Pricing
Tutanota offers a very useful free plan, although its premium plan is hardly expensive. A pricier pro plan is also available, but this only really makes sense for businesses and the like. If you buy a yearly subscription, then Tutanota throws in two months for free.
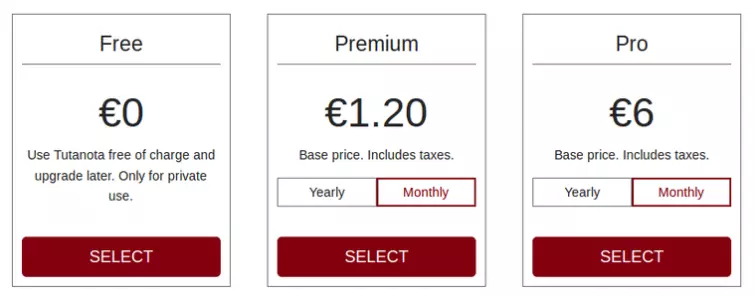
Plans can be tailored to your needs by adding storage and email aliases at varying costs. Monthly subscriptions auto-renew by default.
Enterprise features such as calendar sharing and white label functionality are also available, although are not covered in the review. Non-profit organizations (NPOs) are offered a 50% discount.
You can start with the free plan and upgrade at any time. Payment is via card or PayPal. Cryptocurrency payments are not accepted yet, but are on Tutanota’s roadmap.
Features (base Premium Plan)
- E2e encrypted emails to other users
- Can also send e2e encrypted emails to and receive them from non-Tutanota users
- The entire email is encrypted - subject, body, and attachment
- E2e encrypted storage
- E2e encrypted address book
- No ads
- No IP logging
- No phone number required (but also no anonymous payment yet)
- Strips IP from sent emails
- Attachments up to 25 Mb
- 1 Gb storage
- Custom domains
- MTA-STS support for custom domains
- Unlimited search
- 5 aliases
- Inbox rules with smart filters
- Encrypted calendar
- Web app
- Android and iOS apps
- Desktop clients for Windows, macOS, and Linux (all beta)
- Open-source
- Eco-friendly
- Spam detection
- 2FA support
- Secure Connect (see below)
- Secure password reset
It is worth noting here that Tutanota does not use or support PGP, which may be a sticking point for some. Also not supported is the retrieval of emails via SMTP in third party email clients, as this would not guarantee end-to-end encryption for data.
Free users cannot use custom domains or aliases, have more limited search capabilities, and cannot set Inbox rules. On the other hand, free users can use Tutanota anonymously, since the only meaningful data Tutanota retains is payment details.
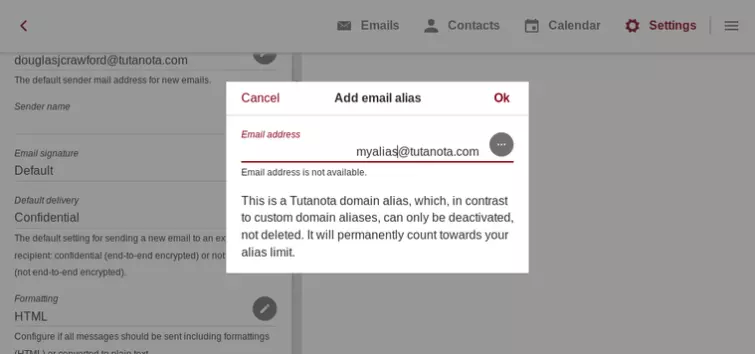
Aliases
Aliases are alternative email addresses tied to your account. You can have up to five aliases on the base premium plan, with the option to purchase more.
Unlimited search
Every aspect of an email can be searched, for, including a full-text search. The ability to search your emails may seem unremarkable, but being able to securely search encrypted data is no easy task. When a search is enabled, data is indexed and the search index stored locally (and can use up more memory on your device).
Encrypted calendar
One of the biggest inconveniences when moving away from services such as Gmail, is that many secure alternatives do not provide calendar functionality. Tutanota does, and it is easy to import your existing calendars using standard iCal files.
