Alternative Choices for You
|
|
From $6.67 |
ProPrivacy.com Score
9.6 out of 10
|
Visit Site Read review |
|
|
From $3.69 |
ProPrivacy.com Score
9.4 out of 10
|
Visit Site Read review |
|
|
From $2.19 |
ProPrivacy.com Score
8.6 out of 10
|
Visit Site Read review |
Why Tunnelblick VPN?
Most commercial VPNs offer custom Mac VPN apps, so why use Tunnelblick VPN? One reason is that it is open source, so you can be fairly confident that it is not doing anything it shouldn’t.
Now… I am usually a very strong advocate for using open source software, but I have doubts about its value when it comes to VPNs, as your VPN provider has full access to your internet traffic anyway. Please see Custom vs. Open Source VPN Clients for my full thoughts on this issue.
Open source aside, Tunnelblick always stays up-to-date with the latest version of OpenVPN, and the latest security patches for it. This means that Tunnelblick is more secure than many custom clients, which can lag behind in this area. It is also bloat-free and stable, which is more than be said for many custom VPN apps.
It is also worth noting that macOS is not quite as well supported by custom VPN clients as Windows is. Small and new VPNs, in particular, often rely on Tunnelblick to provide Mac support. Given how good Tunnelblick is (especially now that it features a kill switch), I do not see this as a problem.
Features
Tunnelblick offers the following features:
- Full Domain Name System (DNS) leak protection – both Internet Protocol version 4 (IPv4) and Internet Protocol version 6 (IPv6). Note that Tunnelblick does not support IPv6 routing, and so prevents IPv6 DNS leaks using the simple expedient of disabling IPv6 (optional).
- Web Real-Time Communication (WebRTC) leak protection*
- Kill switch (latest beta version only)
- Available in many languages – Tunnelblick is currently translated to more than 35 languages.
For more information on IP leaks when using a VPN, please check out my Complete Guide to IP Leaks. Note that DNS leak protection is not enabled by default, and must be turned on (see How to use Tunnelblick later).
*OpenVPN 4.2.x protects against Web Real-Time Communication (WebRTC) leaks, so I presume Tunnelblick does too. Certainly, I detected no WebRTC leaks when testing Tunnelblick for this article.
Additional OpenVPN features
Simple edits to the OpenVPN configuration file(s) allow for a high level of customization (if supported by your provider). This includes port selection, cipher selection, cipher bit-length selection, and the choice of running OpenVPN over User Datagram Protocol (UDP) or Transmission Control Protocol (TCP).
This last allows you to run OpenVPN over TCP port 443, which is a great way to defeat censorship blocks (although horribly inefficient from a technical standpoint).
Pretty much every VPN service provides OpenVPN configuration (.ovpn and .conf) files that can be used by Tunnelblick. Tunnelblick can also use special Tunnelblick configuration files (.tblk), but regular OpenVPN configuration files no longer need to be converted into this format to work with Tunnelblick.
Price
As with OpenVPN GUI, Tunnelblick is free in every sense of the word. In order to use it, however, you will need to connect to a VPN server. It is possible to setup your own privateOpenVPN server, but this usually means paying for a commercial VPN service.
Please check out our 5 Best VPN Services and 5 Best VPNs for macOS pages to see some recommended VPN services. Most VPNs have dedicated Tunnelblick setup pages, but you can use their OpenVPN setup files with Tunnelblick even if they don’t.
Privacy and security
Tunnelblick is community developed open source software built on top of the open source OpenVPN protocol. Being open source means that its code can be checked by anyone qualified to do so, but so far the code has not been professionally audited for vulnerabilities or backdoors.
OpenVPN itself, however, has been.
Ease of Use
Here are the steps to use Tunnelblick
1. Download Tunnelblick or regular OpenVPN configuration files from your chosen VPN service. You will need one file per VPN server location, although it’s often possible to download multiple configurations in a single zip file. In this case, you’ll need to unzip the files before they can be used.
2. Download, install and launch Tunnelblick. It will ask for your Admin password. On the Welcome screen, select “I have the configuration files.”
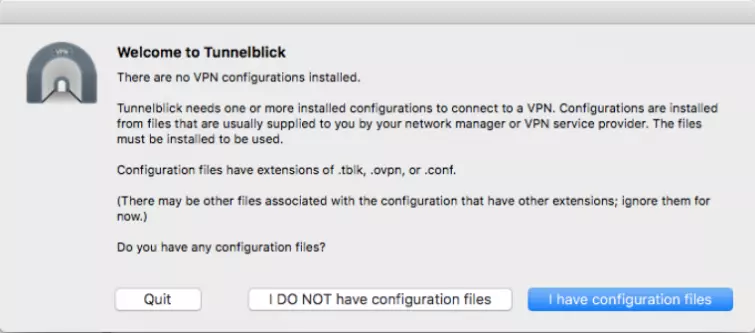
3. Drag the configuration file (or multiples files for multiple server configurations) to the Tunnelblick icon in the menu bar.

4. Hit “Install,” then choose whether to install just for yourself or all users of your Mac. It will probably ask for your Admin password.
5. And that’s setup done! To connect to a VPN server, click on the Tunnelblick icon in the menu bar and select a VPN server.
