This is Part 2 of our look at VeraCrypt
If you haven't done so already, be sure to check out Part 1: VeraCyrpt & how-to basics
One of the best features of VeraCrypt is that it allows you plausible deniability. It does this by hiding an encrypted volume inside another VeraCrypt volume in such a way that it is impossible to prove the second hidden volume exists (if the correct precautions are taken).
The key to this is that VeraCrypt fills up any empty volume space with random data, and it is impossible to distinguish this random data from a second volume hidden inside a ‘normal’ volume.
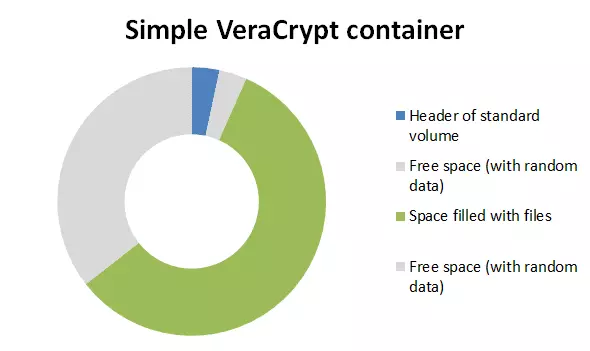
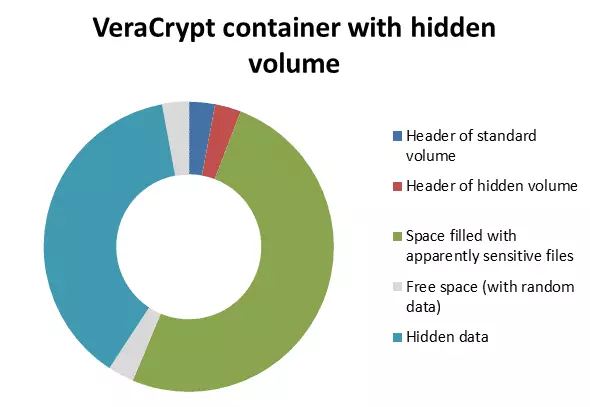
Even when the outer volume is mounted, it should be impossible to prove that another volume is hidden in the apparently random-data filled ‘free space’. Of course, because this feature of VeraCrypt is known to data security specialists, it may be suspected that data is hidden, but there is no way to prove it (and thus coerce you into divulging the password for it).
Please note that this is a beginner's guide designed to help get you started using VeraCrypt hidden volumes. If you need to hide highly sensitive data then please carefully consult the official documentation starting here (and take the time to fully understand the implications this information). Please also note our section on the dangers of VeraCrypt’s hidden volumes feature towards the end of this article.
Creating a VeraCrypt hidden volume
- From the VeraCrypt main screen click ‘Create Volume’.
![VCH3]()
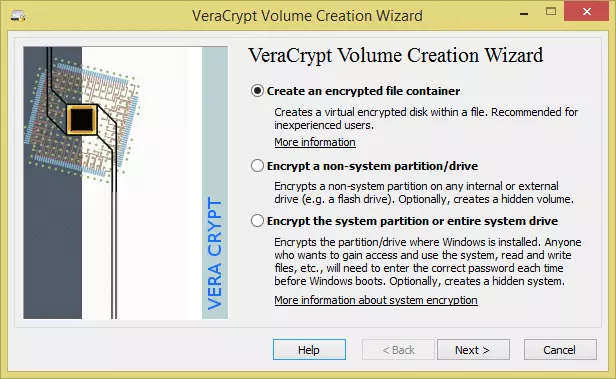
- Make sure the ‘Create an encrypted file container’ radio button is selected, and click ‘Next’.
![VCH4]()
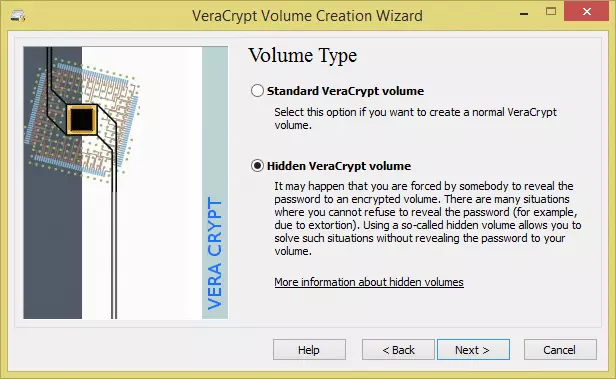
- Select ‘Hidden VeraCrypt volume’ and click next.
