Although in many ways very different, both VPN and the Tor anonymity network use encrypted proxy connections in order to hide users’ identities they can be used together. Using a VPN and Tor together can provide an extra layer of security and mitigate some drawbacks of using either technology exclusively. In this guide, we show you how to use both Tor and a VPN together.
If you are new to Tor browser or maybe you want more information about it, then take a look at the guides listed below:
- What VPN to use? - if you don't already have a VPN service and you aren't sure where to start, check out our Tor VPN article for a list of recommendations and some helpful tips on using them together.
- What is better? - if you are looking to see what software is better and the pros and cons of using each service, then check out our Tor vs VPN guide for more information about this.
- Everything about Tor Browser - if you want details on how Tor works, how to install it, how to use it (without a VPN), and more, take a look at our ultimate Tor browser guide.
Tor through VPN
In this configuration you connect first to your VPN server, and then to the Tor network before accessing the internet:
Your computer -> VPN -> Tor -> internet
Although some of the providers recommended in our best VPNs for Tor article offer to make such a setup easy, this is also what happens when you use the Tor Browser or Whonix (for maximum security) while connected to a VPN server, and means that your apparent IP on the internet is that of the Tor exit node.
Pros:
- Your ISP will not know that you are using Tor (although it can know that you are using a VPN).
- The Tor entry node will not see your true IP address, but the IP address of the VPN server. If you use a good no-logs VPN this can provide a meaningful additional layer of security.
- Allows access to Tor hidden services (.onion websites).
Cons:
- Your VPN provider knows your real IP address
- No protection from malicious Tor exit nodes. (Non-HTTPS traffic entering and leaving Tor exit nodes is unencrypted and could be monitored.)
- Tor exit nodes are often blocked
- We should note that using a Tor bridge such as Obfsproxy can also be effective at hiding Tor use from your ISP (although a determined ISP could in theory use deep packet inspection to detect Tor traffic).
Important note: Some VPN services (such as NordVPN, Privatoria and TorVPN) offer Tor through VPN via an OpenVPN configuration file (which transparently routes your data from OpenVPN to the Tor network). This means that your entire internet connection benefits from Tor through VPN.
Please be aware, however, that this is nowhere near as secure as using the Tor browser, where Tor encryption is performed end-to-end from your desktop to the Tor servers. It is possible that with transparent proxies your VPN provider could intercept traffic before it is encrypted by the Tor servers. The Tor Browser has also been hardened against various threats in a way that your usual browser almost certainly has not been.
For maximum security when using Tor through VPN you should always use the Tor browser
VPN through Tor
This involves connecting first to Tor, and then through a VPN server to the internet:
Your computer -> encrypt with VPN -> Tor -> VPN -> internet
This setup requires your VPN client to be configured to work with Tor, and the only VPN service that we currently recommend for doing this is the Swedish provider PrivateVPN.
The great thing about using PrivateVPN's VPN through Tor feature is that the VPN provider is unable to detect your home IP address when you connect to its servers.
As a result, it becomes impossible for the VPN to track who you are and what you are doing in real-time.
This is a useful additional layer of protection against the potential for the VPN to be served a warrant that forces it to begin monitoring traffic. (PrivateVPN is already a no logs service, so it would have no existing connection records or usage logs to hand over to the authorities if it was approached.)
Admittedly, this is an additional privacy measure that most users probably do not require. However, depending on your personal threat model, it is a useful addition if you want high levels of privacy and anonymity online.
Another benefit of using VPN through Tor (Tor over VPN) is that your apparent IP on the internet is that of the VPN server. This allows you to prevent websites and online services from detecting a Tor exit node (which stops them from blocking you). And allows you to pick the country that you get your outbound IP address in; depending on your needs (to access geo-restricted services, for example).
Pros
- Because you connect to the VPN server through Tor, the VPN provider cannot ‘see’ your real IP address – only that of the Tor exit node. When combined with an anonymous payment method (such as properly mixed Bitcoins) made anonymously over Tor, this means the VPN provider has no way of identifying you, even if it did keep logs.
