In this article on secure privacy email options, we look at various ways to make your email more, well... secure and private. We pay particular attention to the relatively new breed of end-to-end encrypted webmail services, but also survey the pros and cons of more traditional alternatives.
What are the most secure email options?
If you're looking for a short answer, here's a quick overview of the most secure email providers. For more information about the providers we recommend here, and the security of email more broadly, keep on reading.
- StartMail - Offers a 7-day trial, $29.99 annually (10GB storage / unlimited disposable email addresses).
- Mailfence - Comes with a free plan (500 MB / 1 address), or €2.50 per month (5 GB / 10 addresses), €7.50 per month (20 GB / 50 addresses).
- SecureMyEmail - Comes with a 30-day free trial. Free for a single address, or $3.99 per month, $29.99 per year, $99.99 lifetime
- Posteo - €1 per month but offers expandable plans.
- Tutanota - Offers a free plan (1 GB/1 address), or $1.35 per month (1 GB (expandable)/5 addresses).
The best Private Email services
Each email provider we suggest belongs in our curated list because of its focus on privacy and security. Each one is backed with a range of features and assurances not offered in other mainstream services. If you want to choose the right one for you, take a look at what makes each one unique:
StartMail gives users the option to create unlimited disposable email addresses. StartMail is a privacy-focused email service operated by the same people who run the Startpage privacy search engine. Because of its integrated use of PGP, StartMail is fully interoperable with other PGP users. It is also possible to send encrypted emails to non-PGP users, who must know a secret password chosen by you in order to open the email. One of the most notable features of this service is that PGP encryption is performed server-side. In other words, it is not end-to-end. StartMail cites the very real problems with JavaScript-based browser encryption that we discussed in the introduction to this article as the reason for this, but it is undoubtedly a controversial decision. This situation is not helped by the fact that StartMail uses a mix of both open-source and closed-source components. StartMail is based in the Netherlands. Much like Switzerland, this is a country traditionally seen as privacy-friendly but which has recently passed alarming new surveillance laws. One thing we really like with StartMail is the ability to create unlimited disposable email addresses. There are no dedicated mobile apps, but full IMAP and SMTP support means you can use any third-party email app with the service. Mailfence is a Belgian-based provider, an excellent location for privacy. Mailfence is based in Belgium, a country with strong privacy laws and no track record of cooperation with the NSA and GCHQ. ISPs are required to perform extensive blanket data retention, but access to this data is strictly regulated and requires a warrant. Mailfence uses easy “one-click” OpenPGP encryption to secure emails, and emails sent to other Mailfence users are encrypted automatically (and never leave Mailfence’s servers). Emails to non-members can be sent encrypted by PGP, or sent unencrypted, but digitally signed with a PGP key. Alternatively, symmetric-encrypted emails can be sent to non-PGP users using a shared secret to secure them. And because Mailfence uses a standard implementation of OpenPGP with full key management available, the service is interoperable with “regular” PGP users. Mailbox runs its own key server. PGP keys are generated in the browser and stored on Mailfence’s servers using an AES-256 cipher. The browser-based PGP encryption is open-source, but much of the back-end environment is closed-source. Deleted messages are kept for two weeks for backup purposes. More concerning is that Mailfence logs all email metadata, including “IP addresses, message-ID’s, sender and recipient addresses, subjects, browser versions, countries and timestamps.” Other superb features Mailfence provides are secure and exportable calendars and secure document storage. One potential drawback that may turn off some users is that unfortunately, Mailfence does not currently offer any native mobile apps, although messages can be synced to iOS and Android devices using Microsoft Exchange ActiveSync and support for POP and IMAP means you can use third-party apps with the service (paid users only). It also offers a cut-down web interface specially designed for mobile devices. SecureMyEmail offers an email encryption service that works with your existing provider, so no need to change all your login details. They make setting up PGP keys a breeze. SecureMyEmail lets you encrypt emails without needing to change email providers. Unlike other secure email providers like ProtonMail or Tutanota, SecureMyEmail works right alongside your current provider to offer you a new layer of security and privacy without the rigmarole of changing your email address on dozens of different websites. Its encryption is based on PGP, and the process to getting it all set up and working is reassuringly straight-forward, which is a massive benefit for those who aren't IT pros, or who aren't particularly familiar with PGP or other forms of encryption. You can even import your own PGP key if you have one you've been using with other providers and I was impressed with just how straight-forward the entire process was from initial sign-up to being able to send my first encrypted email. SecureMyEmail even allows you to set up a personal secure contacts list. You can verify people's identity verify using their social networks, and even view different metrics such