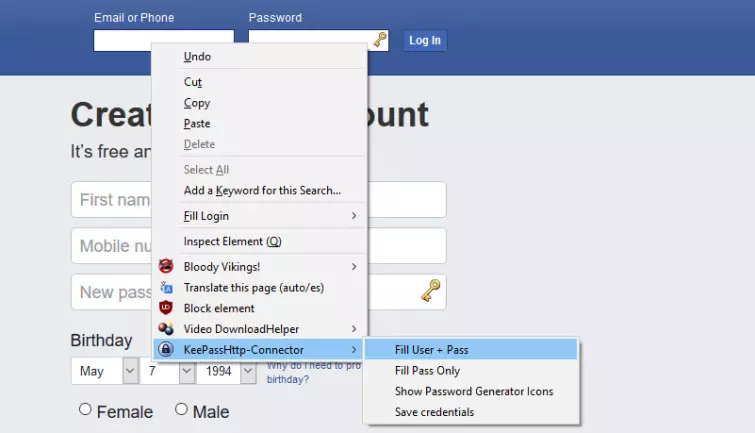
Left-click on any username or password field in webpages for KeePassHTTP-Connector to auto-fill the details from your open KeePass database. Alternatively, you can right-click for more options.
If you aren't happy with KeePass, why not check out some alternative password managers?