![VCH5]()
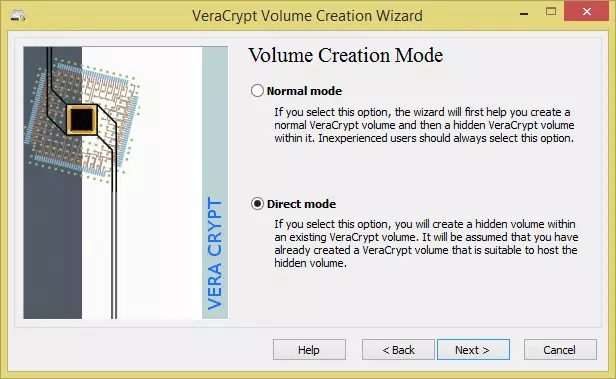
- In the Volume Creation screen you can chose ‘Normal mode’ to make a new normal volume and then create a hidden encrypted volume within it, or ‘Direct mode’ to create a hidden volume inside an already created normal volume. In our article VeraCrypt & how-to basics we looked at how to create a normal VeraCrypt volume, so for the sake of brevity we’ll opt for ‘Direct mode’ here.
![VCH6]()
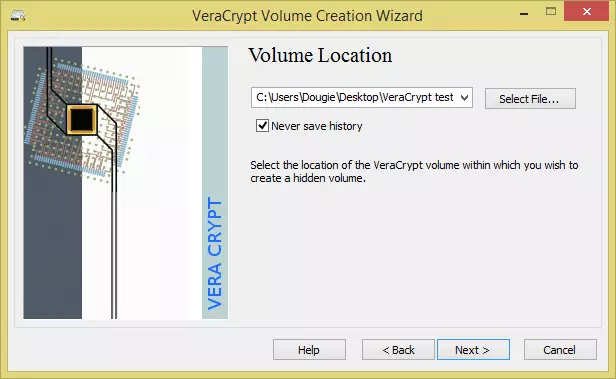
- Click ‘Select File…’ and navigate to a VeraCrypt container you have created, ‘Open’ it and click ‘Next’. If you chose ‘Normal mode’ at the volume creation screen, you will instead be taken through steps 4 – 8 in the ‘Creating a container’ section of VeraCrypt & how-to basics.
![VCH7]()
- Enter the (outer) volume’s password.
![VCH8]()
- Click ‘Next’ again…
![VCH9]()
- Choose how you would like the hidden volume encrypted.
![VCH10]() We will go with the same settings we chose for creating the outer volume (and for the same reasons)
We will go with the same settings we chose for creating the outer volume (and for the same reasons) - 9. Select the hidden volume size. Again, this is just like when you created the outer volume. Then click ‘Next’.
![VCH11]() Our outer volume was 50MB, so we think 20MB is good size to hide our secret files in
Our outer volume was 50MB, so we think 20MB is good size to hide our secret files in - Choose a password for the hidden volume. It is extremely important to choose one that is not only highly secure, but also very different from the one you chose for the outer volume. Click ‘Next’.
![VCH12]()
-
Again, moving your mouse randomly around the window for at least 30 seconds will greatly improve the cryptographic strength of the encryption keys. Click ‘Format’…
![VCH13]() …and the hidden volume is created! Hit ‘OK’.
…and the hidden volume is created! Hit ‘OK’.![VCH14]()
Protect the data on your hidden volume
When you mount the outer volume (using the outer volume password - see VeraCrypt & how-to basics) you can read data stored on it as per normal and without risk. However, if you write (i.e. save) data onto this outer volume then you may damage data stored on the hidden volume. This can be prevented by taking the following steps.
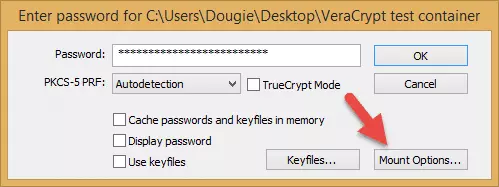
- Mount the outer volume by entering its password, then click ‘Mount Options’.