as trust levels and mutual friends. It's similar to what PGP users call "The Web of Trust" and it offers an additional layer of security against scammers, phishers and fraudsters of all stripes, as you can easily verify if a message really is coming from who it claims to be. Price-wise, SecureMyEmail is a competitive offering when put up against other providers in the same space. While not as cheap as, say, Tutanota, you don't need to change your email address to use their service. A subscription costs $3.99 per month or $29.99 per year and there's even a lifetime option for a one-off payment of $99.99, though we're not big fans of lifetime subscriptions here at ProPrivacy as there's no guarantee that the service you tie yourself into now is the service you will always receive. We would recommend just sticking with a monthly or annual payment. Posteo guarantees complete privacy and insulates users from authorities by not storing any personally identifiable information. Also based in Germany, Posteo is a somewhat different beast to Tutanota and ProtonMail. It is a secure email service that encrypts its server connections with TLS (using DANE and perfect forward secrecy), and stores all emails on AES-encrypted hard drives (key size unknown). By default, Posteo is not an e2e encrypted service. End-to-end email encryption is supported, however, via “one-click” OpenPGP and S/MIME support within the browser. Recipients must have the same kind of encryption software installed on their computers (OpenPGP or S/MIME, whichever is used), but need not be Posteo users. Posteo also runs its own PGP key directory, which is more private than conventional PGP key servers. The Roundcube web interface works well inside mobile browsers, but Posteo has no dedicated mobile apps. IMAP support, however, means that third-party email apps can be used with the service. In 2013, this service proved its privacy chops by successfully resisting demands by the police for the identity of a Posteo account holder who was thought to be using the service for illicit purposes. The fact that it does not store any data on its customers' identities made handing over such information impossible. Tutanota offers users excellent security with perfect forward secrecy. Tutanota is similar in many ways to ProtonMail, but the service is based in Germany, which may raise a few eyebrows amongst the most privacy-conscious users. Though Germany has strict privacy laws, the German government also practices widespread surveillance of its own, provides the base for the NSA's extensive European operations, and is known to collaborate with the NSA. But since Tutanota stores all emails e2e encrypted, this shouldn't matter. Tutanota encrypts messages with an AES-128 cipher, RSA-2048 handshake, and perfect forward secrecy, rather than using PGP. This enables it to encrypt email subject lines when sent to other Tutanota users, but it means the system is not interoperable with "regular" PGP users. For more information, check out our detailed review. Mailbox.org provides users with the option to store sent and received emails in a PGP-encrypted Guard mailbox. Like Tutanota, mailbox.org is based in Germany. The German government has strict privacy laws, but also practices widespread surveillance of its own, providing the base for the NSA’s extensive European operations, and is known to collaborate with the NSA. PGP encryption can be performed server-side for convenience, but this is not end-to-end. mailbox.org mitigates this problem by also requiring a password to access encrypted emails, which is known only to the account user. A certain level of trust is still required, however. Alternatively, you can e2e encrypt PGP emails in your browser using the Mailvelope browser add-on, which has been pre-configured to work with mailbox.org without requiring any further configuration steps. All sent and received emails are optionally stored in a PGP-encrypted Guard mailbox. Unencrypted emails are still vulnerable to interception during transit, but should be secure at rest. As with its server-side full PGP encryption of individual emails, Guard mailboxes are further secured by a password that only the user knows. There are no mobile apps, but mailbox.org supports IMAP and POP for use with third-party email apps. Contacts and calendars can be synced to mobile via ActiveSync. ProtonMail provides users all the convenience and functionality of a webmail service, along with all the security and privacy features you require. ProtonMail was the first in a post-Snowden “new-wave” of webmail services that set out to provide all the functionality of Gmail and its ilk, but which respect users’ privacy and provide full end-to-end encryption (e2ee) for emails. Users can send anyone an encrypted email, to which they can also respond securely. Swiss surveillance laws are worrying, however, and despite reassurances from ProtonMail, the service has handed over information to Swiss authorities in relation to criminal investigations. The good news is that ProtonMail introduced full OpenPGP support in 2018. This means users can send PGP encrypted emails to non-ProtonMail contacts, and open PGP encrypted emails sent to their ProtonMail account. Check out our ProtonMail Review for an in-depth look at this service. 1. StartMail
Pricing
Pros
Cons
Pricing
Pros
Cons
Pricing
Pros
Cons
4. Posteo

Pricing
Pros
Cons
5. Tutanota

Pricing
Pros
Cons
6. Mailbox.org

Pros
Cons
Pricing
Pros
Cons
Honorable mentions
Disroot and Runbox are privacy-friendly email services that store emails on encrypted hard drives. They do not, however, offer any form of end-to-end encryption. Kolab Now is also a privacy-friendly email service but does not store emails encrypted.