- Protection from malicious Tor exit nodes, as data is encrypted by the VPN client before entering (and exiting) the Tor network (although the data is encrypted, your ISP will be able to see that it is heading towards a Tor node).
- Bypasses any blocks on Tor exit nodes.
- Allows you to choose server location (great for geo-spoofing).
- All internet traffic is routed through Tor (even by programs that do not usually support it).
Cons
- Your VPN provider can see your internet traffic (but has no way to connect it to you)
- Slightly more vulnerable to global end-to-end timing attack as a fixed point in the chain exists (the VPN provider).
This configuration is usually regarded as more secure since it allows you to maintain complete (and true) anonymity.
Remember that to maintain anonymity it is vital to always connect to the VPN through Tor (if using AirVPN or BolehVPN this is performed automatically once the client has been correctly configured). The same holds true when making payments or logging into a web-based user account.
Malicious Exit Nodes
When using Tor, the last exit node in the chain between your computer and open internet is called an exit node. Traffic to or from the open internet (Bob in the diagram below) exits and enters this node unencrypted. Unless some additional form of encryption is used (such as HTTPS), this means that anyone running the exit node can spy on users’ internet traffic.
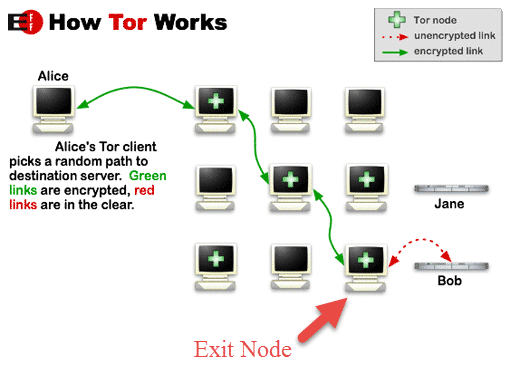
This is not usually a huge problem, as a user’s identity is hidden by the 2 or more additional nodes that traffic passes through on its way to and from the exit node. If the unencrypted traffic contains personally identifiable information, however, this can be seen by the entity running the exit node.
Such nodes are referred to as malicious exit nodes, and have also been known to redirect users to fake websites.
SSL connections are encrypted, so if you connect to an SSL secured website (https://) your data will be secure, even it passes through a malicious exit node.
End-to-end Timing Attacks
This is a technique used to de-anonymize VPN and Tor users by correlating the time they were connected to the timing of otherwise anonymous behavior on the internet.
An incident where a Harvard bomb-threat idiot got caught while using Tor is a great example of this form of de-anonymization attack in action, but it is worth noting that the culprit was only caught because he connected to Tor through the Harvard campus Wi-Fi network.
On a global scale, pulling off a successful e2e attack against a Tor user would be a monumental undertaking, but possibly not impossible for the likes of the NSA, who are suspected of running a high percentage of all the world public Tor exit nodes.
If such an attack (or other de-anonymization tactic) is made against you while using Tor, then using VPN as well will provide an additional layer of security.
So which is better?
VPN through Tor is usually considered more secure because (if the correct precautions are taken) it allows true anonymity - not even your VPN provider knows who you are. It also provides protection against malicious Tor exit nodes, and allows you to evade censorship via blocks on Tor exit nodes.
You should be aware, however, that if an adversary can compromise your VPN provider, then it controls one end of the Tor chain. Over time, this may allow the adversary to pull off an end-to-end timing or other de-anonymization attack. Any such attack would be very hard to perform, and if the provider keeps logs it cannot be performed retrospectively, but this is a point the Edward Snowden’s of the world should consider.
Tor through VPN means that your VPN provider knows who you are, although as with VPN through Tor, using a trustworthy provider who keeps no logs will provide a great deal of retrospective protection.
Tor through VPN provides no protection against malicious exit nodes and is still subject to censorship measures that target Tor users, but does mean that your VPN provider cannot see your internet traffic content…