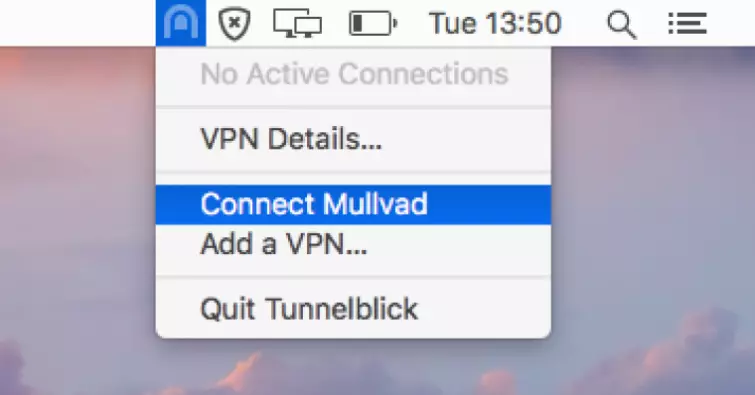
The icon will turn a darker shade to indicate that you are connected. If you hover the cursor over it, it will display additional information.
Addendum:
Turn on DNS leak protection
As already noted, IPv4 and IPv6 DNS leak protection are not enabled by default in Tunnelblick. To enable DNS leak protection go to Configurations -> Settings and tick the boxes next to “Route all IPv4 traffic through the VPN” and “Disable IPv6.”
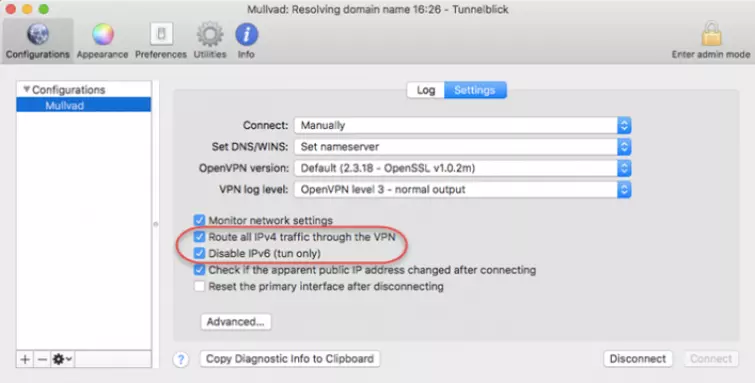
For more information on leaks when using a VPN, check out our Complete Guide to IP Leaks
Turn on the kill switch
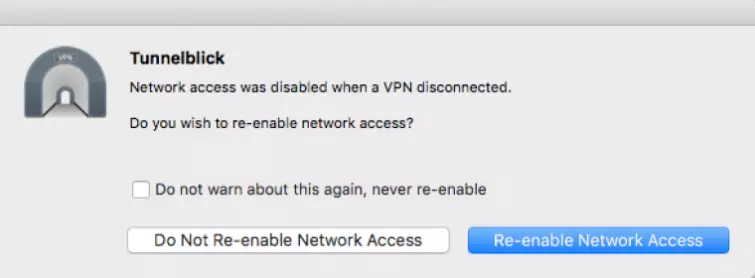
New to the latest beta version of Tunnelblick is a very welcome kill switch feature. This ensures that your real Internet Protocol (IP) address is not exposed in the event of a VPN dropout.
To enable the kill switch, go to Configurations and click on the individual VPN configuration (the kill switch must be enabled for each configuration). Click on the “On unexpected disconnect” field and select Disable Network Access from the drop-down menu.
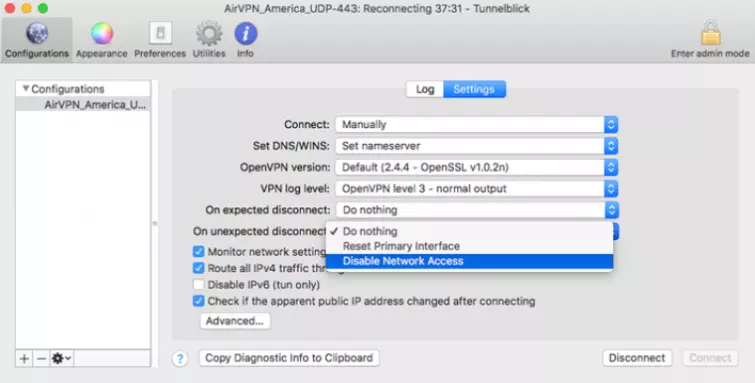
I ran a couple of tests to ensure the kill switch works correctly. The client was running inside a Virtual Machine (VM). Disconnecting then reconnecting the host machine’s internet connection is a good way to simulate a standard VPN drop-out.
In this test the internet stopped working and I could not reconnect until I disconnected from the VPN. So all good and well. I also tested to see if it is a firewall-based kill by simulating a software crash. This is easily done by force-closing the VPN client and seeing if an internet connection is still available.
Customer Service
Despite being free community developed open source software, quite a lot of support is provided to Tunelblick users. This mainly in the form of extensive documentation, which includes a handy quick start guide and FAQ. There is also a Common Problems section, which addresses the … er… most common problems you are likely to encounter.
If all else fails, there is a Google-hosted discussion forum in which Tunnelblick developers appear to play an active part in answering queries.
Final Thoughts
I liked
- Free and open source (FOSS)
- IPv4 and IPv6 DNS leak protection
- WebRTC leak protection
- Always uses the latest version of OpenVPN
- Firewall-based Kill switch (latest beta version only)
- Can use any regular OpenVPN config file
I wasn’t so sure about
- Not quite as easy use as some custom VPN clients
I hated
- Nothing
Tunnelblick is a simple but effective open source VPN client that works with all OpenVPN configuration files. With DNS leak protection, WebRTC leak protection, and a firewall-based kill switch, it also offers all the key features that really matter in a VPN client.
0 User Reviews
Leave a Review
Thanks for your review!
3 Comments
Write Your Own Comment
Your comment has been sent to the queue. It will appear shortly.

Dr.S
James Alton
Douglas Crawford replied to James Alton