Eco-friendly
The Tutanota data centers use 100% renewable energy.
2FA supported
Two-factor authentication is supported via U2F security keys (such as the YubuKey) and via TOTP authenticator apps such as FreeOTP+, as well as OTP, Authenticator, and Authy.
Secure Connect
Secure connect is an encrypted contact form that allows visitors to a website to contact its owners confidentially. Although this review concentrates on Tutanota as a personal email service, this feature just too cool not to mention.
Privacy and security
Jurisdiction
Tutanota and its servers are based in Germany. This is a country known for its strong data privacy laws, and in 2018 was the first country to fully align its data protection legislation with the GDPR.
Despite this, it has enacted the now invalid-on-human-rights-grounds EU Data Retention Directive into local law. This came into force in 2016 and requires all telecommunications and internet service providers to retain user metadata for up to 10 weeks. According to Tutanota, however, the law explicitly excludes email communications.
Germany is a close ally of the United States, with the NSA basing its European headquarters in the country. The 2016 Communications Intelligence Gathering Act authorized Germany’s Federal Intelligence Service (BND) extensive powers to monitor all internet traffic entering and leaving the country.
It should be noted, though, that thanks to Tutanota’s use of secure end-to-end encryption, even if emails are intercepted, then only a very small amount of metadata is exposed.
Logs
Tutanota does not log IP addresses (unless required to in specific cases by law). It also strips IP addresses from sent emails, although it can still see the sender, the recipient, and when the email was sent
The recipient email service will also be able to see this metadata. Other than that, all data is automatically encrypted both in the mailbox and in sent emails. This includes subject, content and attachments.
Tutanota clearly tracks subscriptions and payment details for paying customers.
Open-source
Tutanota’s web application and clients are all fully open source. This means that anyone qualified to do so can examine the code and audit it for weaknesses and deliberate backdoors.
Tutanota’s backend is not open-source, although this is planned for the future. This has invited criticism, but it should be stressed that encryption is performed client-side so it shouldn’t really matter what’s going on server-side.
Tutanota says that its web application was independently audited by Syss GmbH (way back in 2011), but we can find no corroboration for this, let alone an actual report of its findings. For what it's worth, the apps are just wrappers for the web application.
Technical security
All encryption is performed client-side before it leaves your device, meaning that Tutanota offers end-to-end-encryption (e2ee).
Emails between Tutanota users are encrypted using “a standardized, hybrid method consisting of a symmetrical and an asymmetrical algorithm.” These being AES-128 and RSA-2048, respectively.
In an age of almost ubiquitous AES-256 symmetric key encryption, the use of AES-128 might raise the odd eyebrow. But it is cryptographically secure, and a stronger key schedule makes it arguably more secure than AES-256.
Emails to non-Tutanota users are encrypted using AES-128. Passwords are hashed using bcrypt and SHA256. Connections to the Tutanota servers are secured using TLS. You can further improve the security of TLS connections by installing the DANE browser add-on.
This all sounds very secure, although a problem with all browser-based cryptography is that it is vulnerable to malicious code being pushed from compromised servers. Since the stand-alone clients are basically wrappers for the web interface, we presume this also applies to them.
Tutanota is even doing its best to future-proof itself, knowing that emails stored today could easily be decrypted with the next leap in technology. Partnering with the L3S Research of the Leibniz University of Hanover on a project dubbed PQmail, Tutanota hopes to make the service resistant to quantum computing. Of course, we can't talk much about the technology until it becomes a reality.
MTA-STS for custom domains
It is also worth noting that Tutanota has now teamed up with Let’s Encrypt to provide full name SMTP Mail Transfer Agent Strict Transport Security (MTA-STS) not only for primary mail domains but also for user-created custom domains.
MTA-STS is an important new standard that improves the security of SMTP by allowing domain owners to opt into strict transport layer security that requires authentication and encryption. This improves security by preventing targeted downgrade attacks and DNS spoofing attacks.
This is a rare feature, because the vast majority of email services do not provide this important security measure for custom domains at all. And it is nice to see Tutanota now providing automatic handling of TLS certs for custom domains.