When we initially published this article several years ago, the recently resurrected Lavabit service looked promising. Most of the promised privacy and security features have yet to materialize, however, and we have difficulty recommending any service based in the US (as evidenced rather dramatically by Lavabit's own initial demise!).
Email is not private or secure
Unfortunately, email wasn't designed with privacy or security in mind. It was only in the later years of its existence that it became clear that consumers didn't want to pay for expensive and complex technologies they were using every day. Because of this, email providers realized that there were other ways to monetize their services – by selling off your information.
Google developed one of the most successful models by leveraging individuals' personal data for marketing – and the more of your data Google collects, the more valuable it is. By creating profiles on users, Google can target advertising through real-time bidding and get maximum profit for minimum cost.
We're sure you've heard at some point how companies such as Google collect and sell your data online (it's one of the many reasons that legislation such as GDPR came into existence). But did you know that Google also collects information about you through your emails? Google scans all emails sent via its Gmail service, even ones sent between other email services and Gmail services. If you think that's invasive, it's because it is.
In 2017 Google somewhat disingenuously announced that it would no longer scan emails in order to target users with tailored ads, but this does not mean it has stopped scanning emails for other purposes. Its much-touted AI-based smart reply feature proves this beyond all doubt, as does its full list of everything you have purchased from any online retailer since 2015!
Government spying
Whatever the situation with Google, it is normal for email services to scan users’ emails for advertising purposes.
And what can be collected for advertising revenue is also incredibly valuable to "collect it all” security agencies such as the NSA.
Google cooperated with the NSA to spy on its users for years and only stopped when caught with its pants down by Edward Snowden’s revelations in 2013. Or at least it claims to have stopped. Yahoo, on the other hand, continued to betray its users to the NSA right up until at least October 2016.
Pay for It!
As the old adage goes, "if you aren’t paying for a product, then you are the product.”
There are some free, secure email services out there, however, they often have data caps and do not include all the features offered by the premium version of the service.
It costs a lot of money and time to run an email service, so you need to consider very carefully how that service is funded. Services such as RiseUp and Autistici are run by politically motivated activists and are designed primarily to provide privacy for similarly minded activists.
Such services are willing to run at a financial loss thanks to the political ideology of their founders. As such, they are small and not very well-funded. Users should certainly consider donating towards them if they can afford to do so.
PGP-encrypted emails can be securely sent over any regular email service, but the simple reality is that very few of your contacts (if any) will also use PGP. This means that you will still require a private email service for day-to-day use...
All Browser-based encryption is insecure
Webmail services are very convenient, as they can be easily accessed from within any web browser. Unfortunately, cryptography in browsers is implemented using JavaScript, and JavaScript cryptography in browsers is inherently insecure.
This is because a compromised server or man-in-the-middle attack can push compromised encryption keys to both you and your recipient’s browsers.
Does this make webmail services useless? No. It all depends on your threat model. For most users, they are probably absolutely fine. But no webmail service is going to be anywhere near as secure as using PGP with a dedicated email client.
If you access an encrypted webmail service via its mobile app or a dedicated email client only (i.e. not through a browser), then this issue does not apply.
Use Signal Instead
I have recently come to the conclusion that e-mail is fundamentally unsecurable. The things we want out of e-mail, and an e-mail system, are not readily compatible with encryption. I advise people who want communications security to not use e-mail, but instead use an encrypted message client like OTR or Signal.
Encrypted messaging apps are much easier to use than PGP (what isn’t?!), and are much more secure than any kind of email. Signal messenger is widely regarded as the most secure way to communicate with another person yet devised, short of actually whispering something into their ear.
Signal is, therefore, the best solution currently available for keeping the actual contents of messages secure. OTR is also a good option for desktop users.
End-to-end (e2e) privacy Email services
Why use a privacy-focused email service?
If you need a conversation to be as private as possible, then it's always a good idea to use Signal instead of email. However, the simple fact of the matter is that email is not going away, and it remains the single most popular means of communication on the planet. Using a private and secure email service of the kind described below means:
- The service will not scan your emails (for advertising or any other purpose).
- The service will use end-to-end encryption (e2ee). You encrypt and decrypt your emails on your own device so that neither your email provider nor the NSA can access them.
- You won't be bombarded with ads.
Pretty Good Privacy (PGP)
PGP was developed as a protocol for securely encrypting emails, and although the original standard is no longer open source (it is now the property of Symantec), the Free Software Foundation has taken up the open-source banner in the form of the 100 percent interoperable OpenPGP standard.
