Does CyberGhost unblock Netflix?
| Netflix | |
| iPlayer | |
| Amazon Prime | |
| Hulu | |
| Disney+ |
This is often the biggest deciding factor when deciding on a VPN provider. The good news is that CyberGhost is able to unblock multiple Netflix libraries, including the US, UK, Germany, and Japan.
In addition, you'll be able to connect to specially optimized streaming servers that unblock over 35 popular services. These include Fox Sports in Brazil, Comedy Central, YouTube in various countries, Netflix in various countries, hulu, and many more.
It even unblocks Disney+ from anywhere in the world. Plus, it has servers that are optimized for unblocking BBC iPlayer for those who want to stream British TV!
Pricing
As with many other providers, CyberGhost offers a hefty price reduction for those willing to sign up for a long-term subscription, making it a cheap VPN for anyone looking for a lengthy commitment. Otherwise, the plans are identical in terms of the features they offer.
A very generous 45-day VPN money-back guarantee is available when you subscribe for 6 or 18 months. As a result, you'll be able to make a risk-free purchase and try the service out in your own time – which is a great way to ensure that CyberGhost is the right pick for you.
24 months + 3 months FREE
$50.64 billed for the first 2 years6 months
$41.94 billed every 6 months1 month
A 24-hour free trial is also available if you want to try the VPN, which is great. Admittedly, that free trial can seem a little elusive – sometimes it's advertised, sometimes it's not. However, a quick Google search should point you in the right direction.
Clicking on the free trial for macOS can also lead to a Windows .exe file being downloaded, requiring you to search through the CyberGhost VPN help pages to find the correct .pkg download for macOS.
If you already have an account, you can sign-up via the Android or iOS apps, Or, once you've tracked down the Windows or macOS free trial download, the rest of the process is simple.
Payments
CyberGhost VPN accepts payment through credit/debit card, PayPal, or direct debit. Additional payment options may be available depending on your country of residence.
Those looking for privacy can also pay for this VPN in Bitcoin, although remember that no matter how anonymously you pay, a VPN company will still know your real IP address.
Payments are processed by third party services such as Cleverbridge, Stripe, and PayPal, while Bitcoin payments are processed by BitPay.
Features
| Simultaneous connections | 7 |
| Total servers | 11625 |
| Routers supported | |
| Split-tunneling | |
| Server locations | 126 |
| Number of countries | 100 |
CyberGhost is a well-rounded provider – so let's take a look at exactly what you're getting in your subscription.
With up to seven simultaneous connections on offer, you'll be able to keep all of your devices secure at home or on the go.
Torrenters will rejoice, too, as CyberGhost has a number of dedicated P2P servers. These servers have been specifically optimized for torrenting, and the provider's unlimited bandwidth will make downloading files a breeze.
Even if you're not interested in torrenting, CyberGhost has a broad network of bare metal, and virtual servers – and users can take their pick from thousands of different servers spread over 100 countries .
For the more security conscious, the option exists to use CyberGhost's NoSpy servers. Rather than being based inside a data center owned by a third party, the NoSpy data center is based in Romania, putting it outside the reach of the 5 Eyes Alliance's jurisdiction, and only CyberGhost personnel have access to these servers.
These servers also boast extended bandwidth for resource-intensive tasks and super high premium hardware in addition to a dedicated uplink. Claims of 100% anonymity should be viewed with some skepticism, though.
If you'd like to install CyberGhost on your router rather than on individual devices, then you absolutely can, and you'll be able to protect an unlimited number of devices by doing so – so long as they're connected to the same router. There are configuration guides on the CyberGhost site to help you get this set up or you can just purchase one of a range of pre-installed routers with a built-in kill-switch if you'd rather avoid the hassle.
When it comes to customer service, CyberGhost's support team is available 24/7 via live chat or email. There are also a number of how-to guides on the provider website which cover common issues, from set up on iOS and Android to troubleshooting problems when connecting to various streaming platforms.
Secure Dedicated IP addresses
For those who need a dedicated IP address, CyberGhost can provide access at a small extra cost. Dedicated (static) IPs can be added to subscriptions in the US, Germany, France, UK, or Canada.