Password reset
Interestingly, for an e2ee service, it is possible to reset your password using a recovery code. This recovery code can only be viewed by signing into your encrypted mailbox, and it is recommended that you store it offline somewhere.
The Tutanota website provides a huge amount of information, including good FAQs and plenty of easy-to-follow setup guides. Premium users can also ask for help via email.
Ease of use
In addition to the web console, Tutanota offers apps for Android, iOS, Windows, macOS, and Linux.
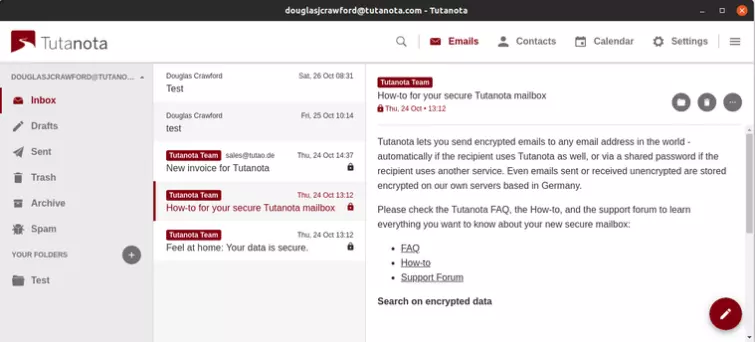
The web console
The beating heart of Tutanota is its web console, where you can do all the things you would normally expect of an email client. It even comes with an optional dark mode!
Premium users can configure sophisticated Inbox rules.
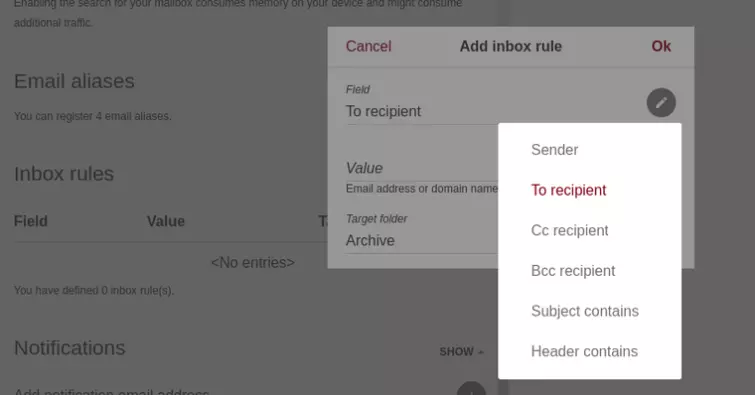
Emails sent to other Tutanota users are seamlessly e2e encrypted. By default, emails sent to non-Tutanota users are also e2e encrypted and secured with a password of your choosing. A nice touch is that you can send the notification email in a very wide selection of languages.
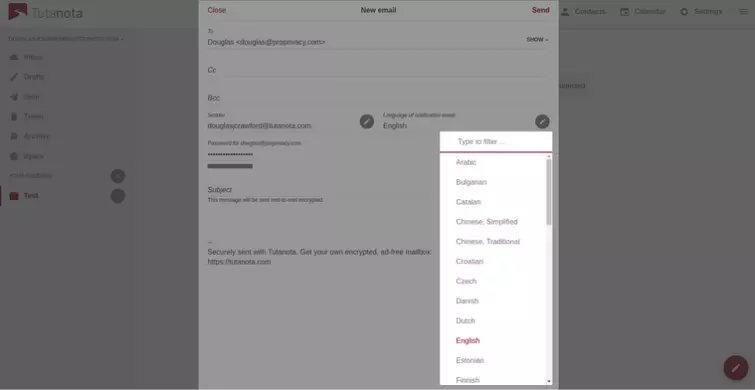
The recipient receives an email containing just a link to the content, which can only be opened with the password you specified. You will, of course, need to communicate this password to the recipient via other channels.