![VCH15]()
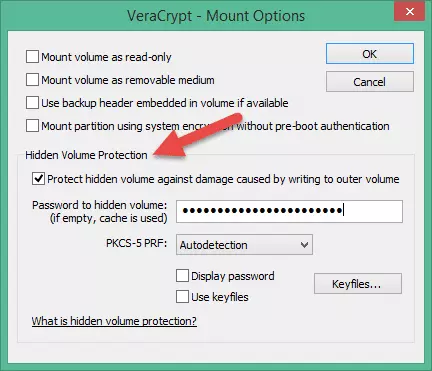
- Check ‘Protect hidden volume against damage caused by writing to outer volume’, enter your password for the hidden volume and click ‘OK’.
![VCH16]() Both passwords must be correct for this setting to work.
Both passwords must be correct for this setting to work.
Note that this procedure does not mean the hidden volume is mounted, only that its header, containing the size of the hidden volume, is decrypted. Any attempt to save data to the hidden volume is then rejected, and the entire volume (both outer volume and hidden volume) becomes write-protected until remounted. In order to maintain ‘plausible deniability’, VeraCrypt will return an ‘invalid parameter’ system error if this happens. - Back at the password screen (see step 1 above) hit ‘OK’. If VeraCrypt is still running and passwords for both volumes are stored in RAM, then you will receive a warning…
![VCH17]()
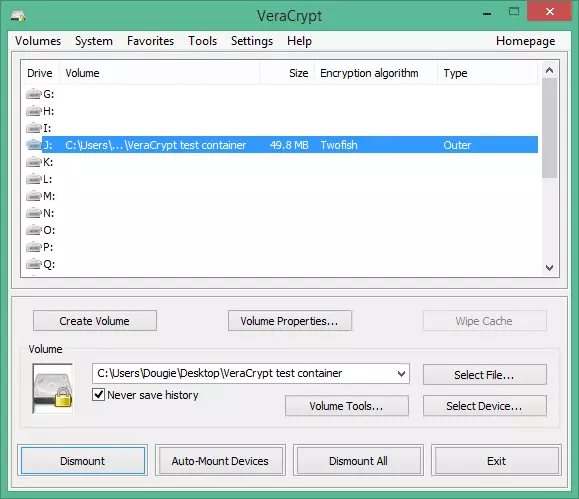
- … the drive type is listed as ‘Outer(!)’ in the VeraCrypt main screen, and if you look in the volume properties (right-click -> Properties) you will see ‘Hidden Volume Protected’ has the ‘Yes (damage prevented)’ value.
![VCH18]() Note that you can only see this if you opted to protect the data on your hidden volume when you mounted it. If you mount the volume normally using just the outer volume password (as you should if asked to mount it by an adversary), the ‘Type’ value would simply show ‘Normal’
Note that you can only see this if you opted to protect the data on your hidden volume when you mounted it. If you mount the volume normally using just the outer volume password (as you should if asked to mount it by an adversary), the ‘Type’ value would simply show ‘Normal’
The volume can be remounted and used as normal, but if you have written to the hidden volume area, data on the outer drive may be corrupted. In this case it is best to create a new VeraCrypt volume and copy your data across.
If possible then, try to not copy more data to the outer partition than there is room for!
Using a hidden volume
The procedure for opening a hidden volume is identical to that for opening a normal VeraCrypt volume (see VeraCrypt & how-to basics), except that instead of entering the password for the outer volume, you enter the password for the hidden volume.
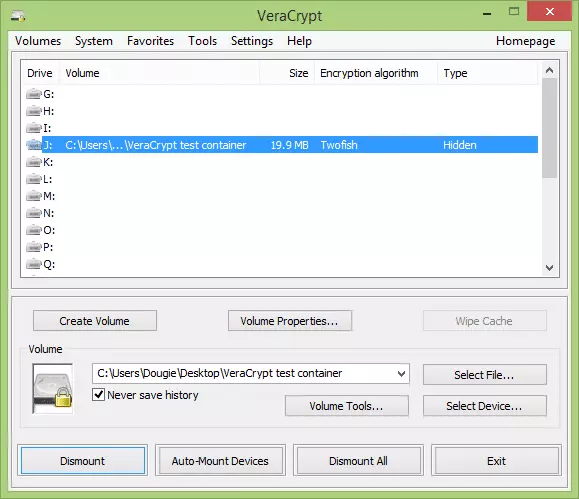
If you enter the password for the outer volume, the volume will appear to be a normal VeraCrypt volume.