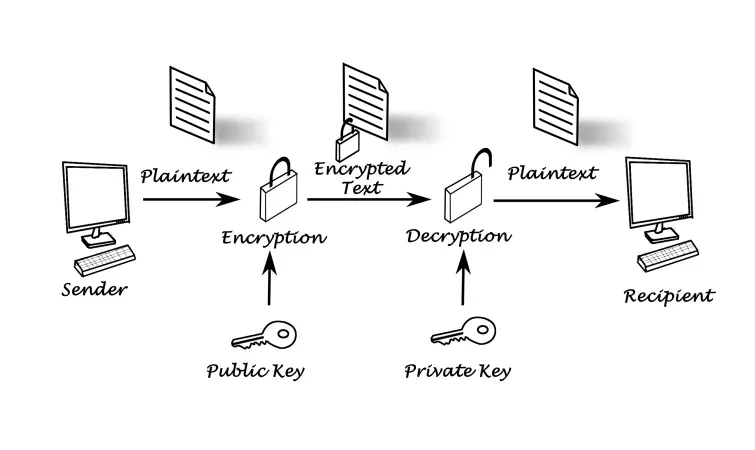
The most traditional (and still the most secure) way to use PGP is GNU Privacy Guard (also known as GnuPG or just GPG). This is available for Windows, macOS, and Linux, with a standalone email client such as Claw-Mail or Thunderbird.
Although the basic program uses a simple command-line interface, more sophisticated versions are available for Windows (Gpg4win) and Mac (GPGTools). We have a guide to securing your email with our Gpg4win guide elsewhere. It may well be worth reading through it to help understand how OpenPGP works.
Note that with PGP, the metadata – email addresses of sender and recipient, date and time of sending, and e-mail’s subject line- are not encrypted. Just the body and any attachments. And any service that wishes to be compatible with PGP will necessarily suffer the same limitations.
Another problem with PGP is that it does not use Perfect Forward Secrecy (PFS). So once keys for one encrypted email are broken, all other emails encrypted using the same keys will also be compromised. This is an area where e2e PGP email web services shine because the use of Diffie-Hellman or ECDE key exchanges in their TLS connections introduces PFS.
We should note that this is a problem that affects all implementations of PGP, including the email providers listed in this article.
Mailvelope – making PGP easier
Even a casual glance through our Gpg4win guide will amply demonstrate why PGP has not caught on with the public. It is complex to the point of being confusing and is hard to get right. Most of the e2e webmail services listed above use PGP, but aim to make it as user-friendly and "idiot-proof” as possible.
In this, they are largely successful, but at a price in security. As already discussed, browser-based cryptography is deeply flawed. A third option exists, however, that provides something of a "middle way”.
Mailvelope is an OpenPGP browser plugin that is much easier to use than the more traditional setup (although not as easy as "one-click” webmail solutions).
Self-hosted email
A more extreme option to all the above is to self-host your own email server. You can do this either on your own PC or on a rented server. Self-hosting your own email server pretty much guarantees that Google and other big corporations will not be snooping on your emails (at least directly – they will still be able to read unencrypted emails sent to other users of their services).
Taking this route, however, is a non-trivial job for even some of the most technically inclined among us. And ensuring that it is secure is even more difficult. In fact, if not done right, running your own email server can be actively dangerous, as it can provide a false sense of security, so only consider it if you really know what you're doing.
This is not to say it is impossible, and there are certainly privacy fanatics out there who swear by self-hosting their email. This is a subject we may indeed write a guide for at some point in the future!
Software such as Mail-in-a Box and Mailcow make the job easier by automating the process, but for maximum security, you should build your own server from scratch (so to speak). Great tutorials on how to do this can be found here and here.
Conclusion
Unfortunately, email isn't as safe as we would like it to be. If you're not wanting to move away from email altogether, then it's time you invested in a secure email provider. Here's a quick reminder of the most secure email clients:
- StartMail - Offers a 7-day trial, $29.99 annually (10GB storage / unlimited disposable email addresses).
- Mailfence - Comes with a free plan (500 MB / 1 address), or €2.50 per month (5 GB / 10 addresses), €7.50 per month (20 GB / 50 addresses).
- SecureMyEmail - Comes with a 30-day free trial. Free for a single address, or $3.99 per month, $29.99 per year, $99.99 lifetime
- Posteo - €1 per month but offers expandable plans.
- Tutanota - Offers a free plan (1 GB/1 address), or $1.35 per month (1 GB (expandable)/5 addresses).