CyberGhost is also the first VPN to implement an automated token system that allocates that static IP address without revealing it to CyberGhost devs.
This unique system prevents CyberGhost from knowing which actual IP address is tied to which dedicated static IP, which massively increases privacy for end users. We are impressed that CyberGhost has managed to remove any ties between a user's CyberGhost VPN account and their Dedicated IP.
WireGuard
The WireGuard protocol is now available to users following the launch of the CyberGhost 8 app. This is great news for users who want access to the latest and greatest in VPN encryption protocols.
WireGuard is a new, lightweight protocol that uses highly secure, modern cryptographic principles, and best of all, it's incredibly fast. This makes it well worth trying if you want to do data-intensive tasks like streaming in HD with your VPN.
Bare metal servers
Also impressive is CyberGhost's network of bare-metal, single occupancy servers that are firmly under the control of CyberGhost's staff rather than being shared with other clients or operating in a virtual machine.
Connection Features
The CyberGhost VPN clients offer a number of special "Connection features". Block ads, Block Malicious Websites, and Block Online Traffic using DNS blocklists to protect your device from online threats.
This allows you to surf the web without fear of running into websites that will try to track you or attempt to infect you with malware.
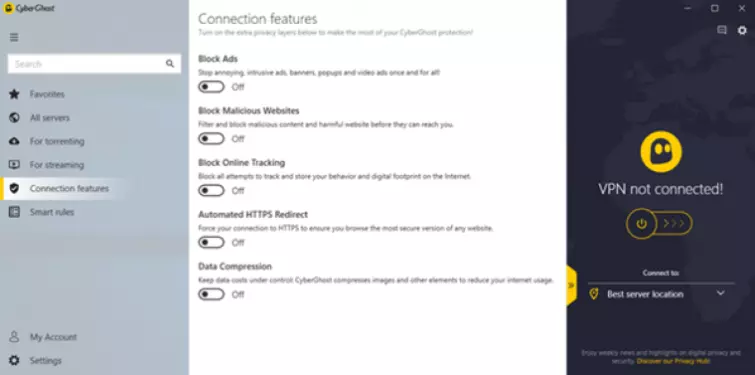
Automated HTTPS is CyberGhost 8's implementation of the open-source HTTPS Everywhere browser extension, which ensures a secure HTTPS connection is automatically established if the domain supports it. This prevents you from connecting using the unsecured HTTP by accident.
Data compression reduces your bandwidth usage and can therefore be useful (depending on what you download), but it should be noted that many VPN services enable data compression by default without feeling the need to mention it.
"Smart rules"
"Smart rules" cover a number of features that are available in some of CyberGhost VPN apps, but not others.
- Wi-Fi protection (Windows, macOS, Android, iOS) – detects when you connect to an unknown network and can automatically turn on your VPN, ask what to do, or never protect, as you specify.
- Exceptions (Windows, Android, iOS) – also known as split-tunneling, this feature allows you to exclude some websites from the VPN. This is very useful, for example, if you usually connect to a VPN server overseas but wish to connect to local versions of some websites without disconnecting the VPN.
- App protection (Windows, Android) – auto-launches CyberGhost and automatically connects to a specified server whenever you open named apps. So, if you want to use this VPN for Netflix you could set this up to auto-connect to the US Netflix server every time you open the Netflix app.
Does CyberGhost VPN allow torrenting?
Torrenting is another popular use case for VPNs. Anyone familiar with the BitTorrent protocol will know that it exposes your IP address when torrenting files to anyone else who is also downloading the same file, which is a definite privacy risk.
A fast VPN protects your privacy and lets you download without having to wait around. However, many VPNs don't allow torrenting traffic on their network, which is why you must check before subscribing!
Luckily, CyberGhost has several servers specifically optimized for torrenting so you can use this service to gain total privacy while you download. We tested these servers using uTorrent to download a few files, and CyberGhost worked flawlessly with no IP leaks to compromise your security.