A word on the dangers of VeraCrypt’s hidden volumes feature
In many ways the fact that VeraCrypt provides ‘plausible deniability’ is one of its greatest strengths, as it is impossible to prove that a hidden volume exists.In most situations, if an adversary (such as law enforcement officials) cannot prove that a volume exists due to lack of evidence, then there can be no case against you.
In the UK for example, you can be jailed for refusing to hand over encryption keys to data the police believe contains criminal content. However (at least at present), the police do have to demonstrate that some encrypted data exists that you have keys to. If there is no evidence that such data even exists, there is no case.
However, the flip side of this is that it is also impossible to prove that a hidden volume does not exist inside a VeraCrypt container. There are situations where the mere lack of proof that a volume actually exists will not deter an adversary who believes or suspects that it does, and in such situations the fact that any VeraCrypt container could potentially contain a hidden folder could be extremely dangerous.
Consider the situation in a country where the law provides no presumption of innocence, and the burden of proof lies with the accused. In such a situation, while an adversary may not be able to prove that a hidden volume exists, you could also not prove that it doesn’t, and so could consequently face jail or worse if the adversary felt you were hiding information (even if you were not).
A similar situation might exist for a Mafia whistleblower facing torture if he does not reveal the password to a suspected hidden volume. Without being able to prove that such volume does not exist, he could be in deep trouble.
A VeraCrypt hidden volume makes it impossible to know (and therefore prove) that hidden data exists, which is what lies at the heart of the concept of ‘plausible deniability’. The problem comes when you are dealing with an adversary who doesn’t care about proving the data exists, and will imprison or torture you simply on the grounds of suspicion.
In such a situation, using VeraCrypt to protect your files may be especially dangerous, since if no hidden volume actually exists then you can neither prove this to be the case, nor surrender the non-existent keys. If your adversary chooses not believe you, then you have nowhere to go…