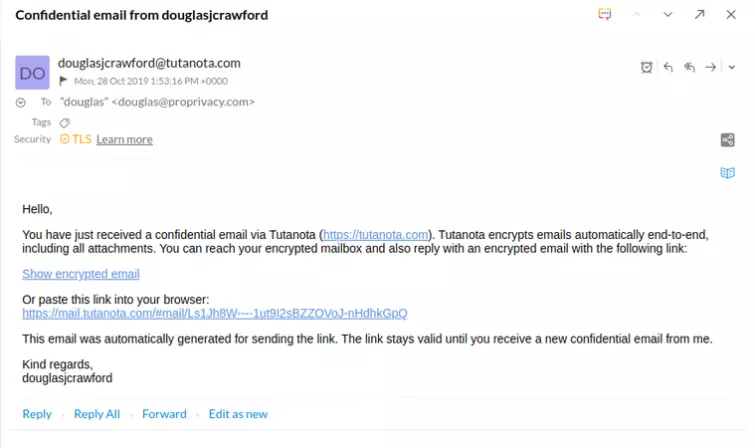
The subject line is hidden, as is all text and attachments. The IP address of the sender is also not shown. Sending an email to a non-Tutanota user creates a new encrypted mailbox for them, which only they can access using the agreed-upon password.
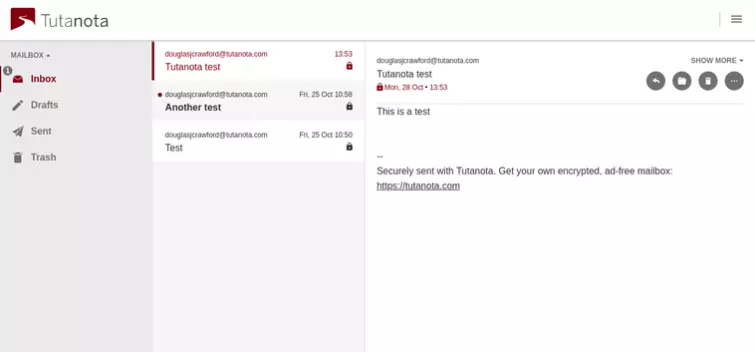
From within their private mailbox, non-Tutanota users can reply to your emails, and these replies will also be securely end-to-end encrypted!
This is an elegant solution for sending e2e encrypted emails to just about anybody. To say that’s much easier than PGP is a serious understatement. Indeed, it's this feature that sets Tutanota apart from every other private and secure email service out there.
Although emails to non-users are sent confidential by default, it is possible to send regular plain text emails as well when required.
The mobile apps
The Android and iOS apps are basically identical, although there is an optimized version available for the iPad. These are really just wrappers for the web console, and so provide the full range of features available through the web interface (including the calendar).
The apps are available from the Google and Android stores, although Android users can also download a Google-free version of the app from F-Droid. Nice.
The desktop apps
The desktop apps for Windows, macOS, and Linux are officially labeled beta. This means there may be some bugs that need ironing out, and they may not be as secure as the web console or mobile apps.
That said, they are straight ports of the web console using Electron, rather than being true native clients. So there shouldn’t really be much that can go wrong.
Final thoughts
Tutanota is a good looking and fully featured email service. It does everything that the likes of Gmail does, without spying on you or targeting you with ads. No email service should be considered as secure as messaging apps such as Signal, but Tutanota is pretty darn secure.
Tutanota's free plan is very usable, although at around a dollar a month there is little excuse not to support Tutanota by upgrading to the Premium plan. Lack of any kind of PGP support may be a sticking point for some, but PGP is hard to use. So hard, in fact, that almost nobody does use it.
Ditching PGP, Tutanota allows you to send secure and private emails in a way that anyone will be able to open and reply to, which is quite an achievement. Unless you absolutely need PGP, then there is little not to like about Tutanota.
We are not entirely convinced that Germany is the best place for such a service to be based, and the ability to pay anonymously with cryptocurrencies can't come soon enough, but overall we are very impressed by the service. We would be happy to recommend it as it stands, but Tutanota isn't resting on its laurels as there is plenty more work to be done.
0 User Reviews
Leave a Review
Thanks for your review!
95 Comments
Write Your Own Comment
Your comment has been sent to the queue. It will appear shortly.

Jon
axlben
pat
Silvia
NewToTutaNota replied to Silvia