Speed & Performance: How fast is CyberGhost VPN?
| CyberGhost VPN | ExpressVPN | NordVPN | |
|---|---|---|---|
| ProPrivacy.com SpeedTest (average) | 63.92 | 100 | 85.9 |
| Speed | 556.2 | 100 | 568.0 |
| Performance | 7 | 10 | 9 |
| Reliability | 7 | 9 | 8 |
An average download speed of around 52 Mbits/s put CyberGhost VPN in the bottom half of some of the fastest VPNs in the world, which is still impressive. Less than a Mbit/s or two separate most of the top providers, which makes them all pretty similar in everyday use.
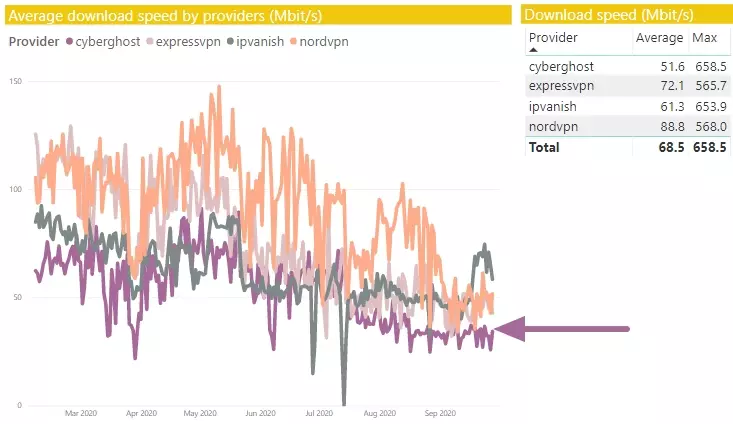
Again, it's not at the top of our list, but CyberGhost VPN's max burst speed result of 658.5 Mbit/s proves that its servers have great capacity, and show that the service competes with the very best VPNs on the market. This means you should have no issues torrenting or streaming in HD with this VPN.
As mentioned earlier, CyberGhost now includes WireGuard connections. This is a modern VPN protocol that is designed to provide super-fast speeds. So, if you need that extra bit of speed for torrenting or streaming, it is definitely worth giving it a go.
IP, DNS, and WebRTC leak tests
| ProPrivacy.com SpeedTest (average) | 63.92 |
| Speed | 556.2 |
| Performance | 7 |
| Reliability | 7 |
To ensure that a VPN is working as advertised, it is important to perform leak tests. If a VPN has IP leaks, DNS leaks, or WebRTC leaks, this will mean that it simply can not adequately protect your privacy online.
We have tested CyberGhost in-house, using our own leak test tool (which you can use to test any VPN provider for leaks on your own system if you wish).
In our tests, we encountered no leak problems with either the Windows or macOS clients. However, we were only able to test CyberGhost 8 on an IPv4 connection from home due to lockdown.
Thus, if you do have an IPV6 connection, you should test yourself (or simply go ahead and revert back to IPV4 manually on your computer).
It is worth noting that CyberGhost's command-line only Linux app provides no DNS or WebRTC leak protection, so you may want to check this for leaks on your own system if you're running Linux.
Please see our Complete guide to IP leak protection for further information on leaks and leak testing.
Privacy & Security
| Kill-switch | |
| Obfuscation (stealth) | |
| IPv6 leak protection | |
| WebRTC leak protection | |
| Bare-metal servers? | |
| Self-hosted DNS |
Jurisdiction
CyberGhost is a Romanian VPN company that is owned by KAPE Technologies.
Romania is generally considered to be privacy-friendly. Romanian courts struck down the EU Data Retention Directive on constitutional grounds long before it was declared illegal by the European Court of Justice.
It is also not a 14-Eyes spying alliance nation and has no known ties to the NSA. This generally makes Romania a great place for a VPN to be based.
It is worth noting that according to its TOS, "the relationship between you and KAPE shall be governed by and construed in accordance with the laws of England."
That said, CyberGhost takes pains to point out that they are a separate entity to KAPE and that it is a Romanian company, operating under Romanian jurisdiction. The company even publishes a transparency report that proves it does not have to comply with any UK warrants.
Overall this earns CyberGhost a thumbs up with us.
Logs
"When using CyberGhost VPN, the user's traffic data such as browsing history, traffic destination, data content, and search preferences are not monitored, recorded, logged or stored by the Company. More than this, when using the CyberGhost VPN, we are not storing connection logs, meaning that we don't have any logs tied to your IP address, connection timestamp or session duration."