A potential workaround
At least in theory*, one possible solution to this problem could be to create a hidden volume even if you do not plan to use it. In this way, should you decide that the consequences of revealing your VeraCrypt protected data outweigh the benefits of keeping it secret, you can also reveal your hidden container key to show that there is no further hidden data (only one hidden volume can be created in each VeraCrypt volume).
*Please note that this is a personal suggestion, and while we have run tests to confirm that only one hidden volume can exist in a VeraCrypt container (if you create a second, the first is deleted), the above idea is just that, and we take no responsibly on how events might play out in practice.
This is Part 2 of our look at VeraCrypt
If you haven't done so already, be sure to check out Part 1: VeraCyrpt & how-to basics. And if you want to learn more groovy VeraCrypt tricks, please see Create a Virtual Machine inside a VeraCrypt Hidden Volume.

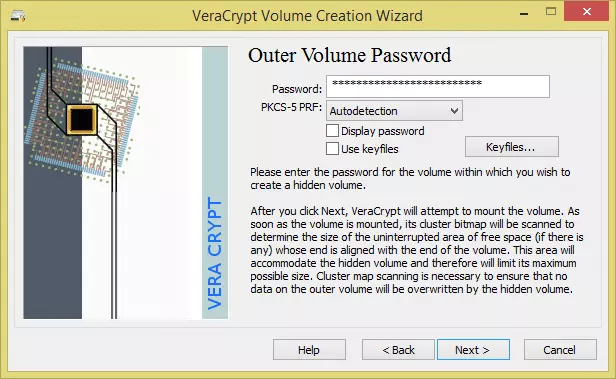
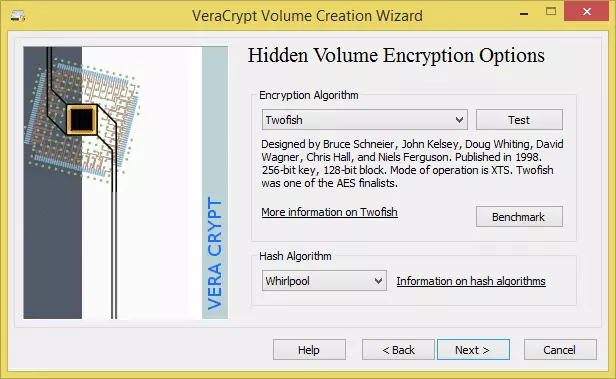 We will go with the same settings we chose for creating the outer volume (and for the same reasons)
We will go with the same settings we chose for creating the outer volume (and for the same reasons)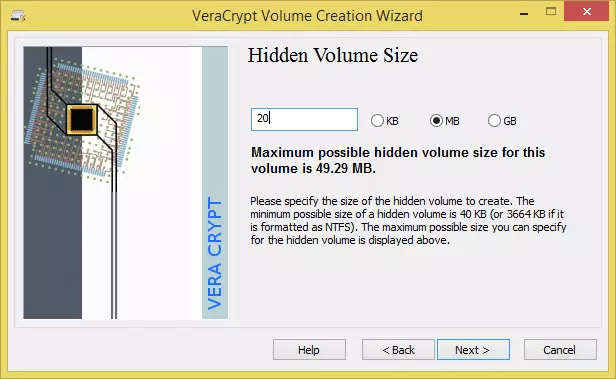 Our outer volume was 50MB, so we think 20MB is good size to hide our secret files in
Our outer volume was 50MB, so we think 20MB is good size to hide our secret files in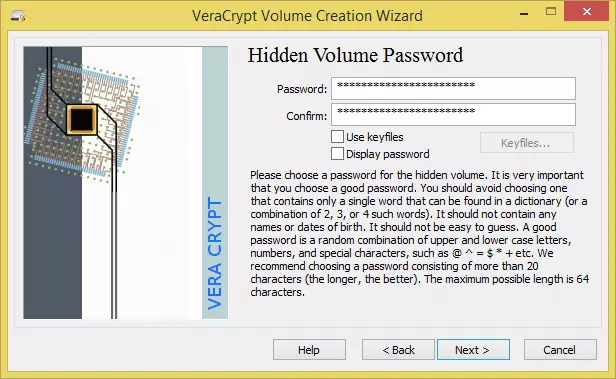
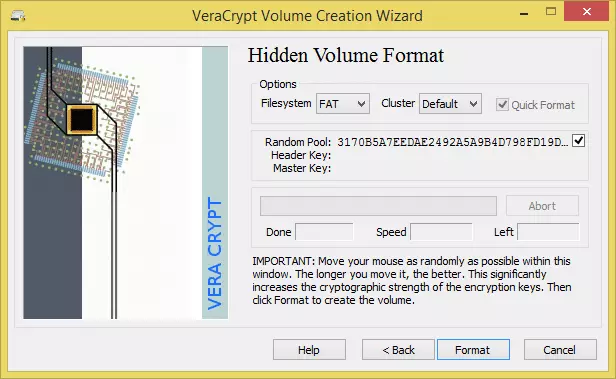 …and the hidden volume is created! Hit ‘OK’.
…and the hidden volume is created! Hit ‘OK’.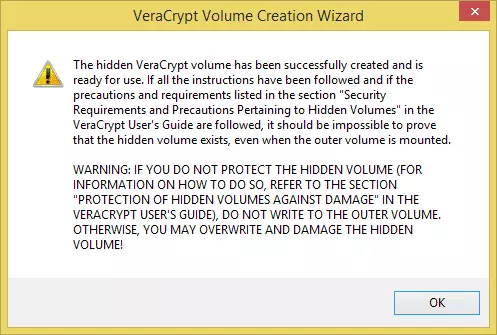
 Both passwords must be correct for this setting to work.
Both passwords must be correct for this setting to work.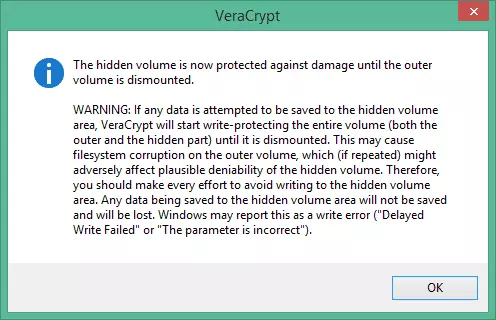
 Note that you can only see this if you opted to protect the data on your hidden volume when you mounted it. If you mount the volume normally using just the outer volume password (as you should if asked to mount it by an adversary), the ‘Type’ value would simply show ‘Normal’
Note that you can only see this if you opted to protect the data on your hidden volume when you mounted it. If you mount the volume normally using just the outer volume password (as you should if asked to mount it by an adversary), the ‘Type’ value would simply show ‘Normal’