So CyberGhost VPN easily qualifies as no logs VPN, although some aggregate metadata is sent anonymously to third-party services (MixPanel) for trend analysis.
A more concerning finding is that CyberGhost VPN performs a considerable amount of web tracking on visits to its site, which it shares with a number of third parties (although I didn't spot any Google Analytics trackers). This kind of tracking has no effect on the privacy of VPN sessions, though use of an ad/web tracker blocker is probably not a bad idea for increased privacy.
Technical security
The Windows app provides OpenVPN, IKEv2, or WireGuard encryption. The Android app also provides those protocols. macOS and iOS apps use IKEv2 by default with WireGuard also available.
CyberGhost uses the following OpenVPN settings:
Data channel: an AES-256-CBC cipher with SHA-256 hash authentication.
Control channel: an AES-256 cipher, RSA-4096 key encryption, and SHA384 hash authentication. Perfect forward secrecy is provided by an ECDH-4096 key exchange.
This is a very strong setup. And as already mentioned, CyberGhost VPN uses 100% bare metal servers, which is great news for privacy.
Ease of Use
Signing up for an account on the CyberGhost website is a straightforward process. The apps can be downloaded even if you are not a member, which makes getting hold of them faff-free.
CyberGhost VPN has custom apps for Windows, macOS, Android, and Android TV/ Amazon Fire TV. It also offers a command-line (CLI) app for Linux and free browser extensions for Chrome and Firefox.
To help users out, it provides manual setup guides for a range of other devices such as DD-WRT and Tomato routers, Raspberry Pi, and Chromebook. this makes CyberGhost a great VPN for all users, no matter which device they happen to own.
And, because CyberGhost lets users install and use the VPN on up to 7 devices at the same time, you can take advantage of all those apps with a single subscription.
The Windows client
CyberGhost VPN has definitely upped the game with its CG8 client in terms of aesthetics. It looks good and is easy to navigate. You can let the app choose a nearby server for you, or you can choose your preferred location from the list.
As always with CyberGhost advanced VPN apps, you can select a country or individual server within a country based on distance and load. You can also select servers that have been optimized for torrenting and streaming various online VoD services.
The Windows VPN app features all of Cyberghost's advanced "Connection feature" and Smart rule" on offer. By default, the CyberGhost uses the OpenVPN protocol, but you can choose from IKEv2 or L2TP/IPsec, too. WireGuard is now also available.
OpenVPN users can switch from UDP to TCP, which is useful for evading moderate VPN blocks. The client offers a random port scanning feature to OpenVPN users, which can be used to evade more casual VPN blocks.
IPv4 DNS leak protection and a kill-switch are enabled by default, though IPv6 connections are not blocked – the reasons for this are unclear. As already noted, IPv6 should be disabled in Settings to prevent IPv6 leaks in Windows.
We ran tests on CyberGhost's kill-switch and discovered that it works at the system firewall level. This is good, meaning that even if the VPN client and OpenVPN daemon crash, your IP address will not be exposed.
We also like the addition of gaming-specific servers that people who need fast speeds will welcome!
The macOS client
The macOS client is very similar to the Windows one. A system-level kill-switch and effective IPv4 and IPv6 DNS leak protection are sensibly baked-in, rather than being a user-configurable option.
Unlike its Windows counterpart, that Mac VPN app uses IKEv2. However, this is a higly robust encryption protocol that is fine for privacy and security.
All "connection features" are present in the app, and they all work excellently – though the only "smart rule" available is Wi-Fi protection. Overall a superb app.
The Android app
The Android VPN app provides the choice of OpenVPN encryption, IKEv2, and WireGuard. Similar to its Windows sibling, it supports TCP and random port selection. It also supports all the "Connection features," plus the Wi-Fi Protection and Exceptions "Smart rules." This makes it a super, advanced VPn client.
It also has an automatic killswitch, and DNS blocking that prevents you from accessing websites that contain malware or tracking.
Overall, we found the Android app to be a pleasure to use. It is fast, and effective for gaining privacy online both at home and on public Wi-Fi. And we enjoy using it for unblocking content, including Netflix US.
The iOS app
Unsurprisingly, the iOS VPN app looks very similar to the Android app.
Under the hood, it opts for the IKEv2 protocol rather than OpenVPN. This is pretty normal for an iOS VPN app, and it is great in terms of security because IKEv2 is widely considered excellent encryption that even has performance advantages over OpenVPN in terms of speeds.
As with the Android app, WireGuard connections are now also available, for those who want the best speeds possible.
Admittedly the "Connection features" and "Smart rules" are not present in the iOS app. However, Wi-Fi Protection and a built-in kill-switch are which is great news and makes this a reliable iOS VPN app.
Linux
CyberGhost's Command-line Linux VPN client is little more than the open-source OpenVPN client pre-configured to use CyberGhost's servers. This does, however, provide some convenience over downloading and running the .ovpn files manually.
The client is available for Ubuntu and Fedora, and appears to be optimized for different versions of those distros. The DEB and RPM packages should work on any systems that support those distribution formats, though.
Browser add-ons
The VPNs browser extensions for Firefox and Chrome are available for anyone to download free of charge, and having a CyberGhost account does not improve their functionality. There are only four proxy server locations available: Germany, Netherlands, Romania, and the United States.
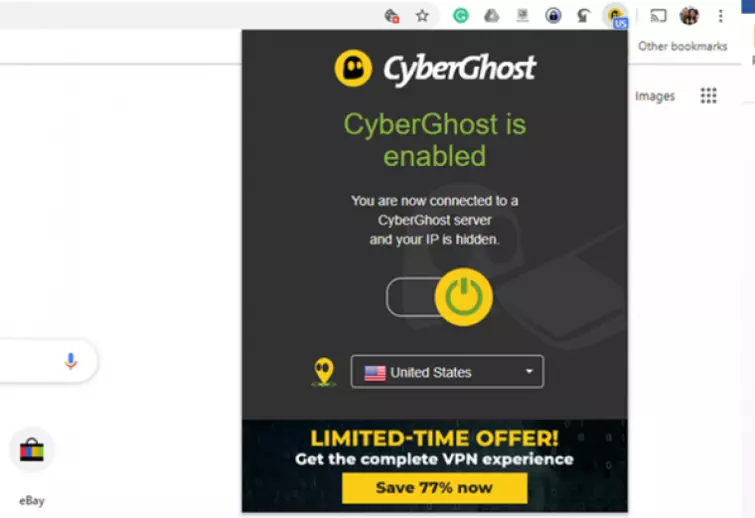
They are simple HTTPS proxies. As such, they will spoof your location and protect your data with HTTPS encryption at the click of a button. They do not provide any WebRTC protection, however.
Customer Service
| Money-back guarantee | |
| 24-hour support | |
| Live chat | |
| Money-back guarantee length | 45 |
| Free trial |
The CyberGhost site hosts extensive setup guides that cover a variety of topics – from setting up the client, troubleshooting streaming issues, and help with protocol usage.
An FAQ is also available, as well as a dedicated Troubleshooting page, and CyberGhost even has its own blog that reports on the latest news from the privacy sphere.
For more direct assistance, email and 24/7 live chat are available in English, German, French, and Romanian, and the team responded quickly, fielding all questions I asked of it.
Final Thoughts
CyberGhost VPN is a fully featured, no-logs VPN provider, and I think that beginners and VPN veterans alike will be able to use the service with few issues. Whilst it's not the fastest VPN out there in terms of average download speed, it is in the top half of the VPN market, meaning you will be able to stream comfortably and play online games with friends without suffering from lag.
The CyberGhost 8 software is elegant on all platforms, and it is a highly secure VPN that unblocks just about everything (including a wide variety of streaming platforms). What's more, you'll benefit from a whole host of useful bells and whistles depending on the platform you're using it on.
The only important feature I'd like to see in the future is more robust obfuscation technology capable of defeating VPN blocks in places such as China, Egypt, and Iran.
But for the vast majority of users who don't need this, CyberGhost VPN is a highly professional service that provides everything you could wish for at a staggeringly low price point!
28 User Reviews
Anon
Serge Robillard
Leave a Review
Thanks for your review!
59 Comments
Write Your Own Comment
Your comment has been sent to the queue. It will appear shortly.

Mueding